Zero Trust Architecture enforces strict identity verification for every user and device attempting to access resources, minimizing the attack surface by assuming no trust by default. Role-Based Access Control (RBAC) assigns permissions based on predefined user roles, simplifying management but potentially allowing excessive access. Explore the core differences and security implications to understand which approach best fits your organization's needs.
Why it is important
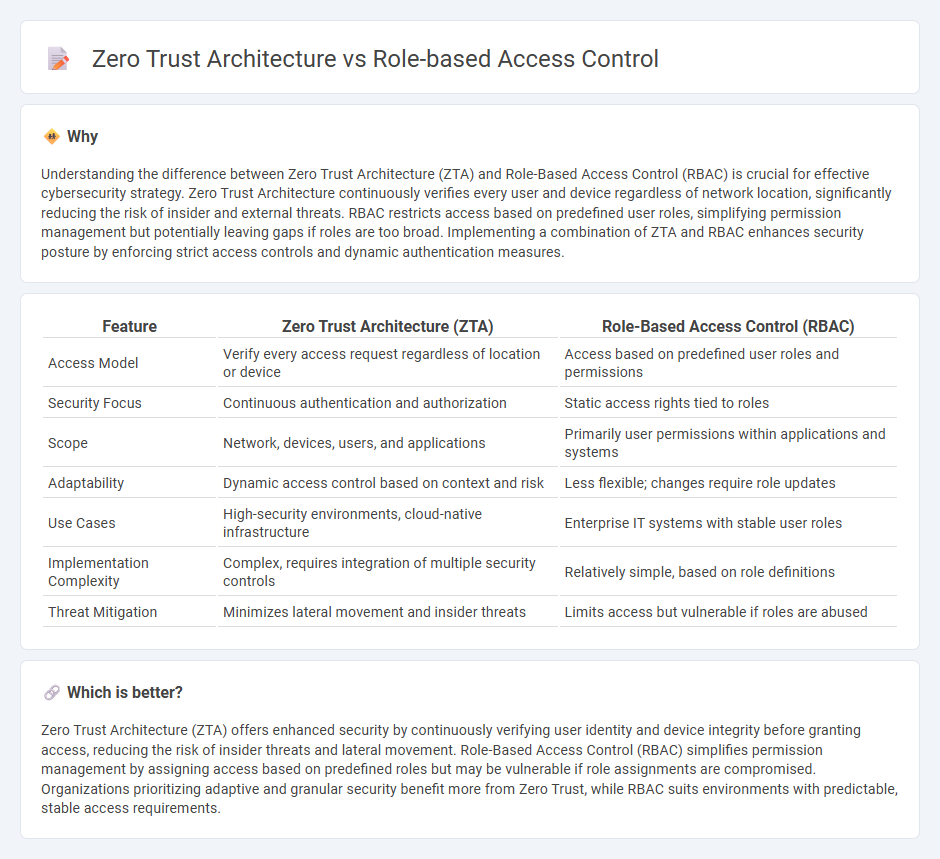
Understanding the difference between Zero Trust Architecture (ZTA) and Role-Based Access Control (RBAC) is crucial for effective cybersecurity strategy. Zero Trust Architecture continuously verifies every user and device regardless of network location, significantly reducing the risk of insider and external threats. RBAC restricts access based on predefined user roles, simplifying permission management but potentially leaving gaps if roles are too broad. Implementing a combination of ZTA and RBAC enhances security posture by enforcing strict access controls and dynamic authentication measures.
Comparison Table
| Feature | Zero Trust Architecture (ZTA) | Role-Based Access Control (RBAC) |
|---|---|---|
| Access Model | Verify every access request regardless of location or device | Access based on predefined user roles and permissions |
| Security Focus | Continuous authentication and authorization | Static access rights tied to roles |
| Scope | Network, devices, users, and applications | Primarily user permissions within applications and systems |
| Adaptability | Dynamic access control based on context and risk | Less flexible; changes require role updates |
| Use Cases | High-security environments, cloud-native infrastructure | Enterprise IT systems with stable user roles |
| Implementation Complexity | Complex, requires integration of multiple security controls | Relatively simple, based on role definitions |
| Threat Mitigation | Minimizes lateral movement and insider threats | Limits access but vulnerable if roles are abused |
Which is better?
Zero Trust Architecture (ZTA) offers enhanced security by continuously verifying user identity and device integrity before granting access, reducing the risk of insider threats and lateral movement. Role-Based Access Control (RBAC) simplifies permission management by assigning access based on predefined roles but may be vulnerable if role assignments are compromised. Organizations prioritizing adaptive and granular security benefit more from Zero Trust, while RBAC suits environments with predictable, stable access requirements.
Connection
Zero Trust Architecture and Role-Based Access Control (RBAC) are interconnected in enhancing cybersecurity by strictly enforcing access permissions based on user roles and continuous verification of identity. Zero Trust assumes no user or device is trusted by default, requiring RBAC to define and limit access rights to sensitive resources according to predefined roles. This combination minimizes attack surfaces, prevents unauthorized access, and supports dynamic policy enforcement in modern enterprise environments.
Key Terms
Permissions
Role-based access control (RBAC) assigns permissions based on predefined user roles, simplifying management but potentially allowing broader access than necessary. Zero Trust Architecture enforces strict, continuous verification of user permissions and device integrity for each access request, minimizing the risk of unauthorized data exposure. Explore these models further to understand how permission controls impact organizational security frameworks.
Least Privilege
Role-based access control (RBAC) assigns permissions based on predefined user roles, enforcing least privilege by limiting access to resources necessary for specific job functions. Zero Trust Architecture (ZTA) eliminates implicit trust, continuously verifying every access request and applying dynamic least privilege principles across all network interactions. Explore detailed comparisons to understand how each approach strengthens security through least privilege enforcement.
Continuous Authentication
Role-based access control (RBAC) assigns permissions to users based on predefined roles, limiting access to resources according to job functions but often lacks continuous verification during sessions. Zero trust architecture (ZTA) emphasizes continuous authentication by constantly validating user identity and device health, ensuring access decisions adapt to real-time risk assessments. Explore how integrating continuous authentication within RBAC and ZTA frameworks enhances security resilience in dynamic environments.
Source and External Links
Role-Based Access Control - Assigns permissions based on predefined roles, simplifying user management and reducing errors compared to individual permission assignments.
What is role-based access control (RBAC)? - Manages user access to systems by grouping users into roles with specific permissions, making it easier to add, modify, or revoke access across groups.
What Is Role-Based Access Control (RBAC)? - Provides a granular, role-based approach to identity and access management (IAM), streamlining authorization and improving security by limiting users to necessary resources.
 dowidth.com
dowidth.com