Quantum key distribution leverages principles of quantum mechanics to enable secure communication by detecting any eavesdropping attempts, providing theoretically unbreakable encryption keys. Symmetric key cryptography relies on a shared secret key for both encryption and decryption, offering efficiency but facing challenges in key distribution and vulnerability if the key is compromised. Explore how these encryption methods impact data security in an increasingly digital world.
Why it is important
Understanding the difference between quantum key distribution (QKD) and symmetric key cryptography is crucial because QKD offers theoretically unbreakable encryption based on quantum mechanics, while symmetric key cryptography relies on computational hardness which may be vulnerable to quantum attacks. QKD uses quantum states to securely exchange keys, ensuring detection of any eavesdropping, whereas symmetric key cryptography uses the same secret key for encryption and decryption, making key management and distribution more challenging. Enterprises and governments must distinguish these methods to prepare for future cybersecurity threats posed by quantum computers. Knowing their differences enables the implementation of robust encryption strategies resilient to emerging quantum technologies.
Comparison Table
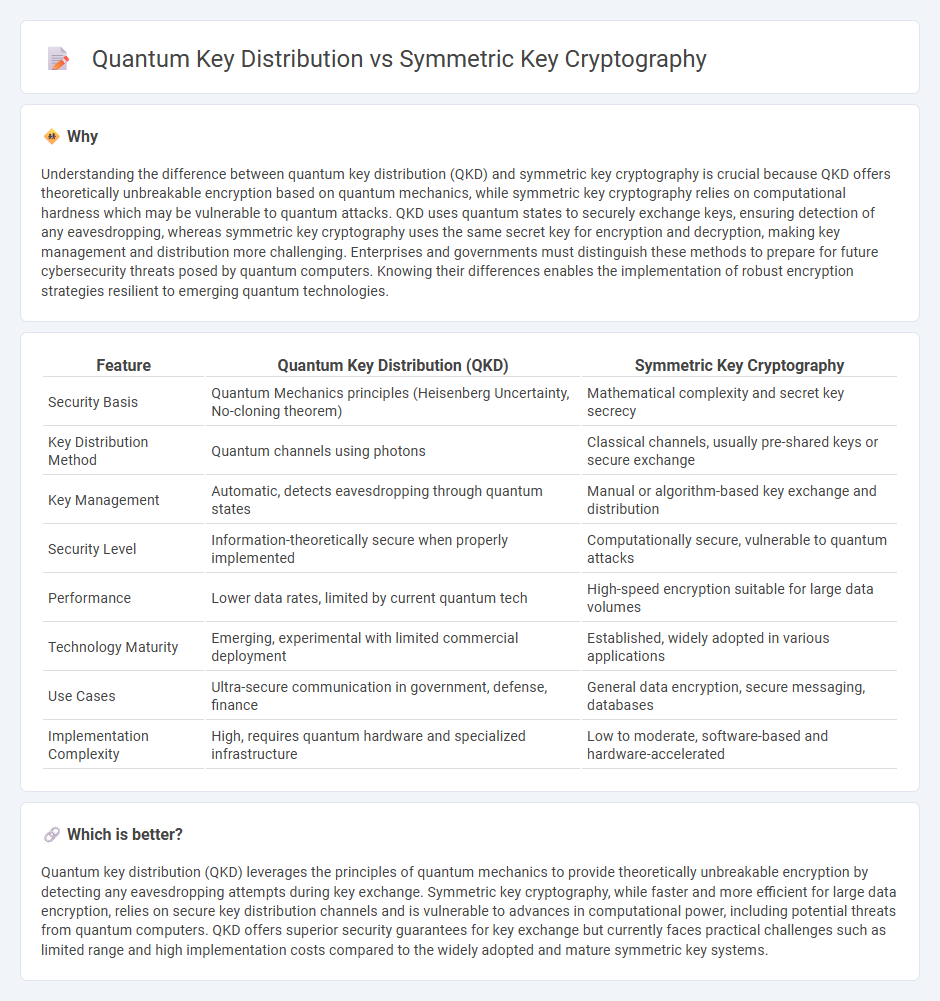
| Feature | Quantum Key Distribution (QKD) | Symmetric Key Cryptography |
|---|---|---|
| Security Basis | Quantum Mechanics principles (Heisenberg Uncertainty, No-cloning theorem) | Mathematical complexity and secret key secrecy |
| Key Distribution Method | Quantum channels using photons | Classical channels, usually pre-shared keys or secure exchange |
| Key Management | Automatic, detects eavesdropping through quantum states | Manual or algorithm-based key exchange and distribution |
| Security Level | Information-theoretically secure when properly implemented | Computationally secure, vulnerable to quantum attacks |
| Performance | Lower data rates, limited by current quantum tech | High-speed encryption suitable for large data volumes |
| Technology Maturity | Emerging, experimental with limited commercial deployment | Established, widely adopted in various applications |
| Use Cases | Ultra-secure communication in government, defense, finance | General data encryption, secure messaging, databases |
| Implementation Complexity | High, requires quantum hardware and specialized infrastructure | Low to moderate, software-based and hardware-accelerated |
Which is better?
Quantum key distribution (QKD) leverages the principles of quantum mechanics to provide theoretically unbreakable encryption by detecting any eavesdropping attempts during key exchange. Symmetric key cryptography, while faster and more efficient for large data encryption, relies on secure key distribution channels and is vulnerable to advances in computational power, including potential threats from quantum computers. QKD offers superior security guarantees for key exchange but currently faces practical challenges such as limited range and high implementation costs compared to the widely adopted and mature symmetric key systems.
Connection
Quantum key distribution (QKD) enhances symmetric key cryptography by enabling the secure exchange of encryption keys using quantum mechanics principles, preventing eavesdropping through quantum entanglement and no-cloning theorem. Symmetric key algorithms then utilize these securely distributed keys for efficient and confidential data encryption and decryption. This integration strengthens overall cryptographic security by combining quantum-resistant key exchange with fast symmetric encryption methods.
Key Terms
Shared Secret Key
Symmetric key cryptography relies on a shared secret key for both encryption and decryption, requiring secure key distribution channels vulnerable to interception. Quantum key distribution (QKD) utilizes quantum mechanics principles to enable secure sharing of secret keys with the ability to detect eavesdropping, ensuring unprecedented security. Explore more about how QKD revolutionizes secure communications by fundamentally changing shared secret key exchange.
Quantum Entanglement
Symmetric key cryptography relies on shared secret keys for encrypting and decrypting data, while quantum key distribution (QKD) leverages the principles of quantum entanglement to enable secure key exchange with theoretically unbreakable security. Quantum entanglement ensures that any eavesdropping attempt disrupts the entangled quantum states, instantly signaling potential interception and maintaining communication integrity. Discover how quantum entanglement revolutionizes cryptographic security beyond classical symmetric key methods.
Eavesdropping Detection
Symmetric key cryptography relies on shared secret keys and lacks inherent mechanisms for detecting eavesdropping during key exchange, making key compromise a significant risk. Quantum key distribution (QKD) uses principles of quantum mechanics to enable detection of any eavesdropping attempts through disturbances in quantum states, ensuring enhanced security. Explore more to understand how QKD revolutionizes secure communication by offering real-time eavesdropping detection.
Source and External Links
Symmetric Key Algorithms - Tutorials Point - Symmetric key cryptography uses a shared secret key for both encryption and decryption, making it faster and more efficient than asymmetric methods but requiring secure key sharing and being less secure if the key is compromised.
Symmetric-key algorithm - Wikipedia - Symmetric-key algorithms use the same cryptographic key for encrypting and decrypting data, often involving block or stream ciphers, and are efficient for bulk encryption though they require both parties to share the secret key.
What is Symmetric Encryption? - Entrust - Symmetric encryption involves generating a secure random key shared between sender and receiver to encrypt plaintext into ciphertext and decrypt it back, relying on mathematical algorithms where the same key enables both processes.
 dowidth.com
dowidth.com