Homomorphic encryption enables computation on encrypted data without decryption, preserving privacy in cloud computing and secure data analysis. Symmetric encryption, relying on a shared secret key for both encryption and decryption, offers faster processing but requires secure key management. Explore the distinct advantages and applications of these encryption methods to enhance your cybersecurity strategy.
Why it is important
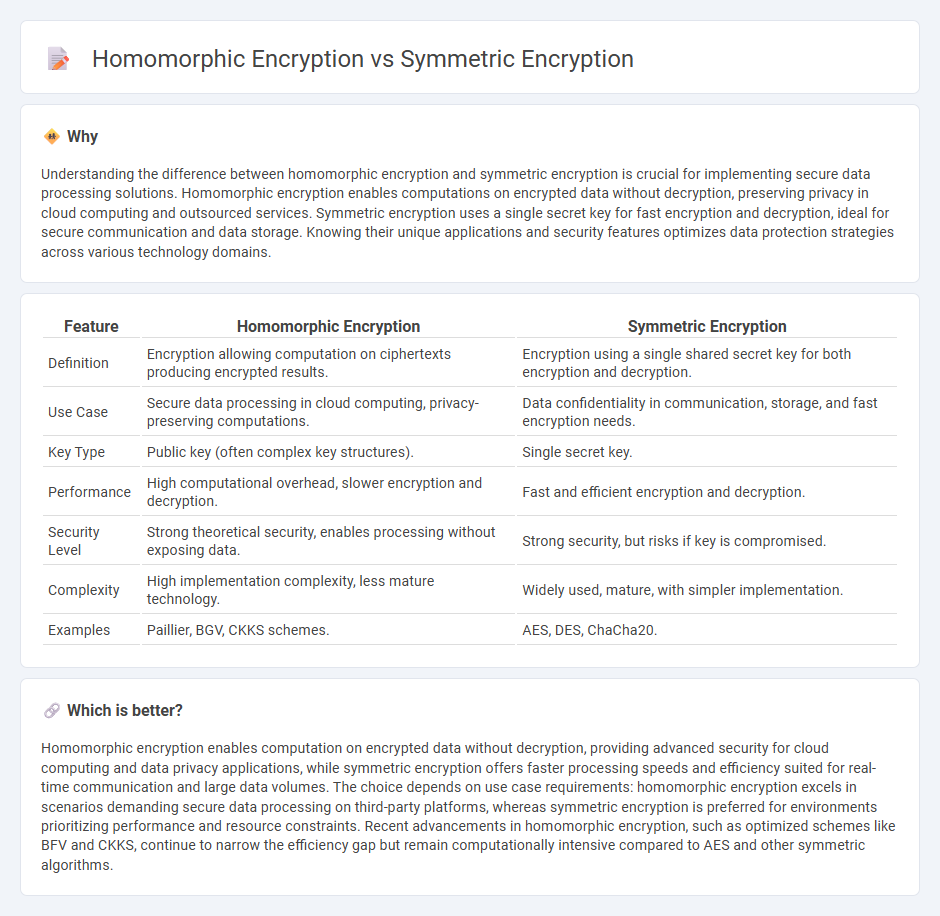
Understanding the difference between homomorphic encryption and symmetric encryption is crucial for implementing secure data processing solutions. Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy in cloud computing and outsourced services. Symmetric encryption uses a single secret key for fast encryption and decryption, ideal for secure communication and data storage. Knowing their unique applications and security features optimizes data protection strategies across various technology domains.
Comparison Table
| Feature | Homomorphic Encryption | Symmetric Encryption |
|---|---|---|
| Definition | Encryption allowing computation on ciphertexts producing encrypted results. | Encryption using a single shared secret key for both encryption and decryption. |
| Use Case | Secure data processing in cloud computing, privacy-preserving computations. | Data confidentiality in communication, storage, and fast encryption needs. |
| Key Type | Public key (often complex key structures). | Single secret key. |
| Performance | High computational overhead, slower encryption and decryption. | Fast and efficient encryption and decryption. |
| Security Level | Strong theoretical security, enables processing without exposing data. | Strong security, but risks if key is compromised. |
| Complexity | High implementation complexity, less mature technology. | Widely used, mature, with simpler implementation. |
| Examples | Paillier, BGV, CKKS schemes. | AES, DES, ChaCha20. |
Which is better?
Homomorphic encryption enables computation on encrypted data without decryption, providing advanced security for cloud computing and data privacy applications, while symmetric encryption offers faster processing speeds and efficiency suited for real-time communication and large data volumes. The choice depends on use case requirements: homomorphic encryption excels in scenarios demanding secure data processing on third-party platforms, whereas symmetric encryption is preferred for environments prioritizing performance and resource constraints. Recent advancements in homomorphic encryption, such as optimized schemes like BFV and CKKS, continue to narrow the efficiency gap but remain computationally intensive compared to AES and other symmetric algorithms.
Connection
Homomorphic encryption and symmetric encryption are connected through their shared goal of securing data, with homomorphic encryption enabling computations on encrypted data without decryption and symmetric encryption providing fast, efficient data protection using a single key. Both methods play crucial roles in modern cryptography, where homomorphic encryption extends functionality to privacy-preserving data processing while symmetric encryption ensures confidentiality and integrity in communication. Their integration is pivotal in developing secure systems for cloud computing and data privacy.
Key Terms
Key Management
Symmetric encryption uses a single secret key for both encryption and decryption, making key distribution and secure storage critical challenges in key management. Homomorphic encryption allows computations on encrypted data without revealing the key, simplifying key sharing in multi-party environments but requiring complex key generation and handling algorithms. Explore further to understand how these key management differences impact security and operational efficiency.
Data Privacy
Symmetric encryption uses a single secret key for both encryption and decryption, ensuring fast performance but requiring secure key management to maintain data privacy. Homomorphic encryption enables computations on encrypted data without revealing the plaintext, offering enhanced privacy for cloud computing and secure data analysis. Explore the differences and benefits of each method to strengthen your data privacy strategies.
Computation on Encrypted Data
Symmetric encryption ensures data confidentiality by using the same key for encryption and decryption, but it requires decryption before performing any computation, exposing plaintext during processing. Homomorphic encryption allows computations directly on encrypted data without decryption, preserving privacy while enabling complex data analysis and secure outsourced computation. Explore the advantages and applications of homomorphic encryption for secure data processing in cloud computing and privacy-preserving analytics.
Source and External Links
Symmetric-key algorithm - Symmetric encryption uses the same cryptographic key for both encrypting plaintext and decrypting ciphertext, enabling a shared secret to secure communication, and typically offers faster and more storage-efficient encryption compared to asymmetric methods.
What Is Symmetric Encryption? - Symmetric encryption relies on a single shared key for both encryption and decryption, offering efficient data protection but requiring secure key exchange and management to prevent unauthorized access.
What is Symmetric Encryption? - This technique transforms plaintext into ciphertext and back using one shared secret key, with the process involving key generation, key exchange, encryption, transmission/storage, and decryption steps based on symmetric encryption algorithms.
 dowidth.com
dowidth.com