Homomorphic encryption enables computations on encrypted data without revealing the raw information, making it vital for secure cloud computing and privacy-preserving data analysis. Quantum cryptography leverages quantum mechanics principles to achieve theoretically unbreakable encryption, with Quantum Key Distribution (QKD) as its most prominent application. Explore how these cutting-edge technologies are shaping the future of cybersecurity and data protection.
Why it is important
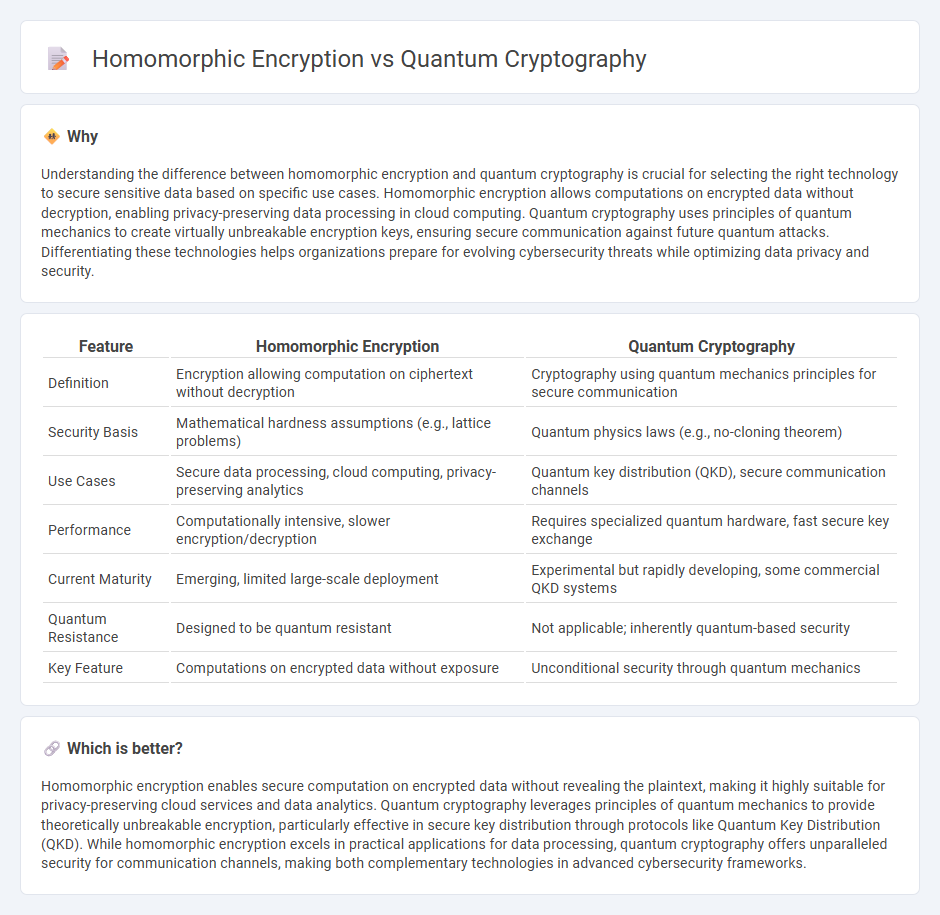
Understanding the difference between homomorphic encryption and quantum cryptography is crucial for selecting the right technology to secure sensitive data based on specific use cases. Homomorphic encryption allows computations on encrypted data without decryption, enabling privacy-preserving data processing in cloud computing. Quantum cryptography uses principles of quantum mechanics to create virtually unbreakable encryption keys, ensuring secure communication against future quantum attacks. Differentiating these technologies helps organizations prepare for evolving cybersecurity threats while optimizing data privacy and security.
Comparison Table
| Feature | Homomorphic Encryption | Quantum Cryptography |
|---|---|---|
| Definition | Encryption allowing computation on ciphertext without decryption | Cryptography using quantum mechanics principles for secure communication |
| Security Basis | Mathematical hardness assumptions (e.g., lattice problems) | Quantum physics laws (e.g., no-cloning theorem) |
| Use Cases | Secure data processing, cloud computing, privacy-preserving analytics | Quantum key distribution (QKD), secure communication channels |
| Performance | Computationally intensive, slower encryption/decryption | Requires specialized quantum hardware, fast secure key exchange |
| Current Maturity | Emerging, limited large-scale deployment | Experimental but rapidly developing, some commercial QKD systems |
| Quantum Resistance | Designed to be quantum resistant | Not applicable; inherently quantum-based security |
| Key Feature | Computations on encrypted data without exposure | Unconditional security through quantum mechanics |
Which is better?
Homomorphic encryption enables secure computation on encrypted data without revealing the plaintext, making it highly suitable for privacy-preserving cloud services and data analytics. Quantum cryptography leverages principles of quantum mechanics to provide theoretically unbreakable encryption, particularly effective in secure key distribution through protocols like Quantum Key Distribution (QKD). While homomorphic encryption excels in practical applications for data processing, quantum cryptography offers unparalleled security for communication channels, making both complementary technologies in advanced cybersecurity frameworks.
Connection
Homomorphic encryption and quantum cryptography are connected through their shared goal of enhancing data security in computing and communication. Homomorphic encryption allows computations on encrypted data without decryption, ensuring privacy in cloud computing, while quantum cryptography uses principles of quantum mechanics to secure communications against eavesdropping. Both technologies represent advanced cryptographic methods that address emerging threats posed by quantum computing and the need for secure data processing.
Key Terms
Qubit
Quantum cryptography leverages the principles of quantum mechanics, utilizing qubits to ensure secure communication through quantum key distribution, which is inherently resistant to eavesdropping. Homomorphic encryption, on the other hand, allows computations on encrypted classical data but does not directly involve qubits, relying instead on complex mathematical algorithms for data privacy. Explore the distinctions and applications of qubit-based quantum cryptography versus classical homomorphic encryption to gain deeper insights into future-proof security technologies.
Secure Multiparty Computation
Quantum cryptography leverages principles of quantum mechanics to enable secure key distribution, making it inherently resistant to eavesdropping during communication, while homomorphic encryption allows computations on encrypted data without revealing the underlying information, supporting privacy in multiparty computations. Secure Multiparty Computation (SMPC) benefits from homomorphic encryption by enabling participants to jointly compute functions over their inputs while keeping those inputs private, whereas quantum cryptography enhances secure communication channels but does not perform encrypted computations directly. Explore how integrating quantum cryptographic protocols with homomorphic encryption can revolutionize SMPC by combining secure data transmission and privacy-preserving computation techniques.
Quantum Key Distribution (QKD)
Quantum Key Distribution (QKD) leverages quantum mechanics principles to enable secure communication by generating and sharing cryptographic keys that are theoretically immune to eavesdropping. Unlike homomorphic encryption, which allows computations on encrypted data without decryption, QKD ensures key exchange security through quantum states, making interception detectable. Explore the fundamental differences and advantages of QKD in quantum cryptography to enhance your understanding of next-generation secure communication methods.
Source and External Links
Classical vs. Quantum vs. Post-Quantum Cryptography - Quantum cryptography uses qubits and the unpredictable quantum nature of matter to securely encrypt messages and detect eavesdropping, offering security beyond what classical methods like AES and PKC can provide.
What Is Quantum Cryptography? - Quantum cryptography harnesses quantum mechanics principles such as superposition and entanglement to securely encrypt and transmit data, enabling methods like blind quantum computing that protect data even during processing on remote servers.
What Is Quantum Cryptography? - Quantum key distribution (QKD) allows two parties to create secure cryptographic keys using quantum states of photons, making any eavesdropping detectable and thus the encrypted communication effectively unhackable.
 dowidth.com
dowidth.com