Post-quantum cryptography focuses on developing encryption algorithms resistant to attacks from quantum computers, ensuring data security in the quantum era. Hash-based cryptography relies on cryptographic hash functions to create secure digital signatures, offering strong resistance to quantum attacks with well-established mathematical foundations. Explore the differences and advantages of these cutting-edge cryptographic approaches to safeguard future communications.
Why it is important
Understanding the difference between Post-quantum cryptography and Hash-based cryptography is crucial for safeguarding data against quantum computing threats and ensuring long-term digital security. Post-quantum cryptography focuses on algorithms resistant to quantum attacks, while Hash-based cryptography leverages hash functions to secure data integrity and authenticity. Selecting the appropriate cryptographic method impacts the robustness and future-proofing of encrypted communications. This knowledge is essential for cybersecurity professionals developing encryption systems in the era of advancing quantum technologies.
Comparison Table
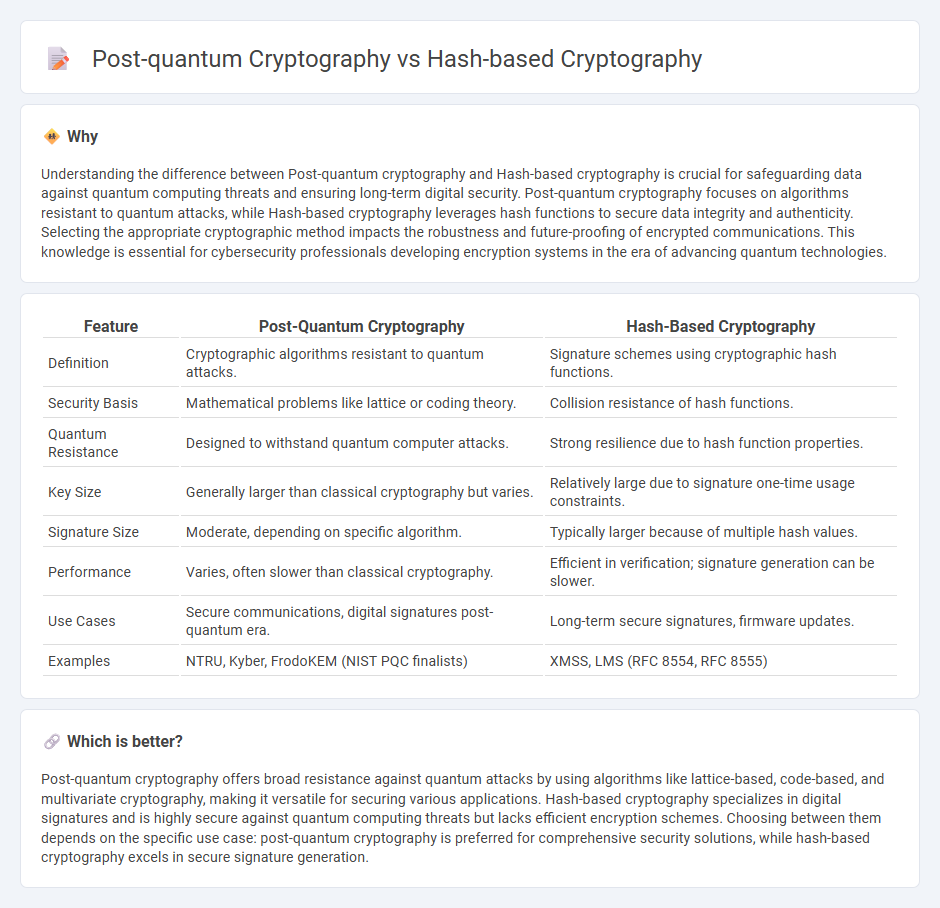
| Feature | Post-Quantum Cryptography | Hash-Based Cryptography |
|---|---|---|
| Definition | Cryptographic algorithms resistant to quantum attacks. | Signature schemes using cryptographic hash functions. |
| Security Basis | Mathematical problems like lattice or coding theory. | Collision resistance of hash functions. |
| Quantum Resistance | Designed to withstand quantum computer attacks. | Strong resilience due to hash function properties. |
| Key Size | Generally larger than classical cryptography but varies. | Relatively large due to signature one-time usage constraints. |
| Signature Size | Moderate, depending on specific algorithm. | Typically larger because of multiple hash values. |
| Performance | Varies, often slower than classical cryptography. | Efficient in verification; signature generation can be slower. |
| Use Cases | Secure communications, digital signatures post-quantum era. | Long-term secure signatures, firmware updates. |
| Examples | NTRU, Kyber, FrodoKEM (NIST PQC finalists) | XMSS, LMS (RFC 8554, RFC 8555) |
Which is better?
Post-quantum cryptography offers broad resistance against quantum attacks by using algorithms like lattice-based, code-based, and multivariate cryptography, making it versatile for securing various applications. Hash-based cryptography specializes in digital signatures and is highly secure against quantum computing threats but lacks efficient encryption schemes. Choosing between them depends on the specific use case: post-quantum cryptography is preferred for comprehensive security solutions, while hash-based cryptography excels in secure signature generation.
Connection
Post-quantum cryptography and hash-based cryptography are connected through their focus on ensuring data security against quantum computing attacks. Hash-based cryptography utilizes cryptographic hash functions to create digital signatures resistant to quantum algorithms like Shor's algorithm. This makes hash-based methods a crucial component in the development of post-quantum cryptographic standards.
Key Terms
One-Time Signatures
One-Time Signatures (OTS) represent a critical component in hash-based cryptography, offering strong security guarantees by relying solely on cryptographic hash functions resistant to quantum attacks. Unlike other post-quantum cryptographic schemes, hash-based OTS schemes, such as the Lamport signature, provide quantum-resistant digital signatures with simple, well-understood security premises but require careful management of single-use key pairs. Explore the practical applications and security benefits of one-time signatures within post-quantum cryptography frameworks to enhance your understanding.
Lattice-Based Cryptography
Lattice-based cryptography offers robust resistance against quantum attacks, leveraging the hardness of lattice problems like Learning With Errors (LWE) and Shortest Vector Problem (SVP) as foundational structures. In contrast to traditional hash-based cryptography, which primarily secures digital signatures using hash functions, lattice-based schemes provide both encryption and signature capabilities with strong theoretical security guarantees against quantum adversaries. Explore the advancements in lattice-based cryptography to understand its critical role within the broader landscape of post-quantum cryptographic solutions.
Quantum Resistance
Hash-based cryptography leverages the security of hash functions to provide strong quantum resistance, making it a prime candidate within post-quantum cryptography (PQC) protocols designed to withstand attacks from quantum computers. Unlike traditional cryptographic schemes vulnerable to quantum algorithms like Shor's, hash-based methods remain secure due to the hardness of preimage and collision resistance properties of modern hash functions. Explore the latest developments and practical implementations in hash-based post-quantum cryptography to better understand its role in securing future digital communications.
Source and External Links
Hash-based cryptography - Wikipedia - Hash-based cryptography is a category of cryptographic primitives that rely on the security of hash functions and is considered a leading candidate for post-quantum digital signatures and integrity proofs.
Post-quantum cryptography: Hash-based signatures - Red Hat - Hash-based signatures use hash functions to produce secure, quantum-resistant digital signatures by revealing a preimage as a signature that can be verified against a published hash of the secret value.
Hash-based Signatures: An illustrated Primer - Classic hash-based schemes, such as the Lamport signature, sign messages by exposing a unique secret for each bit, which must be verified by hashing and comparing with a public key, making them simple but requiring large keys for security.
 dowidth.com
dowidth.com