Trustless computing enables secure transactions without relying on a trusted intermediary by using cryptographic protocols like blockchain and zero-knowledge proofs. Confidential computing protects data in use by isolating it within secure enclaves, ensuring privacy even during processing. Explore the differences and applications of trustless and confidential computing to understand their impact on data security.
Why it is important
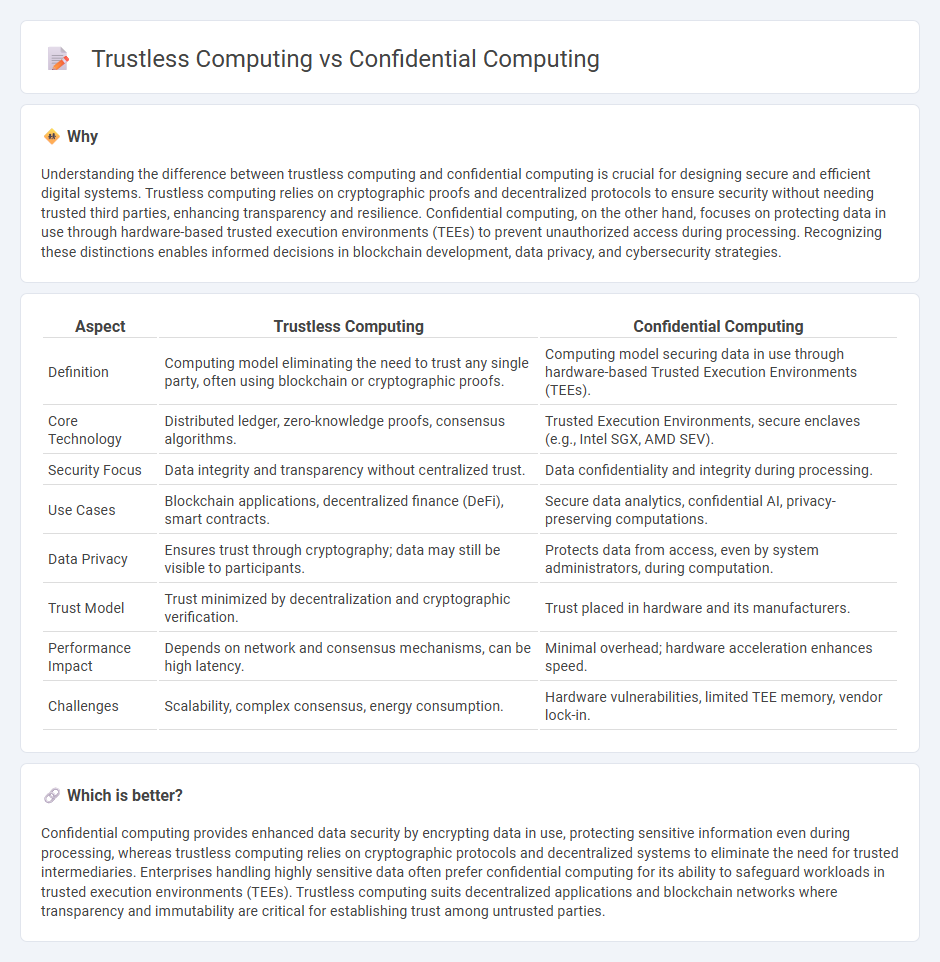
Understanding the difference between trustless computing and confidential computing is crucial for designing secure and efficient digital systems. Trustless computing relies on cryptographic proofs and decentralized protocols to ensure security without needing trusted third parties, enhancing transparency and resilience. Confidential computing, on the other hand, focuses on protecting data in use through hardware-based trusted execution environments (TEEs) to prevent unauthorized access during processing. Recognizing these distinctions enables informed decisions in blockchain development, data privacy, and cybersecurity strategies.
Comparison Table
| Aspect | Trustless Computing | Confidential Computing |
|---|---|---|
| Definition | Computing model eliminating the need to trust any single party, often using blockchain or cryptographic proofs. | Computing model securing data in use through hardware-based Trusted Execution Environments (TEEs). |
| Core Technology | Distributed ledger, zero-knowledge proofs, consensus algorithms. | Trusted Execution Environments, secure enclaves (e.g., Intel SGX, AMD SEV). |
| Security Focus | Data integrity and transparency without centralized trust. | Data confidentiality and integrity during processing. |
| Use Cases | Blockchain applications, decentralized finance (DeFi), smart contracts. | Secure data analytics, confidential AI, privacy-preserving computations. |
| Data Privacy | Ensures trust through cryptography; data may still be visible to participants. | Protects data from access, even by system administrators, during computation. |
| Trust Model | Trust minimized by decentralization and cryptographic verification. | Trust placed in hardware and its manufacturers. |
| Performance Impact | Depends on network and consensus mechanisms, can be high latency. | Minimal overhead; hardware acceleration enhances speed. |
| Challenges | Scalability, complex consensus, energy consumption. | Hardware vulnerabilities, limited TEE memory, vendor lock-in. |
Which is better?
Confidential computing provides enhanced data security by encrypting data in use, protecting sensitive information even during processing, whereas trustless computing relies on cryptographic protocols and decentralized systems to eliminate the need for trusted intermediaries. Enterprises handling highly sensitive data often prefer confidential computing for its ability to safeguard workloads in trusted execution environments (TEEs). Trustless computing suits decentralized applications and blockchain networks where transparency and immutability are critical for establishing trust among untrusted parties.
Connection
Trustless computing relies on cryptographic protocols to enable secure transactions without trusting parties, while Confidential computing ensures data privacy by processing information in isolated, hardware-protected environments. Both technologies aim to enhance security and data integrity in distributed systems by minimizing trust assumptions. Their integration supports secure and private computation in decentralized applications and cloud environments.
Key Terms
**Trusted Execution Environment (TEE)**
Trusted Execution Environment (TEE) provides a hardware-isolated secure area that ensures confidentiality and integrity of code and data during execution, making it a cornerstone of confidential computing. Trustless computing, in contrast, leverages cryptographic proofs and decentralized consensus to enable secure computation without relying on any single hardware trust anchor. Explore the intricacies of TEE in confidential computing to understand how it safeguards sensitive workloads against insider threats and unauthorized access.
**Zero-Knowledge Proofs**
Zero-Knowledge Proofs (ZKPs) enable trustless computing by allowing one party to prove knowledge of information without revealing the data itself, enhancing privacy and security in blockchain and decentralized applications. Confidential computing leverages hardware-based Trusted Execution Environments (TEEs) to protect data in use, ensuring computations remain secure even in potentially compromised systems. Explore the critical distinctions and synergies between confidential and trustless computing with zero-knowledge proofs to deepen your understanding of modern data privacy solutions.
**Hardware Root of Trust**
Confidential computing relies on a Hardware Root of Trust (RoT) to establish a secure and immutable foundation within the hardware, enabling encrypted data processing inside trusted execution environments (TEEs). Trustless computing, in contrast, does not depend on any single hardware component's integrity but uses decentralized consensus and cryptographic proofs to ensure system security. Explore how these fundamentally different approaches impact your organization's data confidentiality and integrity strategies.
Source and External Links
What Is Confidential Computing? - Confidential computing processes data inside a secure processor zone called a Trusted Execution Environment (TEE) where data is encrypted, decrypted, and computed without exposing it to the machine owner or software, with security verified by attestation.
What Is Confidential Computing? - Confidential computing isolates sensitive data in protected CPU enclaves during processing, ensuring data in use is encrypted and accessible only to authorized code, thus providing security beyond existing protections for data at rest and in transit.
Azure Confidential Computing Overview - Confidential computing extends data protection by performing computations in hardware-based, attested TEEs that prevent unauthorized access or modification while data is in use, including blocking access from cloud providers themselves.
 dowidth.com
dowidth.com