Zero Trust and Defense in Depth represent two pivotal cybersecurity frameworks designed to protect digital assets from evolving threats. Zero Trust operates on the principle of "never trust, always verify," ensuring continuous validation of user identities and devices, while Defense in Depth employs multiple layers of security controls to create redundancies that thwart unauthorized access. Explore the nuances and applications of these strategies to enhance your cybersecurity posture.
Why it is important
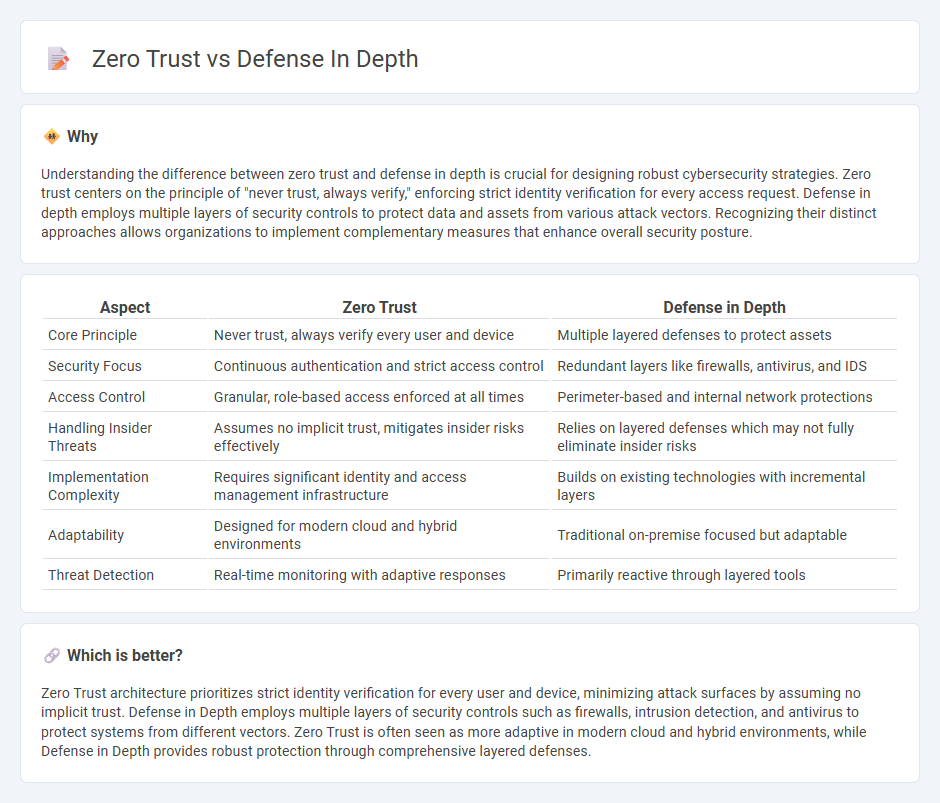
Understanding the difference between zero trust and defense in depth is crucial for designing robust cybersecurity strategies. Zero trust centers on the principle of "never trust, always verify," enforcing strict identity verification for every access request. Defense in depth employs multiple layers of security controls to protect data and assets from various attack vectors. Recognizing their distinct approaches allows organizations to implement complementary measures that enhance overall security posture.
Comparison Table
| Aspect | Zero Trust | Defense in Depth |
|---|---|---|
| Core Principle | Never trust, always verify every user and device | Multiple layered defenses to protect assets |
| Security Focus | Continuous authentication and strict access control | Redundant layers like firewalls, antivirus, and IDS |
| Access Control | Granular, role-based access enforced at all times | Perimeter-based and internal network protections |
| Handling Insider Threats | Assumes no implicit trust, mitigates insider risks effectively | Relies on layered defenses which may not fully eliminate insider risks |
| Implementation Complexity | Requires significant identity and access management infrastructure | Builds on existing technologies with incremental layers |
| Adaptability | Designed for modern cloud and hybrid environments | Traditional on-premise focused but adaptable |
| Threat Detection | Real-time monitoring with adaptive responses | Primarily reactive through layered tools |
Which is better?
Zero Trust architecture prioritizes strict identity verification for every user and device, minimizing attack surfaces by assuming no implicit trust. Defense in Depth employs multiple layers of security controls such as firewalls, intrusion detection, and antivirus to protect systems from different vectors. Zero Trust is often seen as more adaptive in modern cloud and hybrid environments, while Defense in Depth provides robust protection through comprehensive layered defenses.
Connection
Zero trust and defense in depth are interconnected cybersecurity strategies that enhance organizational security by minimizing risk through multiple layers of protection and continuous verification. Zero trust enforces strict access controls by assuming no user or device is trusted by default, while defense in depth employs redundant security measures such as firewalls, intrusion detection systems, and endpoint protection. Together, they create a robust security posture that addresses vulnerabilities at various points in the network and prevents unauthorized access.
Key Terms
Layered Security
Defense in depth employs multiple, overlapping security layers to protect systems by combining firewalls, intrusion detection, antivirus software, and physical controls, creating redundant barriers to mitigate threats. Zero trust architecture eliminates implicit trust by continuously verifying every user and device, enforcing strict access controls regardless of location within or outside the network perimeter. Explore how integrating these strategies enhances organizational resilience by reducing vulnerabilities and improving threat detection.
Least Privilege
Defense in depth employs multiple security layers to protect assets, while zero trust centers on continuous verification and strict access controls based on least privilege. Least privilege ensures users and systems have only the minimum access necessary, reducing the risk of lateral movement in both models. Explore how integrating least privilege enhances security frameworks by visiting our detailed guide.
Continuous Verification
Defense in Depth employs multiple layered security measures to protect systems, while Zero Trust emphasizes continuous verification of user identities and device health before granting access. Continuous verification in Zero Trust enforces strict authentication protocols at every access attempt, reducing risks from insider threats and compromised credentials. Explore deeper into Continuous Verification to understand its critical role in modern cybersecurity frameworks.
Source and External Links
Defense in depth (computing) - Wikipedia - Defense in depth is an information security concept where multiple layers of security controls are placed throughout an IT system to provide redundancy in case one control fails, covering physical, technical, and administrative measures.
What is Defense-in-Depth? - Definition - CyberArk - A defense-in-depth strategy uses overlapping layers of security to holistically protect against cyber threats, so if one layer is breached, others can still contain the attack and reduce risk.
What Is Defense In Depth? Best Practices For Layered Security - Wiz - Defense in depth is a layered cybersecurity strategy that employs multiple, overlapping security mechanisms to prevent full system penetration, ensuring that a breach in one control is stopped by others.
 dowidth.com
dowidth.com