Zero trust security models focus on verifying every access request without assuming trust based on network location, contrasting with traditional firewalls that primarily control access based on predefined network boundaries. Firewalls act as gatekeepers filtering incoming and outgoing traffic, while zero trust continuously monitors and authenticates users and devices regardless of their position within or outside the network. Explore the fundamental differences and strategic benefits of zero trust versus firewall approaches to enhance your cybersecurity knowledge.
Why it is important
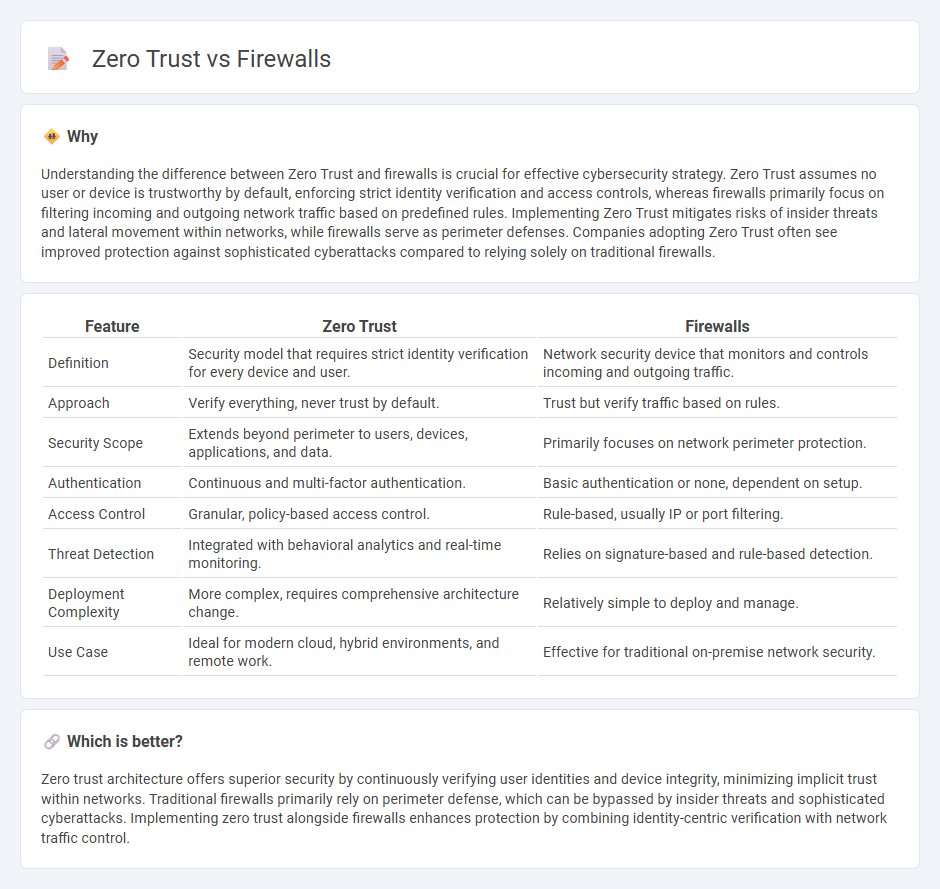
Understanding the difference between Zero Trust and firewalls is crucial for effective cybersecurity strategy. Zero Trust assumes no user or device is trustworthy by default, enforcing strict identity verification and access controls, whereas firewalls primarily focus on filtering incoming and outgoing network traffic based on predefined rules. Implementing Zero Trust mitigates risks of insider threats and lateral movement within networks, while firewalls serve as perimeter defenses. Companies adopting Zero Trust often see improved protection against sophisticated cyberattacks compared to relying solely on traditional firewalls.
Comparison Table
| Feature | Zero Trust | Firewalls |
|---|---|---|
| Definition | Security model that requires strict identity verification for every device and user. | Network security device that monitors and controls incoming and outgoing traffic. |
| Approach | Verify everything, never trust by default. | Trust but verify traffic based on rules. |
| Security Scope | Extends beyond perimeter to users, devices, applications, and data. | Primarily focuses on network perimeter protection. |
| Authentication | Continuous and multi-factor authentication. | Basic authentication or none, dependent on setup. |
| Access Control | Granular, policy-based access control. | Rule-based, usually IP or port filtering. |
| Threat Detection | Integrated with behavioral analytics and real-time monitoring. | Relies on signature-based and rule-based detection. |
| Deployment Complexity | More complex, requires comprehensive architecture change. | Relatively simple to deploy and manage. |
| Use Case | Ideal for modern cloud, hybrid environments, and remote work. | Effective for traditional on-premise network security. |
Which is better?
Zero trust architecture offers superior security by continuously verifying user identities and device integrity, minimizing implicit trust within networks. Traditional firewalls primarily rely on perimeter defense, which can be bypassed by insider threats and sophisticated cyberattacks. Implementing zero trust alongside firewalls enhances protection by combining identity-centric verification with network traffic control.
Connection
Zero trust architecture relies on continuous verification of all users and devices, ensuring strict access controls that traditional firewalls alone cannot enforce. Firewalls serve as critical components within a zero trust framework by segmenting networks and filtering traffic based on predefined security policies. Integrating advanced firewall capabilities with zero trust principles enhances threat detection and minimizes the risk of lateral movement within an organization's infrastructure.
Key Terms
Perimeter Security
Firewalls serve as traditional perimeter security tools that monitor and control incoming and outgoing network traffic based on predetermined security rules, effectively creating a defensive barrier between trusted internal networks and untrusted external environments. Zero Trust security models eliminate implicit trust by continuously verifying every user, device, and connection attempting to access resources, regardless of whether they are inside or outside the network perimeter, thereby addressing evolving cyber threats more dynamically. Discover how shifting from perimeter-centric firewalls to Zero Trust architectures can enhance your organization's overall cybersecurity posture.
Micro-Segmentation
Micro-segmentation plays a pivotal role in both firewalls and Zero Trust architectures by dividing networks into granular zones to control traffic flows and minimize attack surfaces. Firewalls traditionally enforce perimeter security policies, whereas Zero Trust employs micro-segmentation to continuously verify and restrict access within internal networks based on strict identity and context verification. Explore how micro-segmentation enhances security layers and supports modern Zero Trust models for robust cyber defense.
Least Privilege
Firewalls serve as perimeter defenses by filtering incoming and outgoing network traffic based on predetermined security rules, whereas Zero Trust emphasizes the principle of Least Privilege by continuously verifying user identity and granting minimal access necessary for tasks. Least Privilege reduces attack surfaces and limits the potential damage from compromised accounts by enforcing strict access controls at every level of the network and system. Explore how integrating Zero Trust strategies can enhance your security framework beyond traditional firewall protections.
Source and External Links
Types of Firewalls Defined and Explained - Firewalls are categorized by the system they protect, their form factor, network placement, and data filtering method, with network firewalls placed between trusted and untrusted networks to monitor and control traffic, and host-based firewalls installed on individual devices to filter harmful content.
What is a Firewall and Why Do I Need One? - A firewall is a network security device that prevents unauthorized access by inspecting all incoming and outgoing packets, using predefined rules to determine whether to allow or block traffic based on source, destination, port, and protocol information.
What Is a Firewall? - Firewalls serve as gatekeepers between internal and external networks, evaluating each network packet against security rules and only permitting safe traffic to pass, with next-generation firewalls offering advanced features like deep packet inspection, application control, and intrusion prevention.
 dowidth.com
dowidth.com