Quantum-safe cryptography employs algorithms designed to withstand attacks from quantum computers, ensuring secure data encryption in a post-quantum era, whereas traditional public-key cryptography relies on mathematical problems like factoring large numbers, which quantum computing threatens to break. Key protocols such as lattice-based, hash-based, and code-based cryptography form the foundation of quantum-safe methods, offering resistance against quantum-enabled decryption. Explore in-depth the evolving landscape of cryptography and its critical role in future-proof cybersecurity.
Why it is important
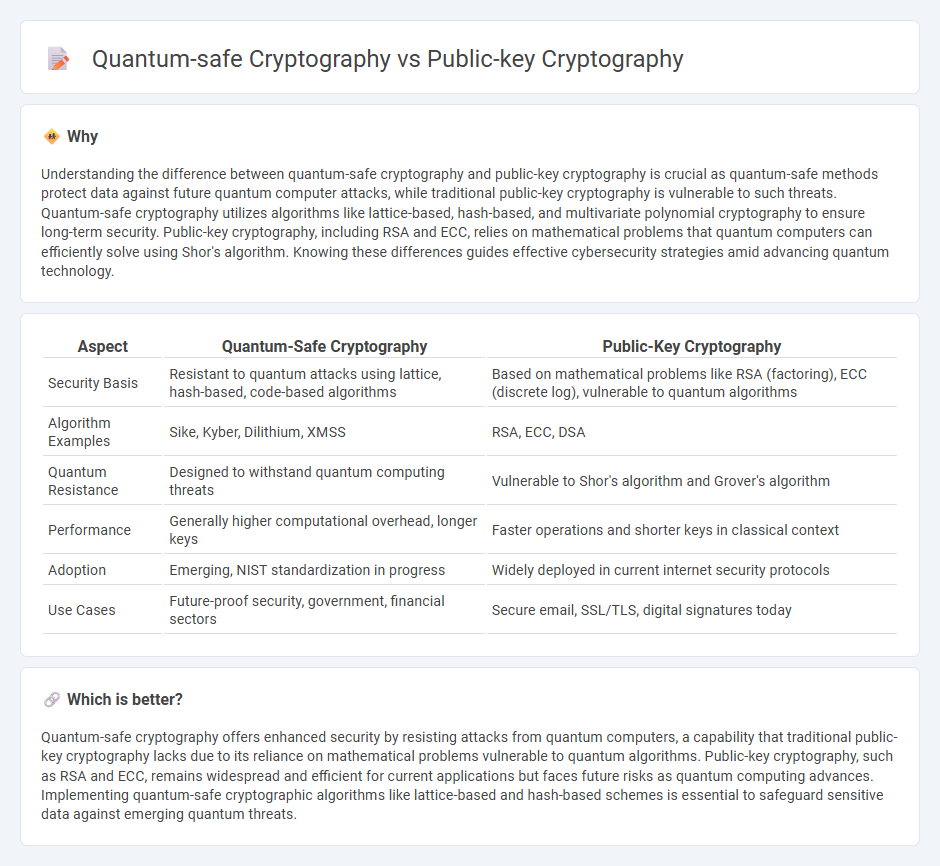
Understanding the difference between quantum-safe cryptography and public-key cryptography is crucial as quantum-safe methods protect data against future quantum computer attacks, while traditional public-key cryptography is vulnerable to such threats. Quantum-safe cryptography utilizes algorithms like lattice-based, hash-based, and multivariate polynomial cryptography to ensure long-term security. Public-key cryptography, including RSA and ECC, relies on mathematical problems that quantum computers can efficiently solve using Shor's algorithm. Knowing these differences guides effective cybersecurity strategies amid advancing quantum technology.
Comparison Table
| Aspect | Quantum-Safe Cryptography | Public-Key Cryptography |
|---|---|---|
| Security Basis | Resistant to quantum attacks using lattice, hash-based, code-based algorithms | Based on mathematical problems like RSA (factoring), ECC (discrete log), vulnerable to quantum algorithms |
| Algorithm Examples | Sike, Kyber, Dilithium, XMSS | RSA, ECC, DSA |
| Quantum Resistance | Designed to withstand quantum computing threats | Vulnerable to Shor's algorithm and Grover's algorithm |
| Performance | Generally higher computational overhead, longer keys | Faster operations and shorter keys in classical context |
| Adoption | Emerging, NIST standardization in progress | Widely deployed in current internet security protocols |
| Use Cases | Future-proof security, government, financial sectors | Secure email, SSL/TLS, digital signatures today |
Which is better?
Quantum-safe cryptography offers enhanced security by resisting attacks from quantum computers, a capability that traditional public-key cryptography lacks due to its reliance on mathematical problems vulnerable to quantum algorithms. Public-key cryptography, such as RSA and ECC, remains widespread and efficient for current applications but faces future risks as quantum computing advances. Implementing quantum-safe cryptographic algorithms like lattice-based and hash-based schemes is essential to safeguard sensitive data against emerging quantum threats.
Connection
Quantum-safe cryptography enhances public-key cryptography by developing algorithms resistant to quantum computing attacks, ensuring secure data transmission in a future with powerful quantum processors. Traditional public-key cryptographic methods like RSA and ECC rely on computational hardness assumptions vulnerable to quantum algorithms such as Shor's algorithm, prompting the need for quantum-resistant substitutes. Integrating lattice-based, hash-based, or multivariate polynomial cryptographic schemes fortifies public-key infrastructure against the potential threats posed by quantum computing advancements.
Key Terms
Asymmetric Encryption
Public-key cryptography relies on mathematical problems like factoring large primes, which current algorithms efficiently solve, whereas quantum-safe cryptography employs algorithms resistant to quantum attacks, such as lattice-based or hash-based cryptography. Asymmetric encryption methods like RSA and ECC become vulnerable in a quantum era due to Shor's algorithm, prompting development of post-quantum cryptographic standards by NIST. Explore advances in quantum-safe asymmetric encryption to secure communication in the coming quantum computing landscape.
Quantum Algorithms
Public-key cryptography relies on mathematical problems like integer factorization, which quantum algorithms such as Shor's algorithm can solve efficiently, threatening traditional encryption schemes. Quantum-safe cryptography uses quantum-resistant algorithms including lattice-based, hash-based, and multivariate polynomial cryptography designed to withstand attacks from quantum computers. Explore the latest advancements in quantum-safe cryptographic algorithms and their impact on secure communications.
Post-Quantum Cryptography
Post-Quantum Cryptography (PQC) addresses vulnerabilities in traditional public-key cryptography algorithms like RSA and ECC, which are susceptible to quantum computing attacks exploiting Shor's algorithm. PQC involves developing cryptographic techniques based on hard mathematical problems such as lattice-based, code-based, and hash-based cryptography that resist both classical and quantum attacks. Explore further to understand how PQC is revolutionizing data security in the quantum era.
Source and External Links
Public-key cryptography - Also called asymmetric cryptography, it relies on pairs of mathematically related keys--a public key shared openly and a private key kept secret--used for encryption, authentication, and digital signatures.
What is a Public Key and How Does it Work? - Public keys, created by algorithms like RSA, are used for encrypting data, while private keys, kept secret, are used to decrypt it, with public key exchange allowing secure communication without prior shared secrets.
Public Key Cryptography - This method ensures confidentiality and integrity by allowing anyone to encrypt messages with a recipient's public key, decryptable only with their private key, and by enabling digital signatures with private keys verifiable by public keys.
 dowidth.com
dowidth.com