Quantum-safe cryptography employs algorithms designed to resist attacks from quantum computers, ensuring long-term data security beyond the capabilities of traditional key exchange protocols like Diffie-Hellman. Key exchange protocols facilitate secure sharing of encryption keys but remain vulnerable to quantum attacks due to underlying mathematical assumptions. Explore the advancements in quantum-safe cryptographic techniques to safeguard future communications.
Why it is important
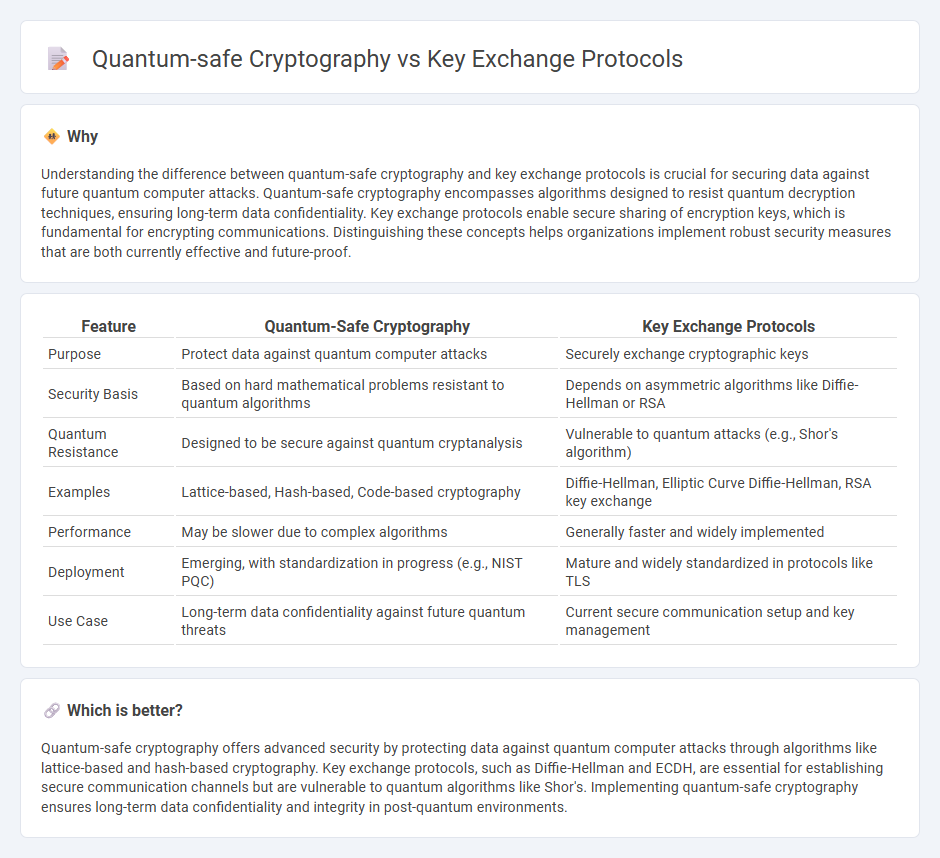
Understanding the difference between quantum-safe cryptography and key exchange protocols is crucial for securing data against future quantum computer attacks. Quantum-safe cryptography encompasses algorithms designed to resist quantum decryption techniques, ensuring long-term data confidentiality. Key exchange protocols enable secure sharing of encryption keys, which is fundamental for encrypting communications. Distinguishing these concepts helps organizations implement robust security measures that are both currently effective and future-proof.
Comparison Table
| Feature | Quantum-Safe Cryptography | Key Exchange Protocols |
|---|---|---|
| Purpose | Protect data against quantum computer attacks | Securely exchange cryptographic keys |
| Security Basis | Based on hard mathematical problems resistant to quantum algorithms | Depends on asymmetric algorithms like Diffie-Hellman or RSA |
| Quantum Resistance | Designed to be secure against quantum cryptanalysis | Vulnerable to quantum attacks (e.g., Shor's algorithm) |
| Examples | Lattice-based, Hash-based, Code-based cryptography | Diffie-Hellman, Elliptic Curve Diffie-Hellman, RSA key exchange |
| Performance | May be slower due to complex algorithms | Generally faster and widely implemented |
| Deployment | Emerging, with standardization in progress (e.g., NIST PQC) | Mature and widely standardized in protocols like TLS |
| Use Case | Long-term data confidentiality against future quantum threats | Current secure communication setup and key management |
Which is better?
Quantum-safe cryptography offers advanced security by protecting data against quantum computer attacks through algorithms like lattice-based and hash-based cryptography. Key exchange protocols, such as Diffie-Hellman and ECDH, are essential for establishing secure communication channels but are vulnerable to quantum algorithms like Shor's. Implementing quantum-safe cryptography ensures long-term data confidentiality and integrity in post-quantum environments.
Connection
Quantum-safe cryptography relies on advanced key exchange protocols designed to withstand attacks from quantum computers by using mathematical problems incompatible with quantum algorithms. These protocols enable secure communication channels that protect cryptographic keys against quantum threats, ensuring data confidentiality and integrity. Implementations like lattice-based and hash-based key exchange schemes are central to establishing quantum-resistant security frameworks in emerging technologies.
Key Terms
Diffie-Hellman
Diffie-Hellman key exchange protocol, widely used for secure communication, faces vulnerabilities against quantum computing attacks due to its reliance on discrete logarithm problems. Quantum-safe cryptography, including lattice-based and hash-based schemes, offers robust alternatives designed to withstand quantum threats by leveraging mathematically complex problems resistant to quantum algorithms. Explore more about advancements in quantum-resistant cryptographic techniques and their impact on securing future communications.
Post-Quantum Cryptography
Post-Quantum Cryptography (PQC) addresses vulnerabilities in traditional key exchange protocols exposed by quantum computing threats, utilizing algorithms resistant to quantum attacks such as lattice-based, hash-based, code-based, and multivariate polynomial cryptography. These quantum-safe cryptographic methods ensure data confidentiality and integrity against potential breaches from quantum-enabled adversaries, making PQC essential for future-proof secure communications. Explore the evolving field of Post-Quantum Cryptography to understand how it safeguards digital assets in a quantum era.
Lattice-based Cryptography
Key exchange protocols such as Diffie-Hellman face vulnerabilities against quantum attacks, making quantum-safe cryptography essential for future-proof security. Lattice-based cryptography provides a robust framework for secure key exchange, leveraging mathematical problems believed to be resistant to quantum computing threats. Explore the advancements in lattice-based cryptographic algorithms to understand how they secure communication in the post-quantum era.
Source and External Links
What Are Cryptographic Key Exchange Protocols? - ITU Online - Cryptographic key exchange protocols, such as Diffie-Hellman, are methods for securely sharing cryptographic keys between parties over insecure channels, allowing them to generate shared secrets without transmitting them directly; Diffie-Hellman relies on the discrete logarithm problem for its security but requires additional authentication to prevent man-in-the-middle attacks.
Key Exchange Protocols - Oracle Help Center - Key exchange protocols like IKEv1 combine methods such as ISAKMP and Oakley to negotiate security associations and keys for secure IPsec communication, using phases that establish authentication and symmetric encryption with Diffie-Hellman as the underlying key agreement method.
What Is A Key Exchange? | JSCAPE - The most popular key exchange algorithms are RSA and Diffie-Hellman (now Diffie-Hellman-Merkle), enabling secure key exchanges over insecure media, while newer protocols include elliptic curve methods like ECDH and ECDHE for improved security and efficiency.
 dowidth.com
dowidth.com