Homomorphic encryption allows computations on encrypted data without revealing the underlying information, enhancing privacy in cloud computing and data analysis. Trusted Execution Environments (TEEs) provide isolated secure areas within processors to protect sensitive code and data from unauthorized access, ensuring data integrity during execution. Explore the differences and applications of homomorphic encryption and TEEs to understand their roles in advancing data security.
Why it is important
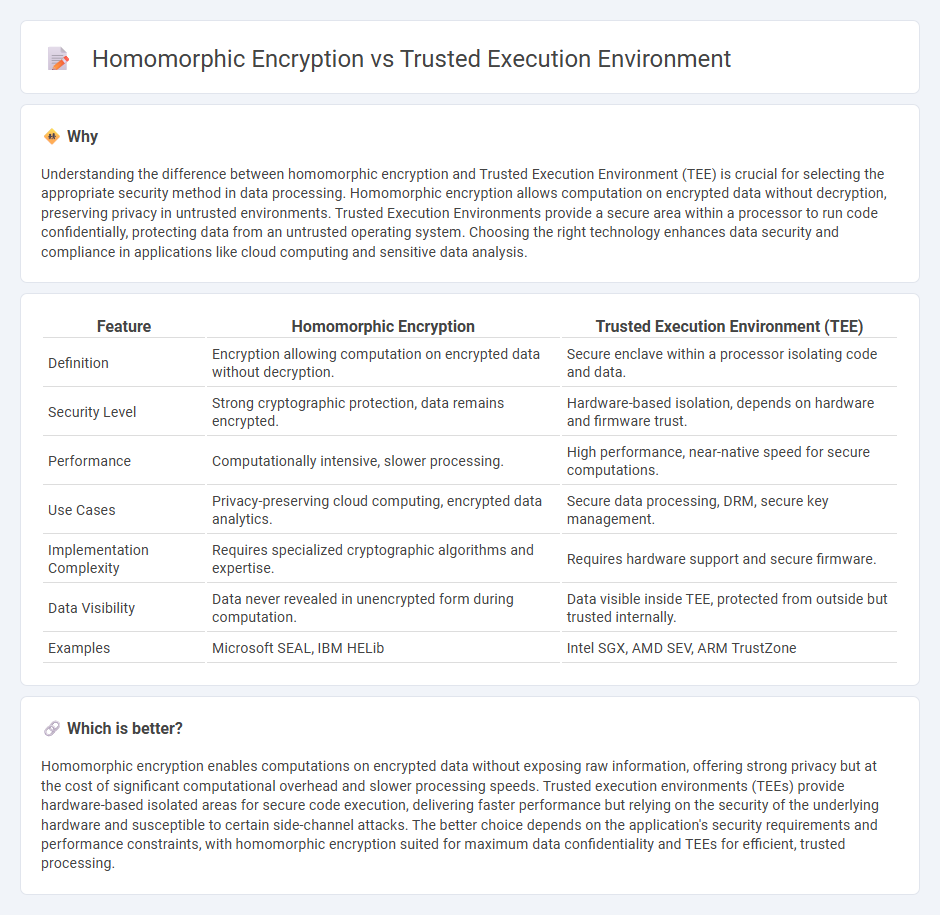
Understanding the difference between homomorphic encryption and Trusted Execution Environment (TEE) is crucial for selecting the appropriate security method in data processing. Homomorphic encryption allows computation on encrypted data without decryption, preserving privacy in untrusted environments. Trusted Execution Environments provide a secure area within a processor to run code confidentially, protecting data from an untrusted operating system. Choosing the right technology enhances data security and compliance in applications like cloud computing and sensitive data analysis.
Comparison Table
| Feature | Homomorphic Encryption | Trusted Execution Environment (TEE) |
|---|---|---|
| Definition | Encryption allowing computation on encrypted data without decryption. | Secure enclave within a processor isolating code and data. |
| Security Level | Strong cryptographic protection, data remains encrypted. | Hardware-based isolation, depends on hardware and firmware trust. |
| Performance | Computationally intensive, slower processing. | High performance, near-native speed for secure computations. |
| Use Cases | Privacy-preserving cloud computing, encrypted data analytics. | Secure data processing, DRM, secure key management. |
| Implementation Complexity | Requires specialized cryptographic algorithms and expertise. | Requires hardware support and secure firmware. |
| Data Visibility | Data never revealed in unencrypted form during computation. | Data visible inside TEE, protected from outside but trusted internally. |
| Examples | Microsoft SEAL, IBM HELib | Intel SGX, AMD SEV, ARM TrustZone |
Which is better?
Homomorphic encryption enables computations on encrypted data without exposing raw information, offering strong privacy but at the cost of significant computational overhead and slower processing speeds. Trusted execution environments (TEEs) provide hardware-based isolated areas for secure code execution, delivering faster performance but relying on the security of the underlying hardware and susceptible to certain side-channel attacks. The better choice depends on the application's security requirements and performance constraints, with homomorphic encryption suited for maximum data confidentiality and TEEs for efficient, trusted processing.
Connection
Homomorphic encryption and Trusted Execution Environments (TEEs) both enhance data security by enabling computation on sensitive information without exposing raw data. Homomorphic encryption allows computations to be performed on encrypted data, producing encrypted results that, once decrypted, match the outcome of operations on plaintext. TEEs provide a secure enclave within hardware, isolating code and data to prevent unauthorized access during processing, thus complementing homomorphic encryption in building robust privacy-preserving systems.
Key Terms
Secure Enclave
Secure Enclave provides a Trusted Execution Environment (TEE) that isolates sensitive computations and data from the main operating system, ensuring hardware-based security and minimizing exposure to attacks. Homomorphic encryption enables computation on encrypted data without decryption, preserving privacy but typically incurs significant computational overhead compared to the efficiency of Secure Enclave-based TEEs. Explore how Secure Enclave technology balances performance and security to protect critical applications in real-world scenarios.
Data Confidentiality
Trusted execution environments (TEEs) provide data confidentiality by isolating sensitive computations within secure hardware enclaves, ensuring that data remains protected from unauthorized access even during processing. Homomorphic encryption allows computations on encrypted data without decryption, preserving confidentiality but often with significant computational overhead. Explore the detailed trade-offs between TEEs and homomorphic encryption to determine the best approach for your data privacy needs.
Computation on Encrypted Data
Trusted execution environments (TEEs) provide a secure enclave within a processor to perform computation on decrypted data while maintaining confidentiality and integrity, ensuring minimal exposure to external threats. Homomorphic encryption enables direct computation on encrypted data without decryption, preserving data privacy but typically incurring higher computational overhead. Explore how these technologies compare in enabling secure computation on encrypted data to determine the best fit for your specific security needs.
Source and External Links
Trusted execution environment - Wikipedia - A Trusted Execution Environment (TEE) is a secure area of a main processor that protects code and data loaded inside it in terms of confidentiality and integrity through hardware-based memory encryption and isolated execution.
What Is Trusted Execution Environment (TEE) & How Does It Work? - TEEs ensure secure startup and only execute authorized code that is checked and isolated, attesting its trustworthy state and protecting its data from unauthorized access.
Introduction to Trusted Execution Environments | GlobalPlatform - The TEE is a secure processor area isolating trusted applications and data from the main operating system and other apps, providing confidentiality, authenticity, system integrity, and high-speed processing.
 dowidth.com
dowidth.com