Zero Trust Architecture enforces strict identity verification for every user and device, regardless of their location, minimizing security risks in complex network environments. Certificate-based authentication relies on digital certificates to establish trust, often used in traditional security models but susceptible to certificate theft or mismanagement. Explore the key differences and benefits of these approaches to enhance your cybersecurity strategy.
Why it is important
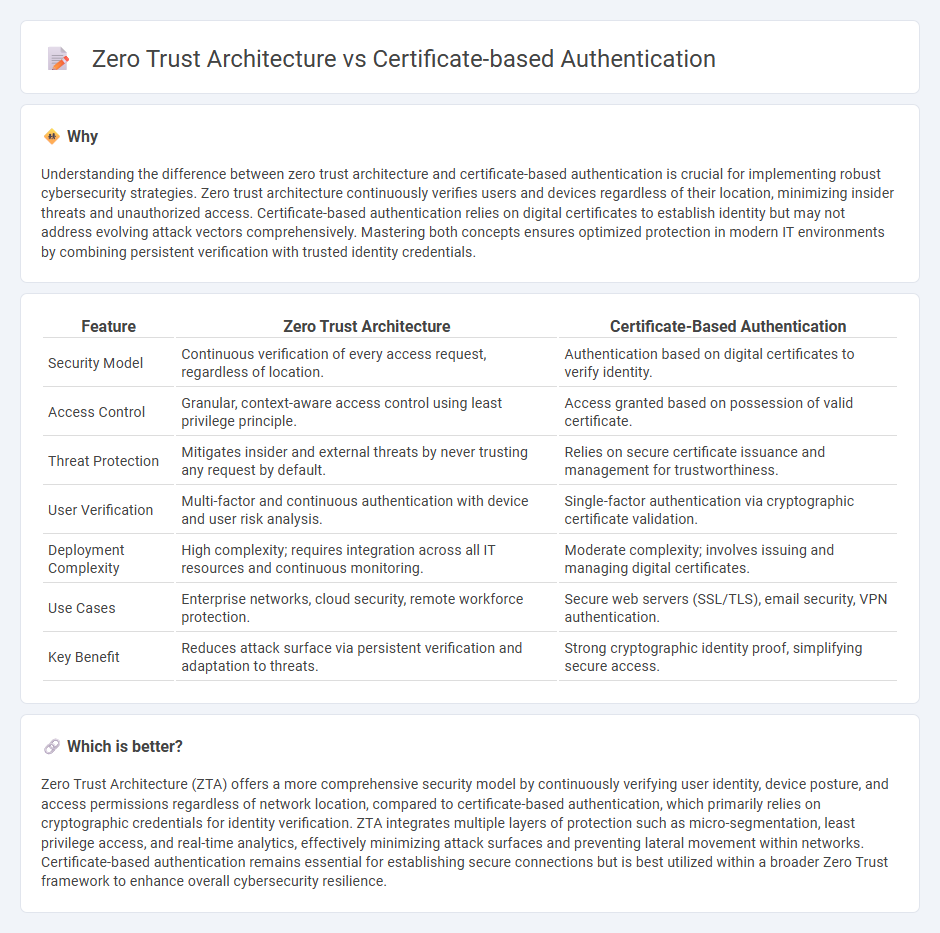
Understanding the difference between zero trust architecture and certificate-based authentication is crucial for implementing robust cybersecurity strategies. Zero trust architecture continuously verifies users and devices regardless of their location, minimizing insider threats and unauthorized access. Certificate-based authentication relies on digital certificates to establish identity but may not address evolving attack vectors comprehensively. Mastering both concepts ensures optimized protection in modern IT environments by combining persistent verification with trusted identity credentials.
Comparison Table
| Feature | Zero Trust Architecture | Certificate-Based Authentication |
|---|---|---|
| Security Model | Continuous verification of every access request, regardless of location. | Authentication based on digital certificates to verify identity. |
| Access Control | Granular, context-aware access control using least privilege principle. | Access granted based on possession of valid certificate. |
| Threat Protection | Mitigates insider and external threats by never trusting any request by default. | Relies on secure certificate issuance and management for trustworthiness. |
| User Verification | Multi-factor and continuous authentication with device and user risk analysis. | Single-factor authentication via cryptographic certificate validation. |
| Deployment Complexity | High complexity; requires integration across all IT resources and continuous monitoring. | Moderate complexity; involves issuing and managing digital certificates. |
| Use Cases | Enterprise networks, cloud security, remote workforce protection. | Secure web servers (SSL/TLS), email security, VPN authentication. |
| Key Benefit | Reduces attack surface via persistent verification and adaptation to threats. | Strong cryptographic identity proof, simplifying secure access. |
Which is better?
Zero Trust Architecture (ZTA) offers a more comprehensive security model by continuously verifying user identity, device posture, and access permissions regardless of network location, compared to certificate-based authentication, which primarily relies on cryptographic credentials for identity verification. ZTA integrates multiple layers of protection such as micro-segmentation, least privilege access, and real-time analytics, effectively minimizing attack surfaces and preventing lateral movement within networks. Certificate-based authentication remains essential for establishing secure connections but is best utilized within a broader Zero Trust framework to enhance overall cybersecurity resilience.
Connection
Zero Trust Architecture relies heavily on certificate-based authentication to verify every user and device attempting to access network resources, ensuring strict identity validation without implicit trust. Certificates act as digital identities that constantly authenticate endpoints, preventing unauthorized access in a perimeter-less security model. This integration strengthens security by continuously validating credentials, aligning with Zero Trust's core principle of "never trust, always verify.
Key Terms
Digital Certificates
Digital certificates serve as a cornerstone in certificate-based authentication by providing cryptographic proof of identity, allowing systems to verify users or devices through a trusted certificate authority (CA). Zero Trust Architecture, while leveraging digital certificates, expands security by enforcing strict continuous verification of identities and device health across all network access points, minimizing implicit trust. Explore the nuances of digital certificates' role in evolving security frameworks to enhance your understanding.
Least Privilege
Certificate-based authentication enforces identity verification through digital certificates, enabling secure access control by proving user or device legitimacy. Zero Trust Architecture enhances this by continuously validating trust and strictly adhering to the Least Privilege principle, ensuring users or devices have minimal access rights required for tasks. Explore how integrating certificate-based authentication within Zero Trust frameworks strengthens Least Privilege enforcement for robust cybersecurity.
Continuous Verification
Certificate-based authentication relies on digital certificates to verify user identities during initial access, providing strong cryptographic assurance but often lacking ongoing session validation. Zero Trust Architecture enforces continuous verification by constantly evaluating user behavior, device health, and contextual factors to adapt access permissions dynamically, minimizing the risk of insider threats and lateral movement. Explore detailed strategies for implementing continuous verification in modern security frameworks to enhance protection and compliance.
Source and External Links
What is Certificate-Based Authentication | Yubico - Certificate-based authentication uses digital certificates to securely identify users, devices, or machines before granting access to applications or networks.
Boost Security with Certificate-Based Authentication - Ping Identity - Certificate-based authentication involves using digital certificates to prove identity by verifying ownership of a private key, enhancing security through public key cryptography.
What is certificate-based authentication? - OneLogin - Certificate-based authentication uses digital certificates to verify identities, providing a secure method to authenticate users, devices, or servers before accessing networks or applications.
 dowidth.com
dowidth.com