Zero-knowledge proofs (ZKPs) enable one party to prove the truth of a statement without revealing any additional information, enhancing privacy in blockchain and cryptographic applications. Trusted Execution Environments (TEEs) provide secure hardware-based enclaves to execute code and protect sensitive data from external access or tampering. Explore the differences and use cases of ZKPs and TEEs to understand their roles in advancing secure technology.
Why it is important
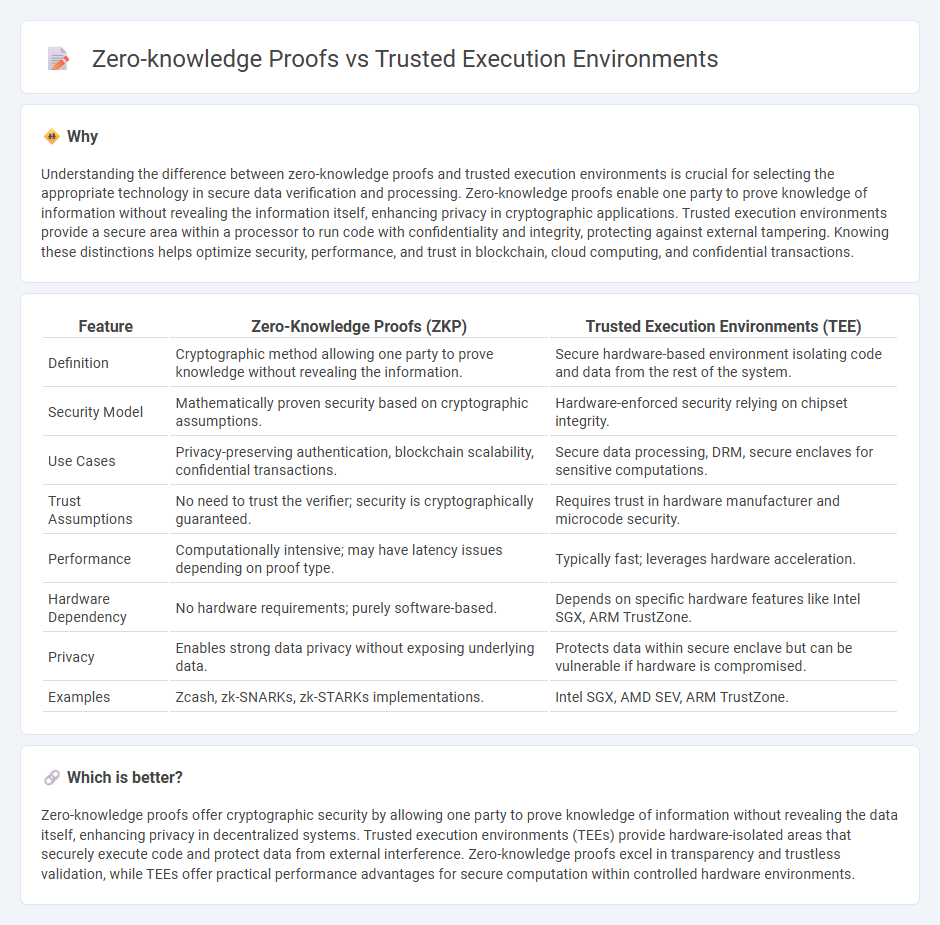
Understanding the difference between zero-knowledge proofs and trusted execution environments is crucial for selecting the appropriate technology in secure data verification and processing. Zero-knowledge proofs enable one party to prove knowledge of information without revealing the information itself, enhancing privacy in cryptographic applications. Trusted execution environments provide a secure area within a processor to run code with confidentiality and integrity, protecting against external tampering. Knowing these distinctions helps optimize security, performance, and trust in blockchain, cloud computing, and confidential transactions.
Comparison Table
| Feature | Zero-Knowledge Proofs (ZKP) | Trusted Execution Environments (TEE) |
|---|---|---|
| Definition | Cryptographic method allowing one party to prove knowledge without revealing the information. | Secure hardware-based environment isolating code and data from the rest of the system. |
| Security Model | Mathematically proven security based on cryptographic assumptions. | Hardware-enforced security relying on chipset integrity. |
| Use Cases | Privacy-preserving authentication, blockchain scalability, confidential transactions. | Secure data processing, DRM, secure enclaves for sensitive computations. |
| Trust Assumptions | No need to trust the verifier; security is cryptographically guaranteed. | Requires trust in hardware manufacturer and microcode security. |
| Performance | Computationally intensive; may have latency issues depending on proof type. | Typically fast; leverages hardware acceleration. |
| Hardware Dependency | No hardware requirements; purely software-based. | Depends on specific hardware features like Intel SGX, ARM TrustZone. |
| Privacy | Enables strong data privacy without exposing underlying data. | Protects data within secure enclave but can be vulnerable if hardware is compromised. |
| Examples | Zcash, zk-SNARKs, zk-STARKs implementations. | Intel SGX, AMD SEV, ARM TrustZone. |
Which is better?
Zero-knowledge proofs offer cryptographic security by allowing one party to prove knowledge of information without revealing the data itself, enhancing privacy in decentralized systems. Trusted execution environments (TEEs) provide hardware-isolated areas that securely execute code and protect data from external interference. Zero-knowledge proofs excel in transparency and trustless validation, while TEEs offer practical performance advantages for secure computation within controlled hardware environments.
Connection
Zero-knowledge proofs enable one party to prove knowledge of information without revealing the data itself, enhancing privacy in digital transactions. Trusted execution environments (TEEs) provide secure areas within processors that protect code and data from unauthorized access during execution, establishing a hardware-based security foundation. The intersection of zero-knowledge proofs and TEEs results in robust systems where sensitive computations are both verifiably correct and executed in isolated, tamper-resistant environments, strengthening overall trust and confidentiality.
Key Terms
Hardware Enclave (Trusted Execution Environments)
Trusted Execution Environments (TEEs), particularly Hardware Enclaves, provide a secure area within a processor that isolates sensitive computations from the rest of the system, ensuring data confidentiality and integrity even in compromised environments. Zero-Knowledge Proofs (ZKPs) offer cryptographic methods for one party to prove knowledge of information without revealing the data itself, enhancing privacy but relying on complex mathematical protocols rather than hardware. Explore how Hardware Enclaves in TEEs compare to ZKPs in securing sensitive operations and maintaining data privacy.
Attestation (Trusted Execution Environments)
Trusted Execution Environments (TEEs) provide hardware-based attestation by generating cryptographic proofs that verify the integrity and authenticity of the execution environment, ensuring that code runs in a secure, isolated space protected from external tampering. Zero-Knowledge Proofs (ZKPs), in contrast, offer cryptographic verification without revealing the underlying data but rely on mathematical constructs rather than hardware for attestation. Explore detailed comparisons on how TEE attestation mechanisms enhance secure computing and trust verification.
Cryptographic Proof (Zero-Knowledge Proofs)
Zero-Knowledge Proofs (ZKPs) enable one party to prove knowledge of specific information without revealing the data itself, leveraging sophisticated cryptographic algorithms to maintain privacy and integrity. Unlike Trusted Execution Environments (TEEs), which secure computations within isolated hardware, ZKPs provide cryptographic guarantees that computations and data remain confidential during verification on any platform. Explore detailed comparisons and implementation strategies to understand how ZKPs revolutionize secure verification processes.
Source and External Links
What are Trusted Execution Environments (TEE)? - AI21 Labs - A TEE is a secure area inside a computer processor that runs sensitive code and handles private data isolated from the main operating system, with its own Trusted OS and Trusted Applications, protecting operations even if the main system is compromised.
What is a Trusted Execution Environment? | TEE Technology - TEEs (also known as secure enclaves) isolate sensitive code and data execution from the main OS to protect confidentiality and integrity, using hardware-enforced isolation and encryption, commonly applied in secure mobile payments, DRM, and biometric authentication.
Trusted execution environment - Wikipedia - A TEE is a secure area of a main processor providing hardware-based memory encryption that isolates application code and data to protect confidentiality and integrity against unauthorized access or modification, offering stronger security than the main OS and more functionality than a secure element.
 dowidth.com
dowidth.com