Trustless computing leverages decentralized networks to enable secure transactions without relying on a trusted intermediary, enhancing transparency and reducing fraud risks. Homomorphic encryption allows computations to be performed directly on encrypted data, preserving privacy while enabling data analysis and processing. Explore the distinctions and applications of trustless computing and homomorphic encryption to understand their impact on secure technology solutions.
Why it is important
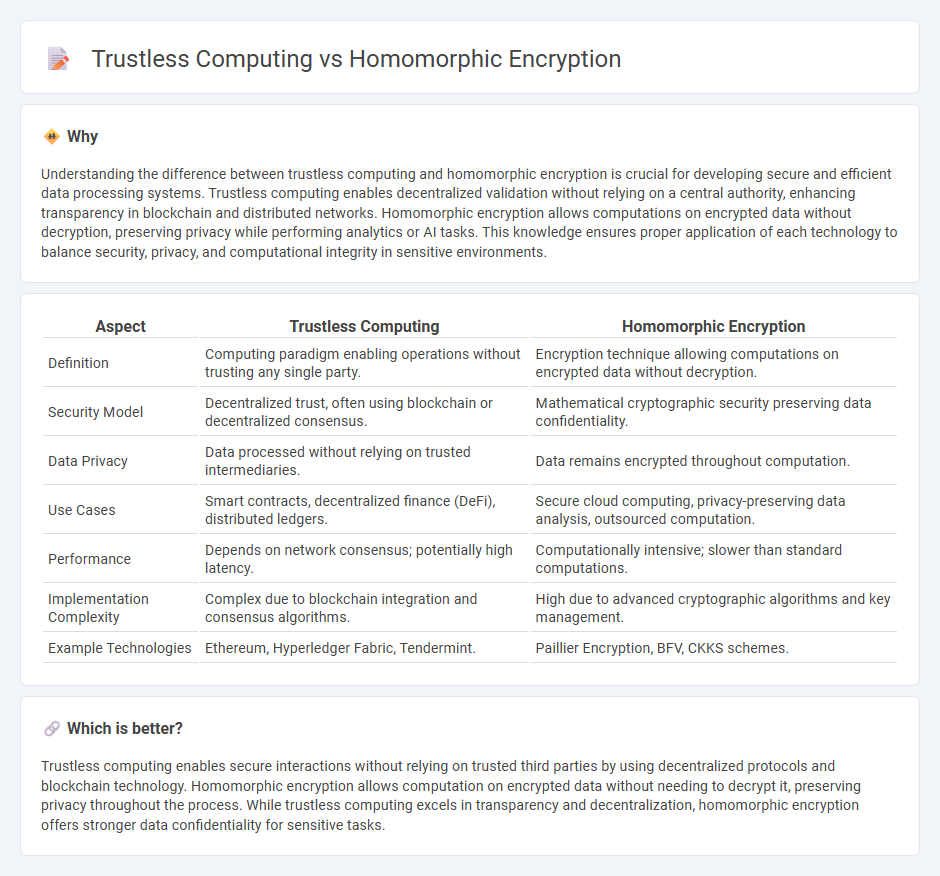
Understanding the difference between trustless computing and homomorphic encryption is crucial for developing secure and efficient data processing systems. Trustless computing enables decentralized validation without relying on a central authority, enhancing transparency in blockchain and distributed networks. Homomorphic encryption allows computations on encrypted data without decryption, preserving privacy while performing analytics or AI tasks. This knowledge ensures proper application of each technology to balance security, privacy, and computational integrity in sensitive environments.
Comparison Table
| Aspect | Trustless Computing | Homomorphic Encryption |
|---|---|---|
| Definition | Computing paradigm enabling operations without trusting any single party. | Encryption technique allowing computations on encrypted data without decryption. |
| Security Model | Decentralized trust, often using blockchain or decentralized consensus. | Mathematical cryptographic security preserving data confidentiality. |
| Data Privacy | Data processed without relying on trusted intermediaries. | Data remains encrypted throughout computation. |
| Use Cases | Smart contracts, decentralized finance (DeFi), distributed ledgers. | Secure cloud computing, privacy-preserving data analysis, outsourced computation. |
| Performance | Depends on network consensus; potentially high latency. | Computationally intensive; slower than standard computations. |
| Implementation Complexity | Complex due to blockchain integration and consensus algorithms. | High due to advanced cryptographic algorithms and key management. |
| Example Technologies | Ethereum, Hyperledger Fabric, Tendermint. | Paillier Encryption, BFV, CKKS schemes. |
Which is better?
Trustless computing enables secure interactions without relying on trusted third parties by using decentralized protocols and blockchain technology. Homomorphic encryption allows computation on encrypted data without needing to decrypt it, preserving privacy throughout the process. While trustless computing excels in transparency and decentralization, homomorphic encryption offers stronger data confidentiality for sensitive tasks.
Connection
Trustless computing relies on cryptographic methods to perform computations without requiring trust in any party, ensuring data privacy and integrity. Homomorphic encryption enables operations to be performed directly on encrypted data without decryption, making it a foundational technology for trustless environments. Integrating homomorphic encryption in trustless computing frameworks enhances secure data processing in multi-party systems and cloud-based applications.
Key Terms
Encrypted Computation
Homomorphic encryption enables computations to be performed directly on encrypted data without revealing the underlying plaintext, ensuring data privacy throughout the processing pipeline. Trustless computing leverages decentralized protocols and verifiable execution environments like blockchain or secure enclaves to guarantee computational integrity without relying on a central trusted party. Explore detailed comparisons and practical applications of encrypted computation by diving deeper into the evolving technologies shaping secure data processing.
Zero-Knowledge Proofs
Homomorphic encryption enables computations on encrypted data without revealing the underlying information, preserving privacy in cloud and distributed computing environments. Trustless computing leverages Zero-Knowledge Proofs (ZKPs) to verify the correctness of computations without exposing sensitive data or requiring trust in external parties. Explore the latest advancements in Zero-Knowledge Proofs to understand their role in enhancing secure, privacy-preserving computation frameworks.
Decentralization
Homomorphic encryption enables data processing on encrypted information without revealing raw data, enhancing privacy in decentralized systems by minimizing trust in third parties. Trustless computing relies on blockchain and consensus algorithms to eliminate the need for mutual trust, ensuring transparent and verifiable transactions in decentralized networks. Explore detailed comparisons on decentralization benefits and limitations in homomorphic encryption and trustless computing.
Source and External Links
Homomorphic encryption - Wikipedia - Homomorphic encryption is a form of encryption allowing computations on encrypted data without decryption, with results remaining encrypted.
What is homomorphic encryption, and why isn't it mainstream? - Homomorphic encryption algorithms let mathematical operations be performed directly on encrypted data, enabling processing while maintaining privacy.
What Is Homomorphic Encryption? - Chainlink - Homomorphic encryption comes in several types, from partially (supports only addition or multiplication) to fully (supports unlimited computations on encrypted data), though full schemes are computationally intensive.
 dowidth.com
dowidth.com