Trustless computing enables decentralized systems to operate without relying on mutual trust, leveraging cryptographic proofs and blockchain technology to ensure data integrity and transaction security. Secure enclaves offer hardware-based isolated environments that protect sensitive computations and data from unauthorized access and tampering within a device. Explore the key differences and applications of trustless computing versus secure enclaves to understand their roles in advancing cybersecurity.
Why it is important
Understanding the difference between trustless computing and secure enclave is crucial for selecting the right security model in technology applications. Trustless computing relies on cryptographic proofs and decentralized consensus to ensure data integrity without trusting any single party, vital for blockchain and decentralized systems. Secure enclaves provide a hardware-based trusted execution environment that safeguards sensitive data and code within a physically isolated area on a device, essential for protecting user privacy and preventing insider threats. Choosing the appropriate technology impacts the security, privacy, and scalability of digital systems in sectors like finance, healthcare, and IoT.
Comparison Table
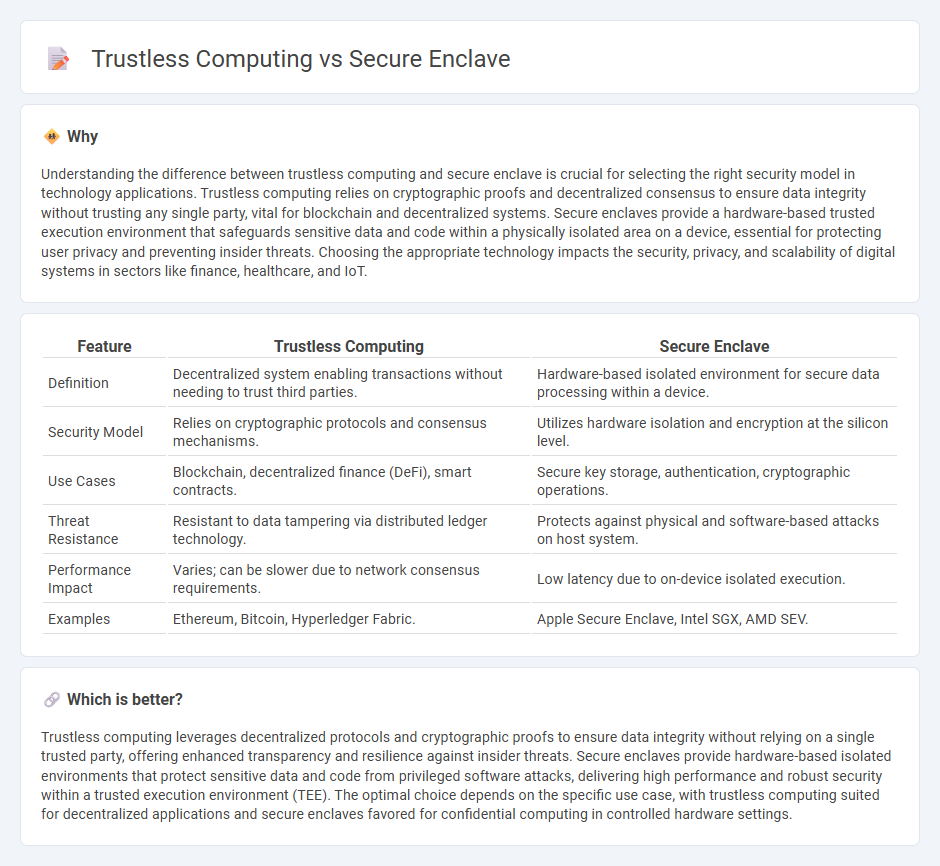
| Feature | Trustless Computing | Secure Enclave |
|---|---|---|
| Definition | Decentralized system enabling transactions without needing to trust third parties. | Hardware-based isolated environment for secure data processing within a device. |
| Security Model | Relies on cryptographic protocols and consensus mechanisms. | Utilizes hardware isolation and encryption at the silicon level. |
| Use Cases | Blockchain, decentralized finance (DeFi), smart contracts. | Secure key storage, authentication, cryptographic operations. |
| Threat Resistance | Resistant to data tampering via distributed ledger technology. | Protects against physical and software-based attacks on host system. |
| Performance Impact | Varies; can be slower due to network consensus requirements. | Low latency due to on-device isolated execution. |
| Examples | Ethereum, Bitcoin, Hyperledger Fabric. | Apple Secure Enclave, Intel SGX, AMD SEV. |
Which is better?
Trustless computing leverages decentralized protocols and cryptographic proofs to ensure data integrity without relying on a single trusted party, offering enhanced transparency and resilience against insider threats. Secure enclaves provide hardware-based isolated environments that protect sensitive data and code from privileged software attacks, delivering high performance and robust security within a trusted execution environment (TEE). The optimal choice depends on the specific use case, with trustless computing suited for decentralized applications and secure enclaves favored for confidential computing in controlled hardware settings.
Connection
Trustless computing enables secure data processing without relying on trusted third parties by using cryptographic methods and decentralized protocols. Secure enclaves, such as Intel SGX, provide hardware-based isolated environments that protect data and code integrity even from privileged system software. Together, they enhance security by combining cryptographic trust minimization with hardware-enforced confidentiality, enabling robust execution of sensitive applications.
Key Terms
Hardware-based isolation
Secure enclave technology relies on hardware-based isolation to create a protected execution environment within a device's processor, ensuring data confidentiality and integrity against unauthorized access. Trustless computing, often enabled by blockchain or distributed systems, emphasizes decentralized verification without depending on hardware isolation, focusing instead on cryptographic proofs and consensus mechanisms. Explore how hardware-based secure enclaves compare with trustless models to understand which approach best suits your security needs.
Cryptographic proofs
Secure enclaves provide a hardware-based environment that protects cryptographic keys and computations from external access, ensuring data confidentiality through isolated execution. Trustless computing relies on cryptographic proofs such as zero-knowledge proofs and consensus algorithms to verify computations without requiring trust in any single party. Explore the strengths and limitations of both approaches to better understand their roles in enhancing security in modern cryptographic applications.
Decentralization
Secure enclaves provide hardware-based protection by isolating sensitive computations within a trusted execution environment, enhancing confidentiality and integrity. Trustless computing leverages decentralized consensus mechanisms and cryptographic proofs to ensure system security without relying on a central authority, achieving true decentralization. Explore how these technologies impact blockchain scalability and privacy solutions.
Source and External Links
Secure Enclaves: The Powerful Way to Make Data Secure by Default - Secure enclaves are hardware-level, encrypted memory environments within CPUs that isolate and protect data and applications from both insiders and third parties, including those with root or physical access, by ensuring code and data are decrypted and accessible only within the enclave itself.
Secure Enclave - Apple Support - Apple's Secure Enclave is a dedicated, isolated hardware subsystem within its devices that handles sensitive operations like cryptographic key management, providing an additional layer of security even if the main processor is compromised.
What Is a Secure Enclave in WebAuthn? - The Secure Enclave is an Apple-specific hardware feature that generates and stores cryptographic keys separately from the main processor, primarily supporting NIST P-256 elliptic curve operations for enhanced security in authentication protocols like WebAuthn and passkeys.
 dowidth.com
dowidth.com