Quantum-safe cryptography leverages advanced algorithms based on mathematical problems resistant to quantum computer attacks, contrasting with RSA cryptography, which relies on prime factorization vulnerable to quantum algorithms like Shor's. RSA cryptography has been the foundation of secure communications for decades but faces significant risks as scalable quantum computing progresses. Explore the future of secure encryption methods to understand how quantum-safe cryptography can safeguard data in the quantum era.
Why it is important
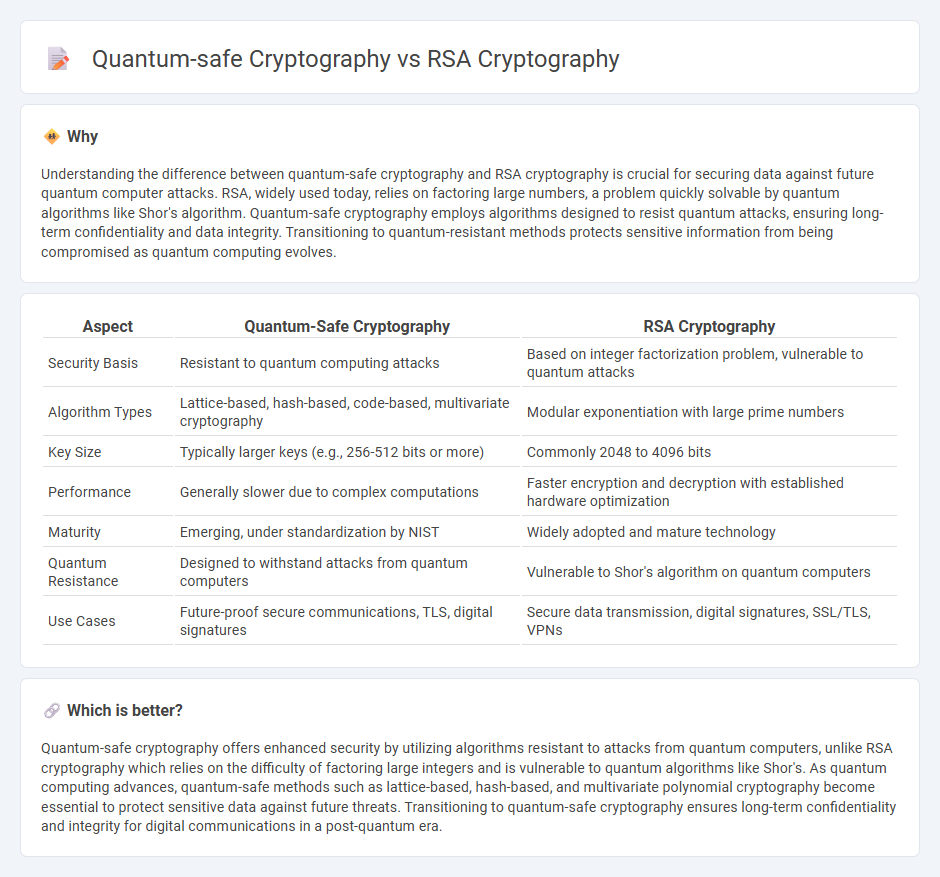
Understanding the difference between quantum-safe cryptography and RSA cryptography is crucial for securing data against future quantum computer attacks. RSA, widely used today, relies on factoring large numbers, a problem quickly solvable by quantum algorithms like Shor's algorithm. Quantum-safe cryptography employs algorithms designed to resist quantum attacks, ensuring long-term confidentiality and data integrity. Transitioning to quantum-resistant methods protects sensitive information from being compromised as quantum computing evolves.
Comparison Table
| Aspect | Quantum-Safe Cryptography | RSA Cryptography |
|---|---|---|
| Security Basis | Resistant to quantum computing attacks | Based on integer factorization problem, vulnerable to quantum attacks |
| Algorithm Types | Lattice-based, hash-based, code-based, multivariate cryptography | Modular exponentiation with large prime numbers |
| Key Size | Typically larger keys (e.g., 256-512 bits or more) | Commonly 2048 to 4096 bits |
| Performance | Generally slower due to complex computations | Faster encryption and decryption with established hardware optimization |
| Maturity | Emerging, under standardization by NIST | Widely adopted and mature technology |
| Quantum Resistance | Designed to withstand attacks from quantum computers | Vulnerable to Shor's algorithm on quantum computers |
| Use Cases | Future-proof secure communications, TLS, digital signatures | Secure data transmission, digital signatures, SSL/TLS, VPNs |
Which is better?
Quantum-safe cryptography offers enhanced security by utilizing algorithms resistant to attacks from quantum computers, unlike RSA cryptography which relies on the difficulty of factoring large integers and is vulnerable to quantum algorithms like Shor's. As quantum computing advances, quantum-safe methods such as lattice-based, hash-based, and multivariate polynomial cryptography become essential to protect sensitive data against future threats. Transitioning to quantum-safe cryptography ensures long-term confidentiality and integrity for digital communications in a post-quantum era.
Connection
Quantum-safe cryptography and RSA cryptography are connected through their roles in securing digital communications, with RSA relying on the difficulty of prime factorization, which quantum computers can potentially break using Shor's algorithm. Quantum-safe cryptography, also known as post-quantum cryptography, employs new cryptographic algorithms designed to resist attacks from quantum computers, ensuring long-term data security. This relationship highlights the transition needed from classical RSA encryption to quantum-resistant methods to protect sensitive information in a future with advanced quantum computing capabilities.
Key Terms
Public-Key Encryption
RSA cryptography relies on the computational difficulty of factoring large integers, making it a widely used public-key encryption method. Quantum-safe cryptography, also known as post-quantum cryptography, employs algorithms like lattice-based, hash-based, and code-based cryptography designed to resist attacks from quantum computers. Explore more about the advancements and implementations in quantum-safe public-key encryption to secure future communications.
Shor's Algorithm
RSA cryptography relies on the computational difficulty of factoring large integers, a problem efficiently solved by Shor's Algorithm on quantum computers, rendering RSA vulnerable in the quantum era. Quantum-safe cryptography employs algorithms based on lattice problems, hash functions, or multivariate polynomials, which are believed to resist attacks from quantum algorithms like Shor's. Explore advancements in quantum-resistant cryptographic protocols to ensure data security against emerging quantum threats.
Lattice-Based Cryptography
Lattice-based cryptography offers robust security against quantum attacks by relying on hard mathematical problems like the Shortest Vector Problem, which remain intractable for quantum computers. Unlike traditional RSA cryptography, which depends on factoring large integers and is vulnerable to Shor's algorithm, lattice-based schemes provide efficient key generation, encryption, and digital signatures suitable for next-generation security standards. Explore the advantages and developments in lattice-based cryptography to understand its critical role in quantum-safe communication.
Source and External Links
What is RSA? How does an RSA work? - Encryption Consulting - RSA is a public-key encryption algorithm that uses asymmetric cryptography to secure data transmissions by allowing data to be encrypted with a public key and decrypted only with the corresponding private key.
RSA Algorithm in Cryptography - GeeksforGeeks - The RSA algorithm is based on the mathematical difficulty of factoring large prime numbers and uses modular arithmetic for encrypting and decrypting data with separate public and private keys.
RSA cryptosystem - Wikipedia - RSA involves generating a public key from two large prime numbers (kept secret), enabling anyone to encrypt messages with the public key, but only the holder of the private key can decrypt them.
 dowidth.com
dowidth.com