Zero Trust Architecture eliminates implicit trust by continuously verifying every user, device, and network interaction, enhancing security beyond traditional perimeter defenses. Identity-Based Access Control (IBAC) focuses on granting access based on user identities and roles but may lack the dynamic verification needed against sophisticated threats. Explore deeper to understand how these approaches redefine cybersecurity frameworks.
Why it is important
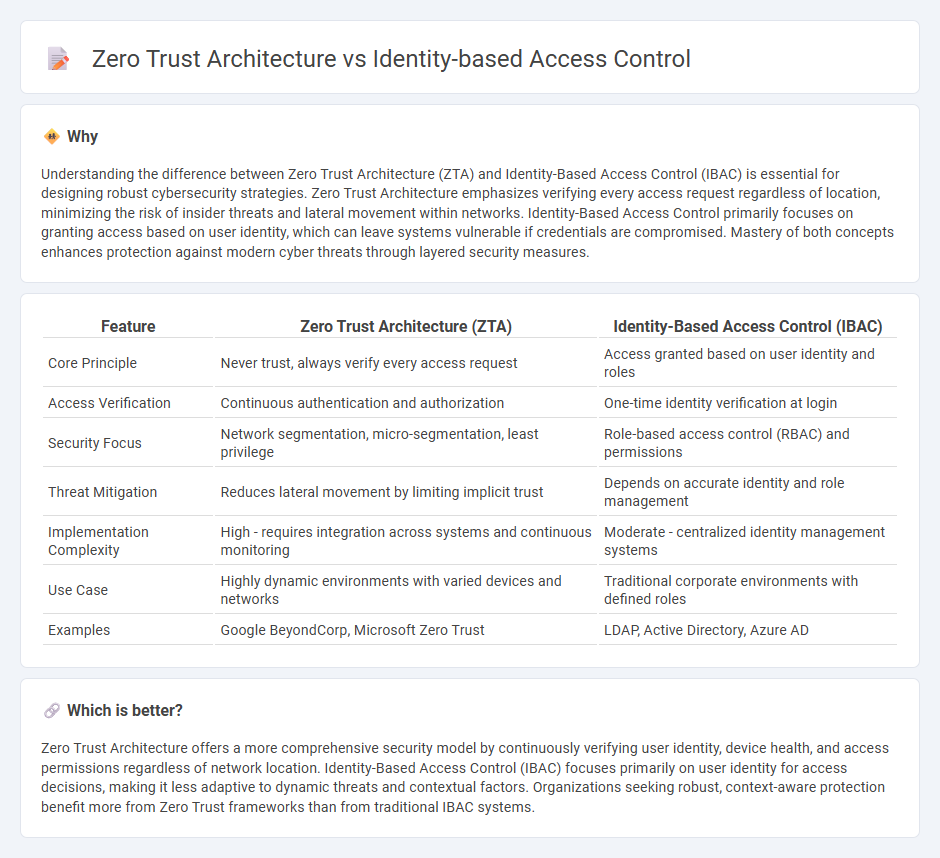
Understanding the difference between Zero Trust Architecture (ZTA) and Identity-Based Access Control (IBAC) is essential for designing robust cybersecurity strategies. Zero Trust Architecture emphasizes verifying every access request regardless of location, minimizing the risk of insider threats and lateral movement within networks. Identity-Based Access Control primarily focuses on granting access based on user identity, which can leave systems vulnerable if credentials are compromised. Mastery of both concepts enhances protection against modern cyber threats through layered security measures.
Comparison Table
| Feature | Zero Trust Architecture (ZTA) | Identity-Based Access Control (IBAC) |
|---|---|---|
| Core Principle | Never trust, always verify every access request | Access granted based on user identity and roles |
| Access Verification | Continuous authentication and authorization | One-time identity verification at login |
| Security Focus | Network segmentation, micro-segmentation, least privilege | Role-based access control (RBAC) and permissions |
| Threat Mitigation | Reduces lateral movement by limiting implicit trust | Depends on accurate identity and role management |
| Implementation Complexity | High - requires integration across systems and continuous monitoring | Moderate - centralized identity management systems |
| Use Case | Highly dynamic environments with varied devices and networks | Traditional corporate environments with defined roles |
| Examples | Google BeyondCorp, Microsoft Zero Trust | LDAP, Active Directory, Azure AD |
Which is better?
Zero Trust Architecture offers a more comprehensive security model by continuously verifying user identity, device health, and access permissions regardless of network location. Identity-Based Access Control (IBAC) focuses primarily on user identity for access decisions, making it less adaptive to dynamic threats and contextual factors. Organizations seeking robust, context-aware protection benefit more from Zero Trust frameworks than from traditional IBAC systems.
Connection
Zero Trust Architecture (ZTA) relies heavily on Identity-Based Access Control (IBAC) to enforce strict verification of user identities before granting access to resources. IBAC ensures that every access request is authenticated and authorized based on the user's identity and associated permissions, aligning perfectly with Zero Trust principles of "never trust, always verify." This integration reduces the risk of unauthorized access and enhances overall cybersecurity posture by continuously validating identities in dynamic IT environments.
Key Terms
Authentication
Identity-based access control (IBAC) emphasizes verifying a user's identity before granting access, often relying on static credentials such as usernames and passwords, which can be vulnerable to breaches if not properly managed. Zero Trust Architecture (ZTA) enhances authentication by continuously validating every access request using multi-factor authentication (MFA), context-aware policies, and real-time risk assessments to minimize trust assumptions. Explore how integrating adaptive authentication methods within these frameworks can strengthen security posture and reduce unauthorized access risks.
Least Privilege
Identity-based access control (IBAC) enforces permissions based on user identity, while zero trust architecture (ZTA) implements continuous verification and strict access limitations rooted in the principle of Least Privilege, minimizing exposure by granting only necessary permissions. ZTA enhances security through dynamic policy enforcement, reducing risks associated with static identity-based models prone to credential compromise. Explore how integrating Least Privilege within Zero Trust frameworks fortifies modern cybersecurity defenses.
Micro-Segmentation
Identity-based access control (IBAC) enforces security by granting access rights based on user identities and roles, while zero trust architecture (ZTA) employs continuous verification and micro-segmentation to limit lateral movement within networks. Micro-segmentation in zero trust divides the network into isolated segments, ensuring that even authenticated users access only specific resources based on strict policies, enhancing threat containment and reducing attack surfaces. Explore how micro-segmentation transforms access control by integrating identity verification with dynamic, granular network segmentation for robust security.
Source and External Links
What is Identity-Based Access Control (IBAC)? An Overview - Identity-Based Access Control (IBAC) is a security model where access to resources is granted based on a user's verified identity, using credentials like passwords, biometrics, or MFA for personalized and secure access control.
Benefits of Identity-Based Access Control (IAC) - InstaSafe - Identity-based access control allows organizations to deploy tailored access policies, track user activities, and ensure employees have appropriate access to technology and resources based on their digital identities.
What is Identity Access Management (IAM)? | Microsoft Security - Identity and access management (IAM) systems authenticate users against an identity database and enforce access controls, often requiring multifactor authentication for added security.
 dowidth.com
dowidth.com