Post-quantum cryptography focuses on developing encryption methods resistant to quantum computer attacks, ensuring data security in the future. Digital signatures verify the authenticity and integrity of messages using classical cryptographic algorithms vulnerable to quantum decryption. Explore the advancements bridging post-quantum cryptography and digital signatures to safeguard digital communications.
Why it is important
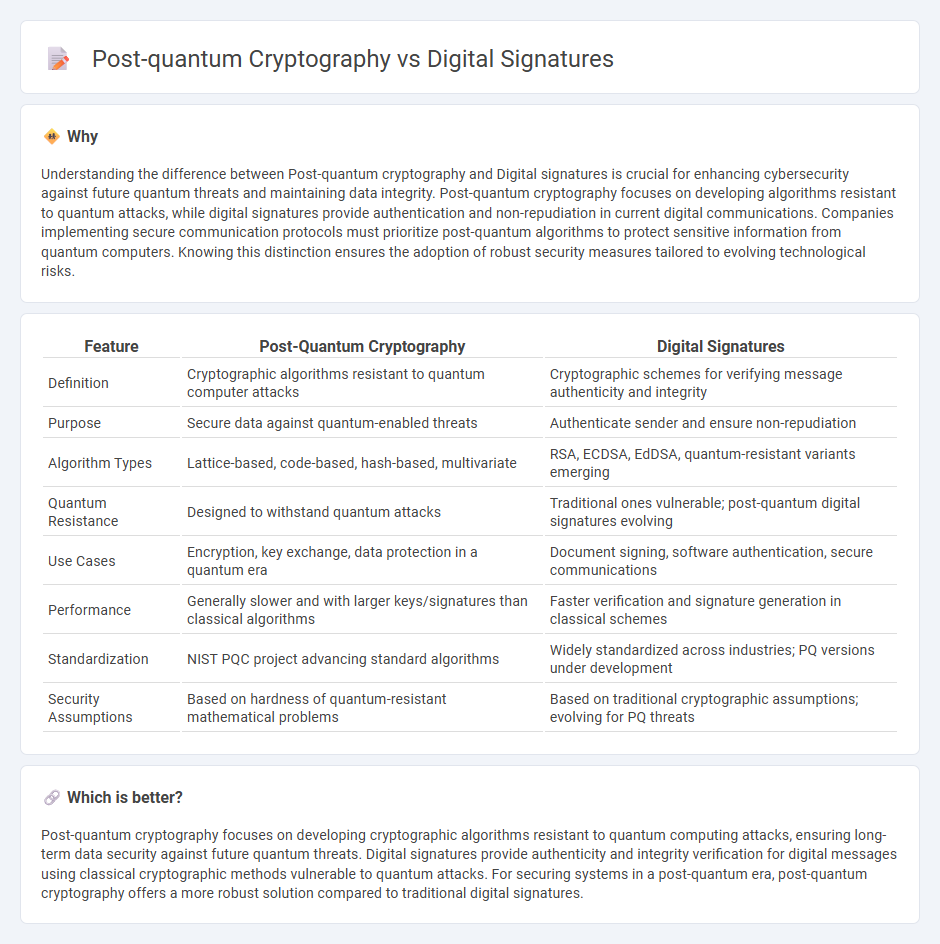
Understanding the difference between Post-quantum cryptography and Digital signatures is crucial for enhancing cybersecurity against future quantum threats and maintaining data integrity. Post-quantum cryptography focuses on developing algorithms resistant to quantum attacks, while digital signatures provide authentication and non-repudiation in current digital communications. Companies implementing secure communication protocols must prioritize post-quantum algorithms to protect sensitive information from quantum computers. Knowing this distinction ensures the adoption of robust security measures tailored to evolving technological risks.
Comparison Table
| Feature | Post-Quantum Cryptography | Digital Signatures |
|---|---|---|
| Definition | Cryptographic algorithms resistant to quantum computer attacks | Cryptographic schemes for verifying message authenticity and integrity |
| Purpose | Secure data against quantum-enabled threats | Authenticate sender and ensure non-repudiation |
| Algorithm Types | Lattice-based, code-based, hash-based, multivariate | RSA, ECDSA, EdDSA, quantum-resistant variants emerging |
| Quantum Resistance | Designed to withstand quantum attacks | Traditional ones vulnerable; post-quantum digital signatures evolving |
| Use Cases | Encryption, key exchange, data protection in a quantum era | Document signing, software authentication, secure communications |
| Performance | Generally slower and with larger keys/signatures than classical algorithms | Faster verification and signature generation in classical schemes |
| Standardization | NIST PQC project advancing standard algorithms | Widely standardized across industries; PQ versions under development |
| Security Assumptions | Based on hardness of quantum-resistant mathematical problems | Based on traditional cryptographic assumptions; evolving for PQ threats |
Which is better?
Post-quantum cryptography focuses on developing cryptographic algorithms resistant to quantum computing attacks, ensuring long-term data security against future quantum threats. Digital signatures provide authenticity and integrity verification for digital messages using classical cryptographic methods vulnerable to quantum attacks. For securing systems in a post-quantum era, post-quantum cryptography offers a more robust solution compared to traditional digital signatures.
Connection
Post-quantum cryptography develops encryption algorithms resistant to quantum computer attacks, securing digital signatures against future decryption threats. Digital signatures rely on cryptographic methods to verify authenticity and integrity of messages, which post-quantum cryptographic algorithms aim to protect by replacing vulnerable classical schemes. The integration of post-quantum algorithms ensures digital signatures remain secure in the era of quantum computing advances.
Key Terms
Public Key Infrastructure (PKI)
Digital signatures in traditional Public Key Infrastructure (PKI) rely on mathematical problems like RSA and ECC, which are vulnerable to attacks from quantum computers. Post-quantum cryptography aims to develop algorithms resistant to quantum attacks, ensuring long-term security for PKI systems. Explore how integrating post-quantum algorithms can future-proof your digital signature processes and enhance PKI resilience.
Quantum-resistant Algorithms
Quantum-resistant algorithms are essential in digital signatures to protect data from potential threats posed by quantum computers that can break traditional cryptographic schemes like RSA and ECDSA. Post-quantum cryptography employs advanced mathematical structures such as lattice-based, hash-based, and multivariate polynomial algorithms to create digital signatures resistant to quantum attacks. Explore the latest developments in quantum-resistant digital signature algorithms to secure future communications effectively.
Hash-based Signatures
Hash-based signatures provide robust security in digital signatures by relying on well-studied cryptographic hash functions, making them resistant to quantum computing attacks that threaten traditional algorithms like RSA and ECC. Unlike classic digital signatures, hash-based schemes such as the LMS and XMSS protocols offer forward-secure authentication with minimal reliance on complex mathematical problems. Explore the advancements and implementation challenges of post-quantum hash-based signature algorithms to understand their potential impact on secure communications.
Source and External Links
What is a Digital Signature? | DigiCert FAQ - Digital signatures authenticate signer identity and document integrity by binding a digital certificate to a document using public key infrastructure (PKI), ensuring the signer is who they claim to be and the document is unaltered, with legal validity in some countries.
Digital Signatures: What They Are & How They Work - Digital signatures use cryptographic algorithms within a PKI framework to create a unique signature using a private key to sign and a public key to verify, ensuring authenticity and integrity of digital documents.
What is a Digital Signature? | Definition from TechTarget - A digital signature is a mathematical technique that validates the authenticity and integrity of digital data by using asymmetric cryptography, where the signer encrypts data with a private key and the recipient verifies it with the signer's public key, often issued by trusted certificate authorities.
 dowidth.com
dowidth.com