Trustless computing leverages decentralized networks and cryptographic protocols to eliminate reliance on trusted intermediaries, enhancing transparency and security in data processing. Secure boot is a hardware-based security standard that ensures a device boots using only software trusted by the manufacturer, preventing unauthorized code execution during startup. Explore the differences and applications of trustless computing and secure boot to understand their impact on modern cybersecurity.
Why it is important
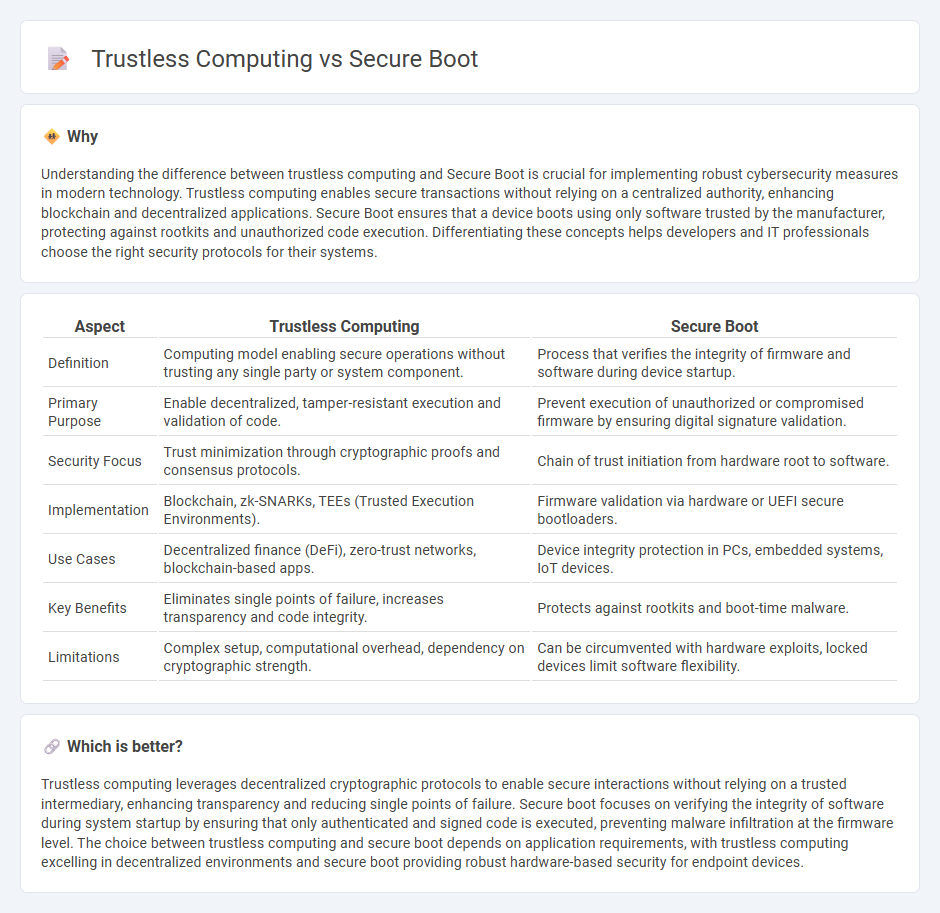
Understanding the difference between trustless computing and Secure Boot is crucial for implementing robust cybersecurity measures in modern technology. Trustless computing enables secure transactions without relying on a centralized authority, enhancing blockchain and decentralized applications. Secure Boot ensures that a device boots using only software trusted by the manufacturer, protecting against rootkits and unauthorized code execution. Differentiating these concepts helps developers and IT professionals choose the right security protocols for their systems.
Comparison Table
| Aspect | Trustless Computing | Secure Boot |
|---|---|---|
| Definition | Computing model enabling secure operations without trusting any single party or system component. | Process that verifies the integrity of firmware and software during device startup. |
| Primary Purpose | Enable decentralized, tamper-resistant execution and validation of code. | Prevent execution of unauthorized or compromised firmware by ensuring digital signature validation. |
| Security Focus | Trust minimization through cryptographic proofs and consensus protocols. | Chain of trust initiation from hardware root to software. |
| Implementation | Blockchain, zk-SNARKs, TEEs (Trusted Execution Environments). | Firmware validation via hardware or UEFI secure bootloaders. |
| Use Cases | Decentralized finance (DeFi), zero-trust networks, blockchain-based apps. | Device integrity protection in PCs, embedded systems, IoT devices. |
| Key Benefits | Eliminates single points of failure, increases transparency and code integrity. | Protects against rootkits and boot-time malware. |
| Limitations | Complex setup, computational overhead, dependency on cryptographic strength. | Can be circumvented with hardware exploits, locked devices limit software flexibility. |
Which is better?
Trustless computing leverages decentralized cryptographic protocols to enable secure interactions without relying on a trusted intermediary, enhancing transparency and reducing single points of failure. Secure boot focuses on verifying the integrity of software during system startup by ensuring that only authenticated and signed code is executed, preventing malware infiltration at the firmware level. The choice between trustless computing and secure boot depends on application requirements, with trustless computing excelling in decentralized environments and secure boot providing robust hardware-based security for endpoint devices.
Connection
Trustless computing relies on cryptographic proofs to enable secure transactions without intermediaries, while Secure Boot ensures the system boots only trusted software by verifying digital signatures during startup. Together, they create a hardware-rooted security foundation that prevents unauthorized code execution and maintains system integrity. This connection is crucial for deploying decentralized applications and blockchain nodes that require tamper-proof environments.
Key Terms
Cryptographic Verification
Secure boot uses cryptographic verification to ensure the integrity of firmware and software by validating digital signatures during the boot process, preventing unauthorized code from executing. Trustless computing leverages cryptographic proofs and decentralized consensus mechanisms, enabling secure operations without relying on a trusted third party. Explore the key differences in cryptographic verification between secure boot and trustless computing to deepen your understanding.
Root of Trust
Secure boot ensures device integrity by verifying firmware signatures during startup, relying on a hardware-based Root of Trust embedded in the Trusted Platform Module (TPM) or similar secure elements. Trustless computing, often used in blockchain and decentralized systems, eliminates reliance on any single Root of Trust, distributing trust across multiple nodes through cryptographic consensus. Explore further to understand how these approaches shape modern cybersecurity frameworks and hardware design.
Decentralization
Secure boot ensures system integrity by cryptographically verifying software during the startup process, preventing unauthorized code execution and enhancing device security. Trustless computing eliminates the need for central authorities by enabling decentralized verification of transactions and computations, thereby enhancing transparency and resistance to censorship. Explore the intricacies of these technologies to understand their impact on decentralized ecosystems.
Source and External Links
Unified Extensible Firmware Interface/Secure Boot - ArchWiki - This webpage provides detailed instructions and considerations for implementing Secure Boot, including the use of custom keys and full drive encryption.
Secure boot - This Microsoft webpage outlines the requirements for Secure Boot, including hardware and firmware signing specifications.
How to use Secure Boot on your PC - This EA webpage guides users through the process of enabling Secure Boot on their PCs, necessary for running some EA games.
 dowidth.com
dowidth.com