Trustless computing enables parties to execute transactions and computations without relying on a trusted intermediary, leveraging blockchain technology and decentralized protocols to ensure transparency and security. In contrast, secure multi-party computation (SMPC) allows multiple participants to jointly compute a function over their inputs while keeping those inputs private, using cryptographic techniques to prevent data leakage. Explore the key differences and applications of trustless computing and SMPC to understand their transformative impact on data security.
Why it is important
Understanding the difference between trustless computing and secure multi-party computation (SMPC) is crucial for implementing effective blockchain and privacy-preserving technologies. Trustless computing removes the need for a trusted third party by relying on cryptographic proofs, while SMPC enables multiple parties to jointly compute a function without revealing their private inputs. This knowledge ensures accurate application of each approach to enhance data security and collaboration in decentralized systems. Proper differentiation optimizes system design, balancing transparency and confidentiality in technology deployments.
Comparison Table
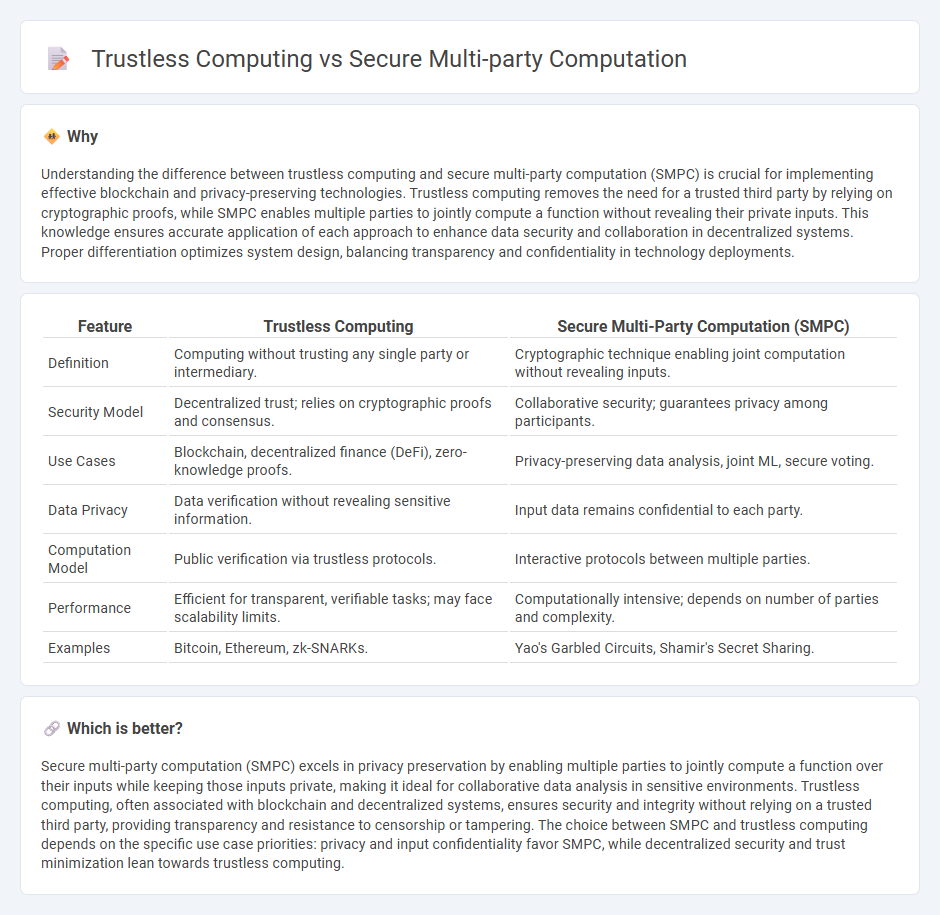
| Feature | Trustless Computing | Secure Multi-Party Computation (SMPC) |
|---|---|---|
| Definition | Computing without trusting any single party or intermediary. | Cryptographic technique enabling joint computation without revealing inputs. |
| Security Model | Decentralized trust; relies on cryptographic proofs and consensus. | Collaborative security; guarantees privacy among participants. |
| Use Cases | Blockchain, decentralized finance (DeFi), zero-knowledge proofs. | Privacy-preserving data analysis, joint ML, secure voting. |
| Data Privacy | Data verification without revealing sensitive information. | Input data remains confidential to each party. |
| Computation Model | Public verification via trustless protocols. | Interactive protocols between multiple parties. |
| Performance | Efficient for transparent, verifiable tasks; may face scalability limits. | Computationally intensive; depends on number of parties and complexity. |
| Examples | Bitcoin, Ethereum, zk-SNARKs. | Yao's Garbled Circuits, Shamir's Secret Sharing. |
Which is better?
Secure multi-party computation (SMPC) excels in privacy preservation by enabling multiple parties to jointly compute a function over their inputs while keeping those inputs private, making it ideal for collaborative data analysis in sensitive environments. Trustless computing, often associated with blockchain and decentralized systems, ensures security and integrity without relying on a trusted third party, providing transparency and resistance to censorship or tampering. The choice between SMPC and trustless computing depends on the specific use case priorities: privacy and input confidentiality favor SMPC, while decentralized security and trust minimization lean towards trustless computing.
Connection
Trustless computing enables secure collaboration without relying on a trusted third party by leveraging cryptographic protocols that ensure data privacy and integrity. Secure multi-party computation (SMPC) is a key technique within trustless computing that allows multiple parties to jointly compute a function over their inputs while keeping those inputs private. Both technologies enhance security and privacy in decentralized systems like blockchain and distributed cloud environments.
Key Terms
Cryptographic protocols
Secure multi-party computation (SMPC) enables multiple parties to jointly compute a function over their inputs while keeping those inputs private, relying heavily on cryptographic protocols like secret sharing and homomorphic encryption. Trustless computing emphasizes executing tasks without requiring mutual trust, often leveraging blockchain and zero-knowledge proofs to ensure correctness and privacy without revealing sensitive data. Explore detailed cryptographic mechanisms and use cases to deepen your understanding of how these paradigms revolutionize secure collaborative computation.
Zero-knowledge proofs
Zero-knowledge proofs enhance secure multi-party computation (MPC) by enabling participants to prove knowledge of a secret without revealing it, improving privacy and security in trustless environments. Trustless computing relies heavily on zero-knowledge proofs to verify transactions and computations without requiring mutual trust among parties, fostering decentralization and enhanced data integrity. Explore how zero-knowledge proofs transform security paradigms in both MPC and trustless computing frameworks.
Decentralization
Secure multi-party computation (SMPC) enables multiple parties to jointly compute a function over their inputs while keeping those inputs private, enhancing decentralization by distributing trust across participants without relying on a central authority. Trustless computing removes the need to trust any single party by leveraging blockchain technology and cryptographic proofs, creating a decentralized environment where computation and data integrity are verifiable by all network participants. Explore how these technologies transform decentralized systems and their implications for privacy and security.
Source and External Links
Secure multi-party computation - Wikipedia - Secure multi-party computation (MPC) is a cryptographic subfield focused on enabling multiple parties to jointly compute a function over their private inputs without revealing those inputs to each other, ensuring privacy among participants during computation.
What is Secure Multiparty Computation? - GeeksforGeeks - MPC allows secure computation on private data across multiple organizations without a trusted third party, preserving data privacy and producing accurate results while facing challenges like computational overhead and communication costs.
Secure Multi-Party Computation - Chainlink - SMPC enables joint computation on private data securely, ensuring confidentiality, regulatory compliance and quantum-safe protection, and supports advanced applications including cross-institution collaboration without exposing sensitive data.
 dowidth.com
dowidth.com