Quantum-safe cryptography focuses on securing data against the potential threats posed by quantum computers using cryptographic systems that are currently proven to be resilient. Post-quantum cryptography involves developing new algorithms designed to withstand quantum attacks, ensuring security even after quantum computing becomes mainstream. Explore the latest advancements in both fields to understand how they protect sensitive information in the quantum era.
Why it is important
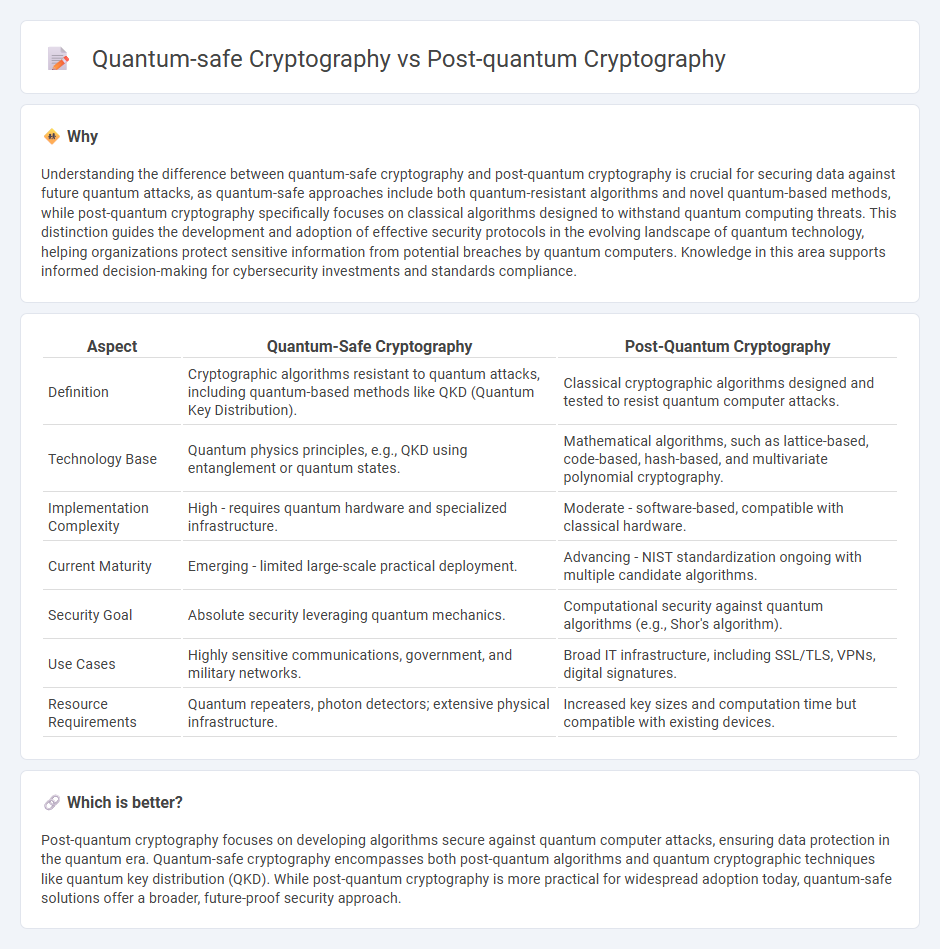
Understanding the difference between quantum-safe cryptography and post-quantum cryptography is crucial for securing data against future quantum attacks, as quantum-safe approaches include both quantum-resistant algorithms and novel quantum-based methods, while post-quantum cryptography specifically focuses on classical algorithms designed to withstand quantum computing threats. This distinction guides the development and adoption of effective security protocols in the evolving landscape of quantum technology, helping organizations protect sensitive information from potential breaches by quantum computers. Knowledge in this area supports informed decision-making for cybersecurity investments and standards compliance.
Comparison Table
| Aspect | Quantum-Safe Cryptography | Post-Quantum Cryptography |
|---|---|---|
| Definition | Cryptographic algorithms resistant to quantum attacks, including quantum-based methods like QKD (Quantum Key Distribution). | Classical cryptographic algorithms designed and tested to resist quantum computer attacks. |
| Technology Base | Quantum physics principles, e.g., QKD using entanglement or quantum states. | Mathematical algorithms, such as lattice-based, code-based, hash-based, and multivariate polynomial cryptography. |
| Implementation Complexity | High - requires quantum hardware and specialized infrastructure. | Moderate - software-based, compatible with classical hardware. |
| Current Maturity | Emerging - limited large-scale practical deployment. | Advancing - NIST standardization ongoing with multiple candidate algorithms. |
| Security Goal | Absolute security leveraging quantum mechanics. | Computational security against quantum algorithms (e.g., Shor's algorithm). |
| Use Cases | Highly sensitive communications, government, and military networks. | Broad IT infrastructure, including SSL/TLS, VPNs, digital signatures. |
| Resource Requirements | Quantum repeaters, photon detectors; extensive physical infrastructure. | Increased key sizes and computation time but compatible with existing devices. |
Which is better?
Post-quantum cryptography focuses on developing algorithms secure against quantum computer attacks, ensuring data protection in the quantum era. Quantum-safe cryptography encompasses both post-quantum algorithms and quantum cryptographic techniques like quantum key distribution (QKD). While post-quantum cryptography is more practical for widespread adoption today, quantum-safe solutions offer a broader, future-proof security approach.
Connection
Quantum-safe cryptography encompasses a range of techniques, including Post-quantum cryptography, designed to secure data against quantum computing attacks. Post-quantum cryptography specifically focuses on developing algorithms resistant to the computational power of quantum machines, ensuring long-term data protection. Both fields aim to safeguard digital communications as quantum computers threaten traditional cryptographic protocols.
Key Terms
Quantum-resistant algorithms
Quantum-resistant algorithms form the core of post-quantum cryptography, designed specifically to withstand attacks from quantum computers. These algorithms utilize mathematical problems believed to be hard for both classical and quantum computers, such as lattice-based, hash-based, and multivariate polynomial cryptography. Explore the latest advancements in quantum-resistant algorithms to secure data against future quantum threats.
Shor's algorithm
Shor's algorithm poses a significant threat to classical cryptographic systems by efficiently factoring large integers and computing discrete logarithms, which undermines RSA and ECC security. Post-quantum cryptography designs algorithms resistant to quantum attacks like Shor's, using lattice-based, hash-based, code-based, and multivariate polynomial constructions. Explore the latest advancements in quantum-safe cryptographic protocols to secure data against future quantum adversaries.
Lattice-based cryptography
Lattice-based cryptography stands as a leading candidate in both post-quantum and quantum-safe cryptographic frameworks due to its resistance to attacks from quantum computers, particularly addressing vulnerabilities found in classical algorithms like RSA and ECC. This cryptographic approach leverages the hardness of lattice problems such as Learning With Errors (LWE) and Shortest Vector Problem (SVP), which remain difficult for quantum algorithms like Shor's algorithm to solve efficiently. Explore the advancements and implementation strategies in lattice-based cryptography to understand its critical role in securing future communication networks.
Source and External Links
Post-quantum cryptography - Wikipedia - Post-quantum cryptography (PQC) develops cryptographic algorithms, such as lattice-based, multivariate, and large symmetric-key systems, designed to be secure against attacks by quantum computers.
Post-Quantum Cryptography | CSRC - The goal of post-quantum cryptography is to create cryptographic systems that remain secure against both quantum and classical computers while maintaining compatibility with existing networks and protocols.
What Is Post-Quantum Cryptography? | NIST - NIST is leading the standardization of post-quantum cryptographic algorithms to defend against potential cyberattacks from future quantum computers.
 dowidth.com
dowidth.com