Zero Trust architecture enforces strict access controls by continuously verifying every user and device regardless of their location, minimizing security risks in modern networks. Identity-Aware Proxy (IAP) simplifies secure access by using user identity and context to grant permissions, effectively protecting applications without relying on traditional VPNs. Explore the distinctions and benefits of Zero Trust and Identity-Aware Proxy to enhance your cybersecurity strategy.
Why it is important
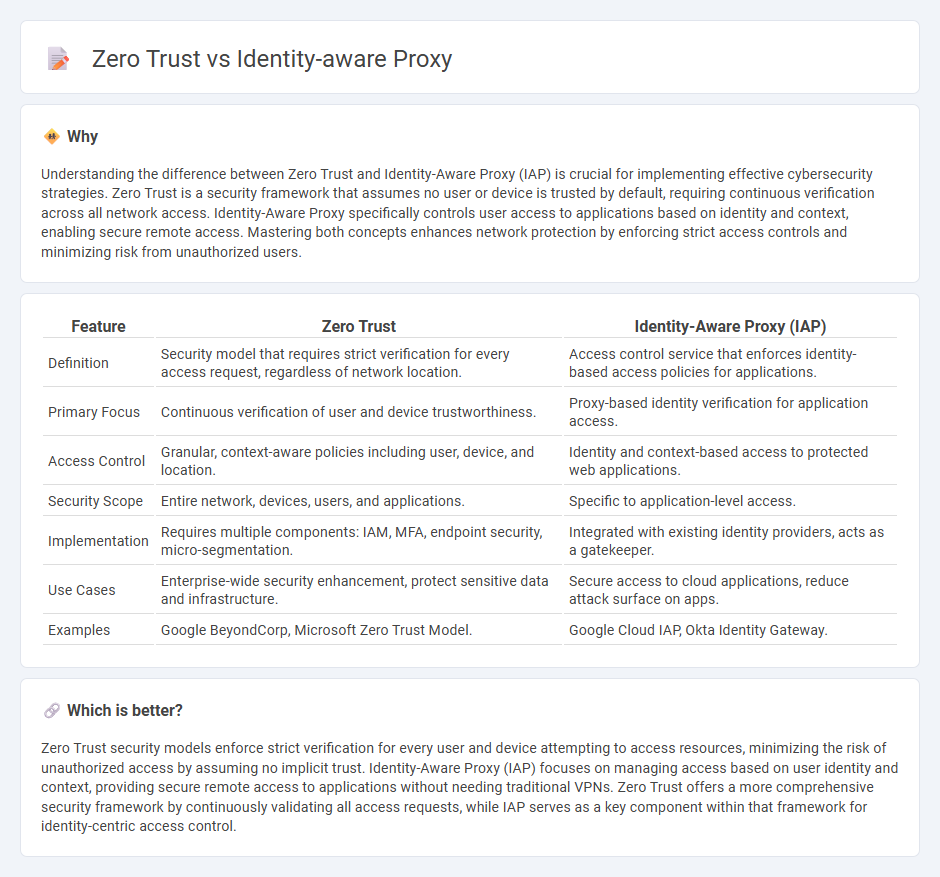
Understanding the difference between Zero Trust and Identity-Aware Proxy (IAP) is crucial for implementing effective cybersecurity strategies. Zero Trust is a security framework that assumes no user or device is trusted by default, requiring continuous verification across all network access. Identity-Aware Proxy specifically controls user access to applications based on identity and context, enabling secure remote access. Mastering both concepts enhances network protection by enforcing strict access controls and minimizing risk from unauthorized users.
Comparison Table
| Feature | Zero Trust | Identity-Aware Proxy (IAP) |
|---|---|---|
| Definition | Security model that requires strict verification for every access request, regardless of network location. | Access control service that enforces identity-based access policies for applications. |
| Primary Focus | Continuous verification of user and device trustworthiness. | Proxy-based identity verification for application access. |
| Access Control | Granular, context-aware policies including user, device, and location. | Identity and context-based access to protected web applications. |
| Security Scope | Entire network, devices, users, and applications. | Specific to application-level access. |
| Implementation | Requires multiple components: IAM, MFA, endpoint security, micro-segmentation. | Integrated with existing identity providers, acts as a gatekeeper. |
| Use Cases | Enterprise-wide security enhancement, protect sensitive data and infrastructure. | Secure access to cloud applications, reduce attack surface on apps. |
| Examples | Google BeyondCorp, Microsoft Zero Trust Model. | Google Cloud IAP, Okta Identity Gateway. |
Which is better?
Zero Trust security models enforce strict verification for every user and device attempting to access resources, minimizing the risk of unauthorized access by assuming no implicit trust. Identity-Aware Proxy (IAP) focuses on managing access based on user identity and context, providing secure remote access to applications without needing traditional VPNs. Zero Trust offers a more comprehensive security framework by continuously validating all access requests, while IAP serves as a key component within that framework for identity-centric access control.
Connection
Zero trust architecture relies on identity-aware proxy (IAP) to enforce strict access controls by continuously verifying user identities and device security before granting access to applications. Identity-aware proxy acts as a gatekeeper, ensuring that every request passes authentication and authorization checks based on dynamic user context and risk factors. This integration minimizes attack surfaces, prevents unauthorized access, and supports secure remote work environments.
Key Terms
Authentication
Identity-aware proxy (IAP) enhances security by verifying user identities before granting access to specific resources, ensuring that only authenticated individuals interact with sensitive data. Zero Trust emphasizes continuous authentication and strict access controls, treating all users and devices as untrusted by default and requiring dynamic verification throughout every session. Explore detailed comparisons to understand which authentication approach best suits your organization's security needs.
Access Control
Identity-aware proxy enforces access control by validating user identity and context before granting access, supporting fine-grained policies based on roles and attributes. Zero Trust access control operates on the principle of "never trust, always verify," continuously authenticating and authorizing users and devices regardless of network location. Explore how these approaches redefine secure access management in modern IT environments.
Least Privilege
Identity-aware proxy enforces Least Privilege by verifying user identity and context before granting access to specific applications, minimizing exposure to unauthorized resources. Zero Trust architecture extends this principle by continuously validating trust at every access point across the network, ensuring no implicit trust regardless of location. Explore how these approaches optimize security through Least Privilege models for detailed insights.
Source and External Links
Identity-Aware Proxy (IAP) in Google Cloud Platform - CloudThat - IAP is a Google Cloud service that enforces Zero Trust security by strictly authenticating users and using contextual information like identity, device, and location to control access to applications without requiring a VPN.
Identity Aware Proxy (IAP): Meaning, Pricing, Solutions - Pomerium - An Identity-Aware Proxy continuously evaluates contextual factors such as location, device, and time along with role-based access policies to allow or deny access, implementing strict, fine-grained, and dynamic access control.
F5 BIG-IP APM Identity Aware Proxy (IAP) and Zero Trust - IAP provides per-request application access with fine-grained authentication and authorization, replacing broad VPN access, thereby supporting the Zero Trust security model and reducing risks and infrastructure costs.
 dowidth.com
dowidth.com