eBPF (extended Berkeley Packet Filter) offers powerful, programmable kernel-level event processing, enabling advanced security, monitoring, and networking functionalities beyond traditional methods. Seccomp (secure computing mode) provides a lightweight kernel feature restricting process system calls to minimize attack surfaces, primarily focusing on sandboxing. Explore the intricate differences and use cases of eBPF and seccomp to enhance your system security and performance strategies.
Why it is important
Understanding the difference between eBPF and seccomp is crucial for optimizing Linux kernel security and performance. eBPF enables advanced, programmable tracing and filtering capabilities, while seccomp provides a simpler, static syscall filtering mechanism for process isolation. Mastery of both tools allows developers to implement precise security policies and efficient monitoring tailored to specific application requirements. This knowledge enhances system stability, reduces attack surfaces, and improves resource utilization in modern computing environments.
Comparison Table
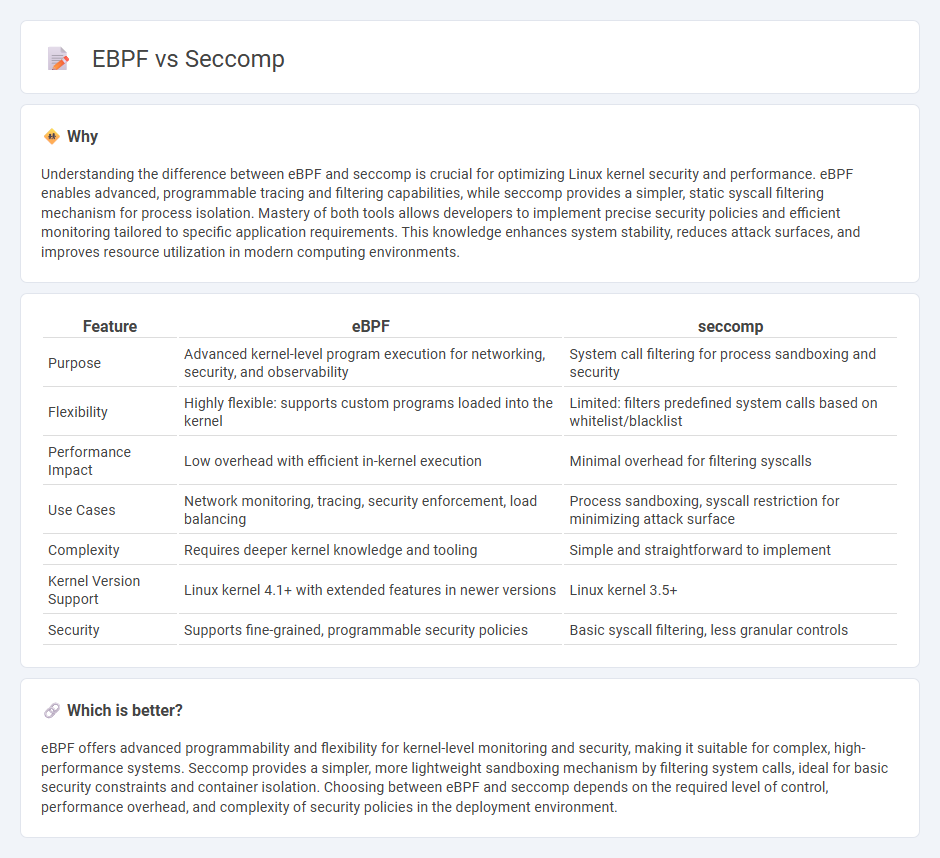
| Feature | eBPF | seccomp |
|---|---|---|
| Purpose | Advanced kernel-level program execution for networking, security, and observability | System call filtering for process sandboxing and security |
| Flexibility | Highly flexible: supports custom programs loaded into the kernel | Limited: filters predefined system calls based on whitelist/blacklist |
| Performance Impact | Low overhead with efficient in-kernel execution | Minimal overhead for filtering syscalls |
| Use Cases | Network monitoring, tracing, security enforcement, load balancing | Process sandboxing, syscall restriction for minimizing attack surface |
| Complexity | Requires deeper kernel knowledge and tooling | Simple and straightforward to implement |
| Kernel Version Support | Linux kernel 4.1+ with extended features in newer versions | Linux kernel 3.5+ |
| Security | Supports fine-grained, programmable security policies | Basic syscall filtering, less granular controls |
Which is better?
eBPF offers advanced programmability and flexibility for kernel-level monitoring and security, making it suitable for complex, high-performance systems. Seccomp provides a simpler, more lightweight sandboxing mechanism by filtering system calls, ideal for basic security constraints and container isolation. Choosing between eBPF and seccomp depends on the required level of control, performance overhead, and complexity of security policies in the deployment environment.
Connection
eBPF (extended Berkeley Packet Filter) and seccomp (secure computing mode) are connected through their roles in enhancing Linux kernel security by controlling system call filtering. eBPF extends seccomp's capabilities by allowing more complex and dynamic filtering rules beyond simple syscall blocklists, enabling detailed introspection and monitoring of kernel and application behavior. Together, they provide a powerful framework for enforcing security policies and improving performance in containerized and cloud-native environments.
Key Terms
Sandbox
Seccomp provides a lightweight sandbox by restricting system calls through a kernel filter that enforces a fixed whitelist, enhancing security with minimal overhead. eBPF offers a more versatile and dynamic sandboxing mechanism, enabling custom, programmable filtering and monitoring with greater flexibility in handling system events. Explore deeper to understand how these technologies complement sandboxing strategies for container and application security.
System Calls
Seccomp provides a straightforward filtering mechanism for system calls by allowing or denying specific syscalls, primarily for enhancing container security with minimal overhead. eBPF offers a more flexible and programmable approach to system call interception, enabling complex logic and dynamic filtering beyond simple allow/deny rules. Explore the detailed capabilities and use cases of seccomp and eBPF in system call management to optimize your security strategy.
Kernel Filtering
seccomp uses predefined sandboxing filters based on system call numbers to restrict a process's capabilities, providing a lightweight, secure kernel-level filtering mechanism. eBPF enables complex, customizable packet and event processing with programmable bytecode running in the kernel, supporting dynamic filtering and advanced telemetry beyond basic syscall restrictions. Explore detailed comparisons of seccomp and eBPF for kernel filtering to optimize Linux security and performance solutions.
Source and External Links
Seccomp - Wikipedia - Seccomp (secure computing) is a Linux kernel security feature allowing a process to enter a restricted mode where it can only make a small set of system calls (exit, sigreturn, read, write), with seccomp-bpf as an extension enabling flexible syscall filtering via Berkeley Packet Filter rules.
What is Seccomp in Kubernetes? - ARMO - Seccomp is a Linux kernel mechanism that restricts system calls available to a process, significantly reducing attack surface in containerized environments like Kubernetes by enforcing default or custom system call filters.
Chapter 8. Linux Capabilities and Seccomp - Red Hat - Seccomp allows filtering system calls from containers using profiles that can be customized to block unsafe calls, implemented via Berkeley Packet Filter programs, providing fine-grained syscall control beyond Linux capabilities.
 dowidth.com
dowidth.com