Quantum key distribution (QKD) enables ultra-secure communication by leveraging quantum mechanics to generate encryption keys, ensuring eavesdropping attempts are detectable. Trusted Platform Module (TPM) is a hardware-based security solution that provides cryptographic functions and secure key storage to protect device integrity. Discover more about how QKD and TPM redefine digital security landscapes.
Why it is important
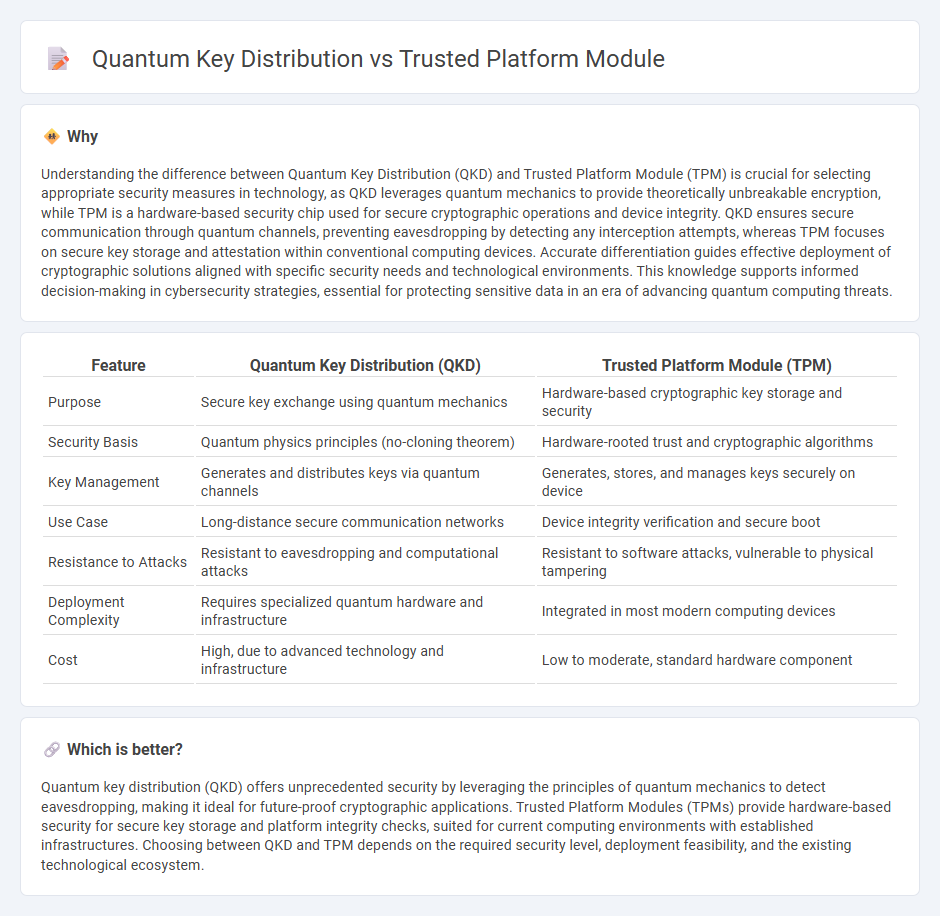
Understanding the difference between Quantum Key Distribution (QKD) and Trusted Platform Module (TPM) is crucial for selecting appropriate security measures in technology, as QKD leverages quantum mechanics to provide theoretically unbreakable encryption, while TPM is a hardware-based security chip used for secure cryptographic operations and device integrity. QKD ensures secure communication through quantum channels, preventing eavesdropping by detecting any interception attempts, whereas TPM focuses on secure key storage and attestation within conventional computing devices. Accurate differentiation guides effective deployment of cryptographic solutions aligned with specific security needs and technological environments. This knowledge supports informed decision-making in cybersecurity strategies, essential for protecting sensitive data in an era of advancing quantum computing threats.
Comparison Table
| Feature | Quantum Key Distribution (QKD) | Trusted Platform Module (TPM) |
|---|---|---|
| Purpose | Secure key exchange using quantum mechanics | Hardware-based cryptographic key storage and security |
| Security Basis | Quantum physics principles (no-cloning theorem) | Hardware-rooted trust and cryptographic algorithms |
| Key Management | Generates and distributes keys via quantum channels | Generates, stores, and manages keys securely on device |
| Use Case | Long-distance secure communication networks | Device integrity verification and secure boot |
| Resistance to Attacks | Resistant to eavesdropping and computational attacks | Resistant to software attacks, vulnerable to physical tampering |
| Deployment Complexity | Requires specialized quantum hardware and infrastructure | Integrated in most modern computing devices |
| Cost | High, due to advanced technology and infrastructure | Low to moderate, standard hardware component |
Which is better?
Quantum key distribution (QKD) offers unprecedented security by leveraging the principles of quantum mechanics to detect eavesdropping, making it ideal for future-proof cryptographic applications. Trusted Platform Modules (TPMs) provide hardware-based security for secure key storage and platform integrity checks, suited for current computing environments with established infrastructures. Choosing between QKD and TPM depends on the required security level, deployment feasibility, and the existing technological ecosystem.
Connection
Quantum key distribution (QKD) enhances cryptographic security by enabling the generation and sharing of encryption keys based on quantum mechanics, preventing eavesdropping. Trusted Platform Modules (TPMs) provide hardware-based security by securely storing cryptographic keys and performing cryptographic operations within a tamper-resistant environment. The connection lies in their synergy: TPMs can securely manage and store keys generated through QKD protocols, integrating quantum-secured keys into practical computing devices for robust end-to-end security.
Key Terms
Hardware Security Module (Trusted Platform Module)
Trusted Platform Module (TPM) is a specialized hardware security module designed to securely store cryptographic keys, perform platform authentication, and ensure hardware integrity through secure boot processes. Unlike Quantum Key Distribution (QKD), which relies on principles of quantum mechanics for secure communication, TPM provides a practical and widely deployed solution for hardware-based cryptographic operations in everyday computing environments. Explore further to understand how TPM enhances hardware security in comparison to emerging quantum cryptography methods.
Quantum Entanglement (Quantum Key Distribution)
Quantum entanglement is a fundamental principle underpinning Quantum Key Distribution (QKD), enabling secure communication by generating shared, identical cryptographic keys between distant parties with unbreakable encryption due to the laws of quantum mechanics. Trusted Platform Module (TPM) relies on classical cryptographic techniques and hardware-based security anchors that lack the intrinsic quantum properties ensuring absolute secrecy inherent in QKD protocols. Discover how harnessing quantum entanglement in QKD surpasses traditional TPM security by exploring its unique advantages and future potential.
Cryptographic Key Management
Trusted Platform Module (TPM) provides hardware-based security for cryptographic key management by securely generating, storing, and limiting the use of cryptographic keys within a dedicated chip, ensuring robust protection against software attacks. Quantum Key Distribution (QKD) leverages quantum mechanics principles to enable ultra-secure key exchange by detecting any eavesdropping attempts, thus enhancing key distribution security over potentially compromised communication channels. Explore the detailed comparison of TPM and QKD to understand their distinct roles and applications in modern cryptographic key management.
Source and External Links
Trusted Platform Module Technology Overview - Learn Microsoft - The Trusted Platform Module (TPM) is a hardware-based security chip that performs cryptographic operations, stores cryptographic keys securely, and helps validate platform integrity during the boot process to protect against tampering and unauthorized access.
What Is a Trusted Platform Module (TPM)? - Intel - TPM is a microcontroller embedded on a device's motherboard used for securely storing critical information like encryption keys and credentials to ensure the device boots safely and authenticates itself against hardware and software attacks.
What's a Trusted Platform Module (TPM)? - Microsoft Support - A TPM is a specialized chip designed to securely store cryptographic keys and verify system integrity, used by features such as Windows Hello for biometric security and BitLocker for disk encryption to protect user data even if the device is lost or stolen.
 dowidth.com
dowidth.com