Decentralized identity empowers individuals with control over their personal data using blockchain and cryptographic methods, minimizing reliance on centralized authorities and enhancing privacy. Zero Trust architecture enforces strict access controls by continuously verifying every user and device, assuming no implicit trust within the network perimeter. Explore how these innovative technologies reshape cybersecurity and identity management.
Why it is important
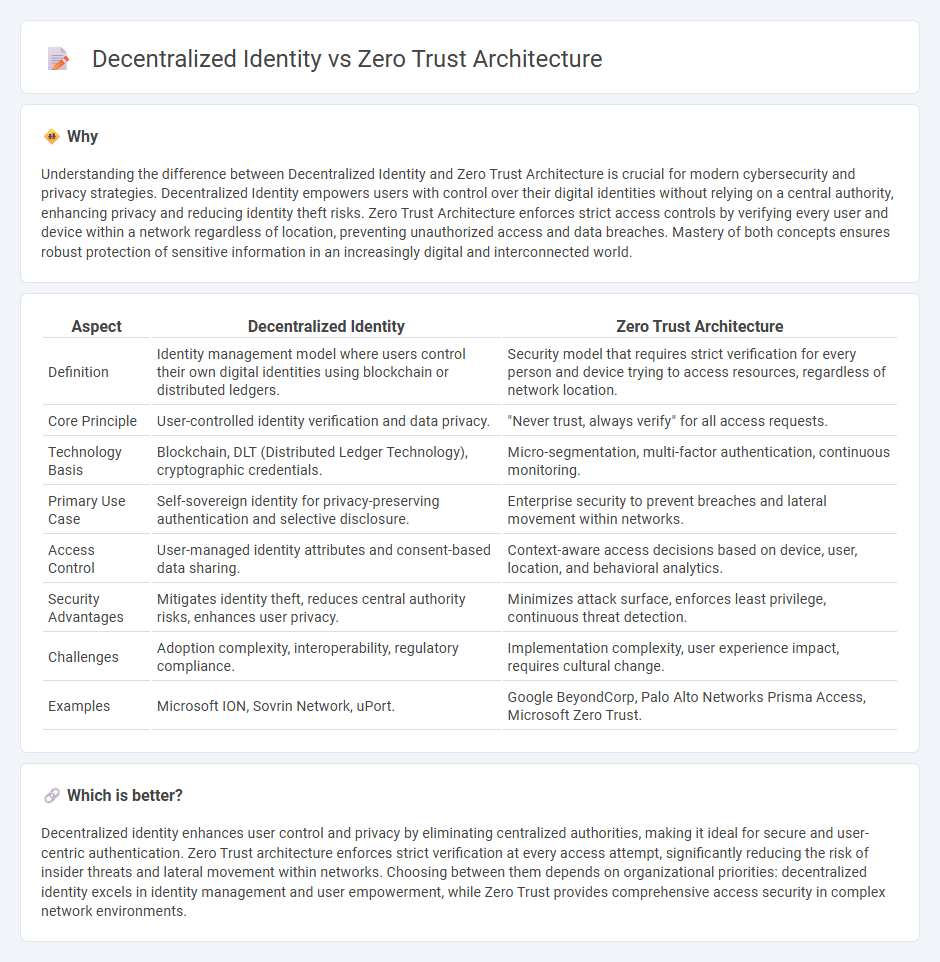
Understanding the difference between Decentralized Identity and Zero Trust Architecture is crucial for modern cybersecurity and privacy strategies. Decentralized Identity empowers users with control over their digital identities without relying on a central authority, enhancing privacy and reducing identity theft risks. Zero Trust Architecture enforces strict access controls by verifying every user and device within a network regardless of location, preventing unauthorized access and data breaches. Mastery of both concepts ensures robust protection of sensitive information in an increasingly digital and interconnected world.
Comparison Table
| Aspect | Decentralized Identity | Zero Trust Architecture |
|---|---|---|
| Definition | Identity management model where users control their own digital identities using blockchain or distributed ledgers. | Security model that requires strict verification for every person and device trying to access resources, regardless of network location. |
| Core Principle | User-controlled identity verification and data privacy. | "Never trust, always verify" for all access requests. |
| Technology Basis | Blockchain, DLT (Distributed Ledger Technology), cryptographic credentials. | Micro-segmentation, multi-factor authentication, continuous monitoring. |
| Primary Use Case | Self-sovereign identity for privacy-preserving authentication and selective disclosure. | Enterprise security to prevent breaches and lateral movement within networks. |
| Access Control | User-managed identity attributes and consent-based data sharing. | Context-aware access decisions based on device, user, location, and behavioral analytics. |
| Security Advantages | Mitigates identity theft, reduces central authority risks, enhances user privacy. | Minimizes attack surface, enforces least privilege, continuous threat detection. |
| Challenges | Adoption complexity, interoperability, regulatory compliance. | Implementation complexity, user experience impact, requires cultural change. |
| Examples | Microsoft ION, Sovrin Network, uPort. | Google BeyondCorp, Palo Alto Networks Prisma Access, Microsoft Zero Trust. |
Which is better?
Decentralized identity enhances user control and privacy by eliminating centralized authorities, making it ideal for secure and user-centric authentication. Zero Trust architecture enforces strict verification at every access attempt, significantly reducing the risk of insider threats and lateral movement within networks. Choosing between them depends on organizational priorities: decentralized identity excels in identity management and user empowerment, while Zero Trust provides comprehensive access security in complex network environments.
Connection
Decentralized identity enhances Zero Trust architecture by enabling users to control their digital identities through cryptographic proofs rather than relying on centralized authorities. Zero Trust relies on continuous verification of user credentials and device integrity, which decentralized identity supports by providing tamper-proof, verifiable credentials. Together, they reduce single points of failure and strengthen security frameworks by ensuring trust is established dynamically and transparently.
Key Terms
Least Privilege Access
Zero Trust architecture enforces Least Privilege Access by continuously verifying user credentials and device health, minimizing access rights to only what is necessary for each session. Decentralized identity empowers users with control over their credentials, enabling selective disclosure and reducing reliance on centralized authorities while still adhering to least privilege principles. Explore more to understand how combining these approaches enhances security frameworks effectively.
Self-Sovereign Identity
Zero Trust architecture enhances security by continuously verifying user identities and device states without relying on perimeter-based controls. Decentralized identity, particularly Self-Sovereign Identity (SSI), empowers individuals to own, control, and share their digital identities without centralized authorities, improving privacy and reducing data breaches. Explore how integrating Zero Trust principles with SSI can revolutionize digital identity management and security.
Trust Anchor
Zero Trust architecture relies on continuous verification of user and device identity, using a centralized Trust Anchor to validate credentials and enforce access policies. Decentralized identity shifts this model by distributing the Trust Anchor across multiple independent entities, empowering users with control over their digital identities and reducing single points of failure. Explore deeper insights into how Trust Anchors redefine security in Zero Trust and Decentralized Identity frameworks.
Source and External Links
Zero trust architecture - Wikipedia - Zero Trust Architecture (ZTA) is an IT system design that enforces no implicit trust for users or devices, requiring identity verification, device compliance checks, and least privilege access to resources regardless of network location, shifting away from traditional network perimeter security models.
What Is a Zero Trust Architecture? - Zscaler - Zero Trust Architecture transforms security by governing access based on context and risk, verifying identities, assessing risk via AI/ML, and enforcing least-privilege access policies in real time, effectively decoupling security from the network itself.
Zero Trust Architecture - NIST Technical Series Publications - NIST defines ZTA as a cybersecurity architecture that prevents data breaches and limits lateral movement by implementing core logical components like policy engines and segregated control and data planes to dynamically assess access requests based on enterprise policies and external threat intelligence.
 dowidth.com
dowidth.com