Flood risk modeling leverages hydrological data, geographic information systems, and climate patterns to predict potential flood events and assess property vulnerabilities with spatial precision. Cyber risk modeling analyzes threat intelligence, network vulnerabilities, and historical cyber attack data to quantify potential financial impacts on digital assets and inform mitigation strategies. Explore the differences and applications of these risk modeling approaches to enhance your insurance strategies.
Why it is important
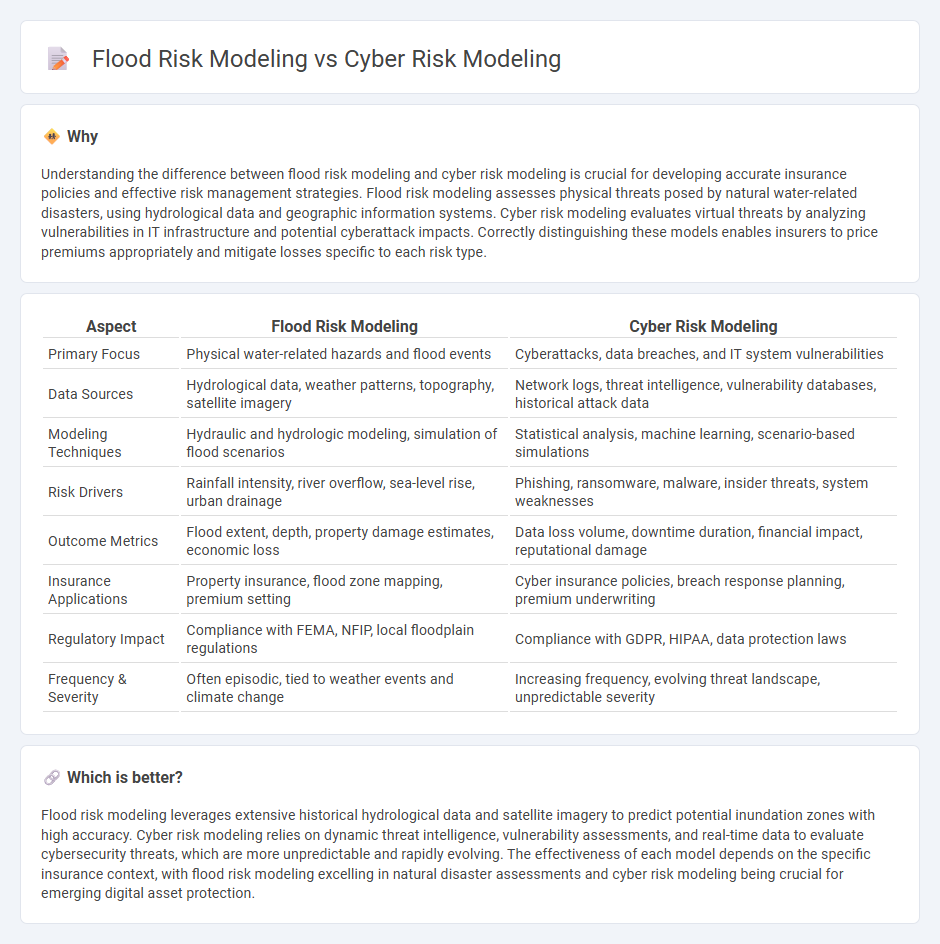
Understanding the difference between flood risk modeling and cyber risk modeling is crucial for developing accurate insurance policies and effective risk management strategies. Flood risk modeling assesses physical threats posed by natural water-related disasters, using hydrological data and geographic information systems. Cyber risk modeling evaluates virtual threats by analyzing vulnerabilities in IT infrastructure and potential cyberattack impacts. Correctly distinguishing these models enables insurers to price premiums appropriately and mitigate losses specific to each risk type.
Comparison Table
| Aspect | Flood Risk Modeling | Cyber Risk Modeling |
|---|---|---|
| Primary Focus | Physical water-related hazards and flood events | Cyberattacks, data breaches, and IT system vulnerabilities |
| Data Sources | Hydrological data, weather patterns, topography, satellite imagery | Network logs, threat intelligence, vulnerability databases, historical attack data |
| Modeling Techniques | Hydraulic and hydrologic modeling, simulation of flood scenarios | Statistical analysis, machine learning, scenario-based simulations |
| Risk Drivers | Rainfall intensity, river overflow, sea-level rise, urban drainage | Phishing, ransomware, malware, insider threats, system weaknesses |
| Outcome Metrics | Flood extent, depth, property damage estimates, economic loss | Data loss volume, downtime duration, financial impact, reputational damage |
| Insurance Applications | Property insurance, flood zone mapping, premium setting | Cyber insurance policies, breach response planning, premium underwriting |
| Regulatory Impact | Compliance with FEMA, NFIP, local floodplain regulations | Compliance with GDPR, HIPAA, data protection laws |
| Frequency & Severity | Often episodic, tied to weather events and climate change | Increasing frequency, evolving threat landscape, unpredictable severity |
Which is better?
Flood risk modeling leverages extensive historical hydrological data and satellite imagery to predict potential inundation zones with high accuracy. Cyber risk modeling relies on dynamic threat intelligence, vulnerability assessments, and real-time data to evaluate cybersecurity threats, which are more unpredictable and rapidly evolving. The effectiveness of each model depends on the specific insurance context, with flood risk modeling excelling in natural disaster assessments and cyber risk modeling being crucial for emerging digital asset protection.
Connection
Flood risk modeling and cyber risk modeling are connected through their reliance on advanced data analytics and predictive algorithms to assess vulnerabilities and potential financial impacts. Both employ machine learning techniques to analyze historical data, identify patterns, and forecast risk scenarios, enabling insurers to develop tailored risk management strategies. Integrating physical risks like flooding with digital threats enhances comprehensive insurance underwriting and resilience planning.
Key Terms
**Cyber risk modeling:**
Cyber risk modeling quantifies potential financial losses from cyberattacks by analyzing threat vectors, vulnerability exposures, and attack frequencies using probabilistic and statistical methods. It incorporates real-time data from cybersecurity incidents, threat intelligence, and system architecture to estimate breach impacts and response costs, enabling businesses to optimize cybersecurity investments. Explore detailed methodologies and advanced tools in cyber risk modeling for enhanced enterprise protection.
Data Breach
Cyber risk modeling for data breaches analyzes threat vectors, vulnerability assessments, and breach impact metrics to quantify potential financial and operational damages. Flood risk modeling incorporates hydrological data, infrastructure resilience, and historical flood events to predict property damage and loss probabilities. Explore comprehensive comparisons to understand methodologies and mitigation strategies in these distinct risk domains.
Malware Attack Vector
Cyber risk modeling for malware attack vectors involves analyzing threat landscapes, payload delivery mechanisms, and vulnerabilities within networks to estimate potential financial and operational impacts. Flood risk modeling assesses hydrological data, terrain elevation, and floodplain mapping to predict inundation extents and associated damages. Explore detailed methodologies and comparative analytics between cyber and flood risk models to enhance your risk management strategies.
Source and External Links
An Overview of Cyber Risk Modeling - Kovrr - Cyber risk modeling is a data-driven process that identifies, simulates tens of thousands of potential cyber threats, and quantifies their business impact to help organizations translate cyber risks into actionable insights and financial metrics like Average Annual Loss (AAL), enabling proactive risk management and investment justification.
What is Risk Modeling? - Centraleyes - Cyber risk modeling involves creating hypothetical risk scenarios and quantifying their potential severity on the business by blending real-world threat intelligence with data on digital assets and security posture, allowing organizations to simulate events like ransomware attacks to assess financial impact and prioritize risk reduction efforts.
Kovrr: Cyber Risk Quantification and Risk Management - Kovrr's cyber risk modeling approach uses proprietary and third-party data sources to run thousands of simulations across business-impact scenarios, producing a financial risk overview including loss analysis, security control effectiveness, and recommendations for risk mitigation, integrating contextual industry data and cyber posture for comprehensive risk insights.
 dowidth.com
dowidth.com