Zero Trust Architecture (ZTA) enforces strict identity verification for every user and device attempting to access resources, minimizing the risk of unauthorized access. Virtual Private Network (VPN) creates an encrypted tunnel to secure data transmission but often relies on perimeter-based security models vulnerable to internal threats. Explore how these technologies redefine cybersecurity by visiting our detailed comparison.
Why it is important
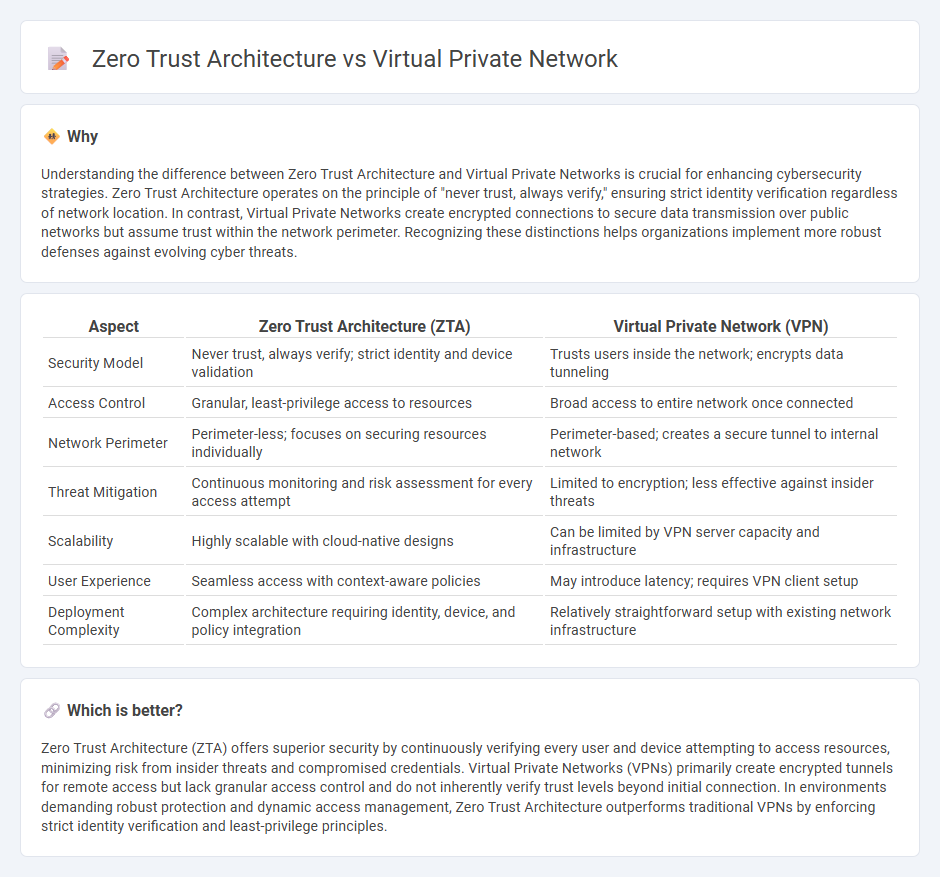
Understanding the difference between Zero Trust Architecture and Virtual Private Networks is crucial for enhancing cybersecurity strategies. Zero Trust Architecture operates on the principle of "never trust, always verify," ensuring strict identity verification regardless of network location. In contrast, Virtual Private Networks create encrypted connections to secure data transmission over public networks but assume trust within the network perimeter. Recognizing these distinctions helps organizations implement more robust defenses against evolving cyber threats.
Comparison Table
| Aspect | Zero Trust Architecture (ZTA) | Virtual Private Network (VPN) |
|---|---|---|
| Security Model | Never trust, always verify; strict identity and device validation | Trusts users inside the network; encrypts data tunneling |
| Access Control | Granular, least-privilege access to resources | Broad access to entire network once connected |
| Network Perimeter | Perimeter-less; focuses on securing resources individually | Perimeter-based; creates a secure tunnel to internal network |
| Threat Mitigation | Continuous monitoring and risk assessment for every access attempt | Limited to encryption; less effective against insider threats |
| Scalability | Highly scalable with cloud-native designs | Can be limited by VPN server capacity and infrastructure |
| User Experience | Seamless access with context-aware policies | May introduce latency; requires VPN client setup |
| Deployment Complexity | Complex architecture requiring identity, device, and policy integration | Relatively straightforward setup with existing network infrastructure |
Which is better?
Zero Trust Architecture (ZTA) offers superior security by continuously verifying every user and device attempting to access resources, minimizing risk from insider threats and compromised credentials. Virtual Private Networks (VPNs) primarily create encrypted tunnels for remote access but lack granular access control and do not inherently verify trust levels beyond initial connection. In environments demanding robust protection and dynamic access management, Zero Trust Architecture outperforms traditional VPNs by enforcing strict identity verification and least-privilege principles.
Connection
Zero Trust Architecture (ZTA) and Virtual Private Networks (VPNs) are interconnected through their shared goal of enhancing network security by verifying user authenticity and enforcing strict access controls. ZTA eliminates implicit trust by continuously validating users and devices, while VPNs create encrypted tunnels that protect data in transit from potential threats. Together, they form a comprehensive security strategy that ensures secure, authenticated connections both inside and outside traditional network perimeters.
Key Terms
Encryption
Virtual Private Network (VPN) encrypts data traffic between the user and the VPN server, ensuring secure remote access by creating a private tunnel over public networks. Zero Trust Architecture (ZTA) implements continuous encryption and strict access controls at every stage of data interaction, verifying and encrypting data regardless of network location to prevent unauthorized access. Explore deeper insights into how encryption strategies differ between VPN and Zero Trust models.
Authentication
Virtual Private Network (VPN) relies on perimeter-based security, granting access once users authenticate through shared credentials, often leading to broad and implicit trust within the network. Zero Trust Architecture (ZTA) enforces strict identity verification using multi-factor authentication (MFA) and continuous validation of user and device permissions before granting access to specific resources. Explore how integrating Zero Trust principles can enhance authentication protocols beyond traditional VPN solutions.
Network Segmentation
Virtual Private Network (VPN) creates secure tunnels between remote users and a network, offering basic network segmentation by isolating traffic within those tunnels, but it inherently trusts all users once inside the network perimeter. Zero Trust Architecture enforces granular network segmentation by continuously verifying every user and device, regardless of location, minimizing lateral movement and potential breaches. Explore the detailed differences between VPN and Zero Trust Architecture to enhance your network security strategy.
Source and External Links
Virtual private network - A network architecture that extends a private network across public networks, enabling secure data transmission through encryption and tunneling protocols.
What is a VPN? - A service that encrypts internet traffic and protects online identity by creating a secure connection between devices and VPN servers.
What is a VPN? - A private network connection that allows safe and anonymous data transmission over the internet by masking IP addresses and encrypting data.
 dowidth.com
dowidth.com