Zero Trust security architecture eliminates implicit trust by continuously verifying every user and device attempting to access resources, contrasting sharply with the traditional Castle-and-Moat model that relies on strong perimeter defenses but assumes internal entities are trustworthy. This paradigm shift prioritizes granular access controls, identity verification, and real-time monitoring to prevent breaches and lateral movement within networks. Explore in-depth comparisons and best implementation practices to enhance your organization's cybersecurity posture.
Why it is important
Understanding the difference between Zero Trust and Castle-and-Moat security models is crucial for designing effective cybersecurity strategies that protect against modern threats. Zero Trust operates on the principle of "never trust, always verify," requiring continuous authentication for all users and devices regardless of their location. Castle-and-Moat relies on strong perimeter defenses but assumes internal users and devices are trusted, which can create vulnerabilities if the perimeter is breached. Selecting the appropriate model directly affects an organization's ability to safeguard sensitive data and maintain operational resilience.
Comparison Table
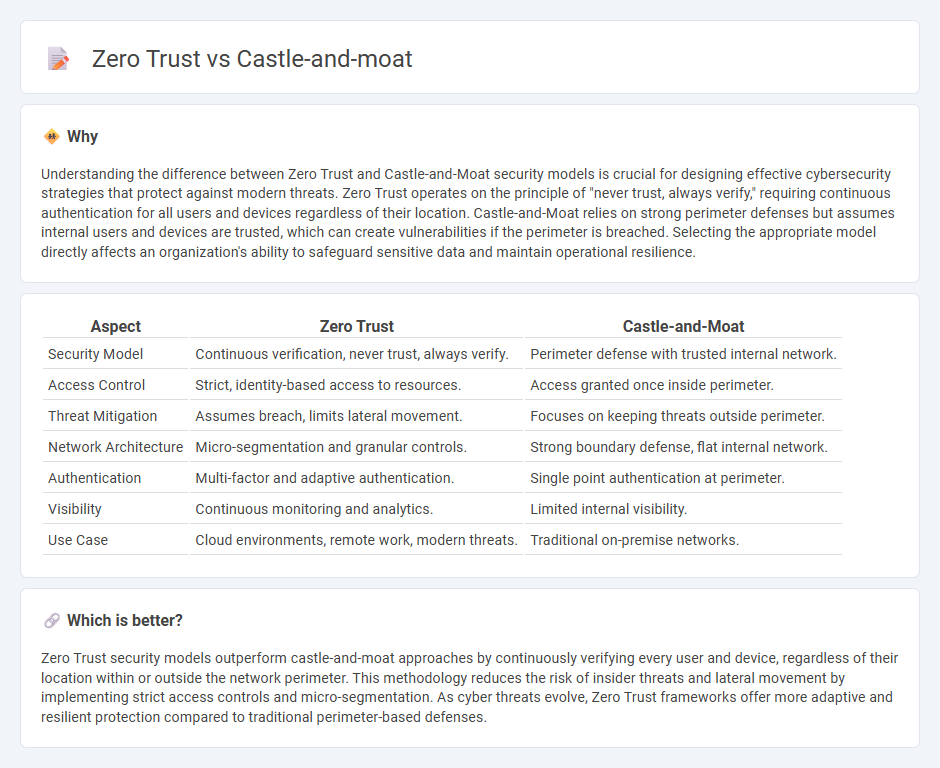
| Aspect | Zero Trust | Castle-and-Moat |
|---|---|---|
| Security Model | Continuous verification, never trust, always verify. | Perimeter defense with trusted internal network. |
| Access Control | Strict, identity-based access to resources. | Access granted once inside perimeter. |
| Threat Mitigation | Assumes breach, limits lateral movement. | Focuses on keeping threats outside perimeter. |
| Network Architecture | Micro-segmentation and granular controls. | Strong boundary defense, flat internal network. |
| Authentication | Multi-factor and adaptive authentication. | Single point authentication at perimeter. |
| Visibility | Continuous monitoring and analytics. | Limited internal visibility. |
| Use Case | Cloud environments, remote work, modern threats. | Traditional on-premise networks. |
Which is better?
Zero Trust security models outperform castle-and-moat approaches by continuously verifying every user and device, regardless of their location within or outside the network perimeter. This methodology reduces the risk of insider threats and lateral movement by implementing strict access controls and micro-segmentation. As cyber threats evolve, Zero Trust frameworks offer more adaptive and resilient protection compared to traditional perimeter-based defenses.
Connection
Zero trust and castle-and-moat security models both aim to protect digital assets but differ fundamentally in approach; zero trust assumes no implicit trust inside or outside the network, continuously verifying every access request, while castle-and-moat relies on strong perimeter defenses with less internal scrutiny. Zero trust enhances the castle-and-moat model by addressing its vulnerability to insider threats and lateral movement within the network through granular access controls and micro-segmentation. Implementing zero trust principles transforms traditional castle-and-moat architectures into more resilient frameworks that adapt to dynamic threat landscapes and cloud environments.
Key Terms
Perimeter Security
Castle-and-moat security relies on traditional perimeter defenses like firewalls and VPNs to create a strong boundary around network assets, assuming all internal traffic is trustworthy. Zero trust architecture eliminates implicit trust by continuously verifying every access request, regardless of location, using principles like least privilege and micro-segmentation. Explore more about how zero trust redefines perimeter security to safeguard modern digital environments.
Least Privilege
The castle-and-moat security model relies on strong perimeter defenses to keep threats out, granting broad access once inside, whereas Zero Trust enforces Least Privilege by continuously verifying users and devices regardless of location. Zero Trust minimizes risk by limiting access to only what is necessary, reducing insider threats and lateral movement within networks. Explore how adopting Zero Trust with a Least Privilege approach can transform your organization's cybersecurity strategy.
Network Segmentation
Castle-and-moat security relies on strong perimeter defenses to protect internal networks, creating a clear boundary between trusted and untrusted zones. Zero Trust shifts the focus to continuous verification and micro-segmentation, ensuring that each segment of the network enforces strict access controls regardless of location. Explore how these network segmentation strategies fundamentally change your cybersecurity posture.
Source and External Links
Castle-and-Moat Network Security Model - The castle-and-moat model is a traditional network security framework where strong defenses (firewalls, IDS/IPS) protect an internal network perimeter, but once inside, users have broad access; this model is now considered outdated and vulnerable.
Moat - Historically, a moat is a broad ditch filled with water surrounding a castle or fort to provide a first line of defense, and modern moats continue to be used architecturally for defense and aesthetic purposes.
IT castle-and-moat security: It is now time to move on - The castle-and-moat security approach in IT involves protecting assets behind a single perimeter, controlled at one access point, which is no longer sufficient against complex modern cyber threats.
 dowidth.com
dowidth.com