Post-quantum cryptography develops algorithms designed to secure data against attacks from future quantum computers by leveraging classical computational principles resistant to quantum decryption techniques. Quantum key distribution uses the properties of quantum mechanics to enable two parties to generate a shared, secret key with provable security based on the laws of physics. Explore further to understand the critical differences and applications of these cutting-edge technologies in securing digital communication.
Why it is important
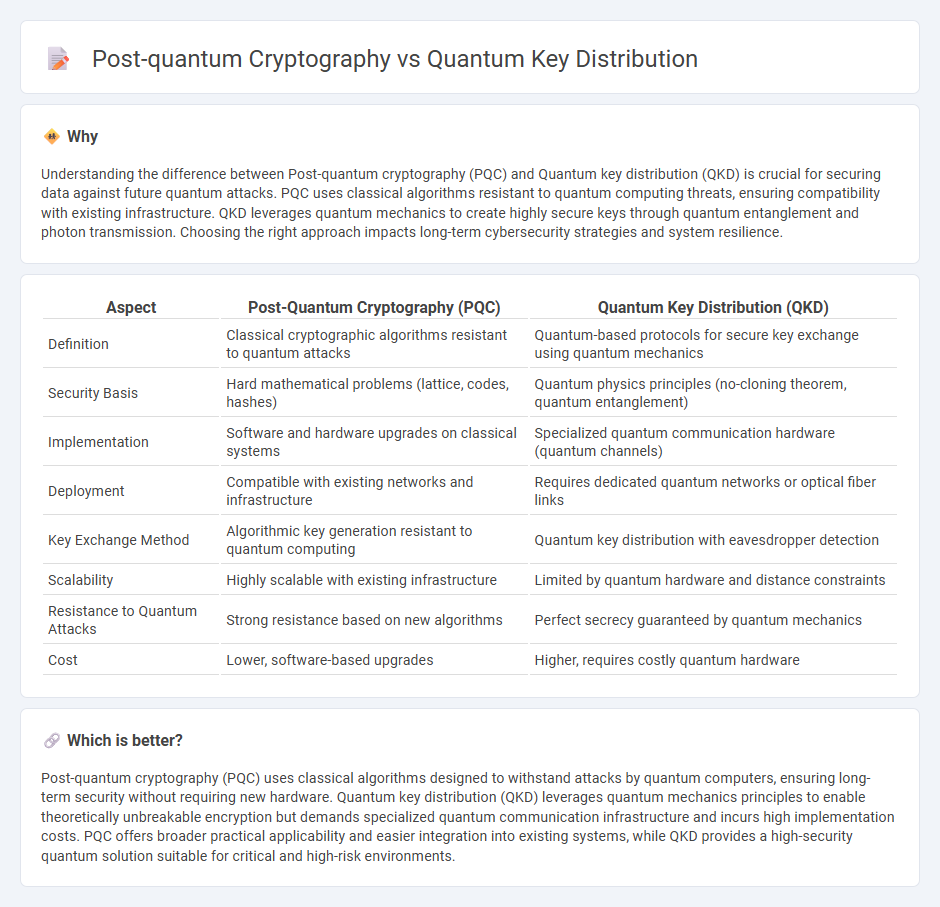
Understanding the difference between Post-quantum cryptography (PQC) and Quantum key distribution (QKD) is crucial for securing data against future quantum attacks. PQC uses classical algorithms resistant to quantum computing threats, ensuring compatibility with existing infrastructure. QKD leverages quantum mechanics to create highly secure keys through quantum entanglement and photon transmission. Choosing the right approach impacts long-term cybersecurity strategies and system resilience.
Comparison Table
| Aspect | Post-Quantum Cryptography (PQC) | Quantum Key Distribution (QKD) |
|---|---|---|
| Definition | Classical cryptographic algorithms resistant to quantum attacks | Quantum-based protocols for secure key exchange using quantum mechanics |
| Security Basis | Hard mathematical problems (lattice, codes, hashes) | Quantum physics principles (no-cloning theorem, quantum entanglement) |
| Implementation | Software and hardware upgrades on classical systems | Specialized quantum communication hardware (quantum channels) |
| Deployment | Compatible with existing networks and infrastructure | Requires dedicated quantum networks or optical fiber links |
| Key Exchange Method | Algorithmic key generation resistant to quantum computing | Quantum key distribution with eavesdropper detection |
| Scalability | Highly scalable with existing infrastructure | Limited by quantum hardware and distance constraints |
| Resistance to Quantum Attacks | Strong resistance based on new algorithms | Perfect secrecy guaranteed by quantum mechanics |
| Cost | Lower, software-based upgrades | Higher, requires costly quantum hardware |
Which is better?
Post-quantum cryptography (PQC) uses classical algorithms designed to withstand attacks by quantum computers, ensuring long-term security without requiring new hardware. Quantum key distribution (QKD) leverages quantum mechanics principles to enable theoretically unbreakable encryption but demands specialized quantum communication infrastructure and incurs high implementation costs. PQC offers broader practical applicability and easier integration into existing systems, while QKD provides a high-security quantum solution suitable for critical and high-risk environments.
Connection
Post-quantum cryptography develops algorithms resistant to quantum computer attacks, ensuring data security in a post-quantum era. Quantum key distribution (QKD) leverages quantum mechanics to enable secure communication by generating cryptographic keys immune to interception. Both technologies address the vulnerability of classical cryptographic systems against quantum threats by providing complementary solutions for future-proof secure communications.
Key Terms
Quantum Entanglement
Quantum entanglement plays a pivotal role in quantum key distribution (QKD), enabling secure communication by generating cryptographic keys through the intrinsic correlations of entangled particles that cannot be intercepted without detection. Post-quantum cryptography (PQC), in contrast, relies on classical algorithms designed to withstand attacks from quantum computers but does not involve quantum entanglement in its processes. Explore the differences and applications of quantum entanglement in QKD and PQC to deepen your understanding of future-proof cryptographic security.
Lattice-based Cryptography
Quantum key distribution (QKD) provides information-theoretic security by leveraging quantum mechanics principles to enable secure key exchange, while post-quantum cryptography (PQC) offers classical algorithms resistant to quantum attacks, with lattice-based cryptography being a leading candidate due to its strong security proofs and efficiency. Lattice-based schemes, such as Learning With Errors (LWE) and Ring-LWE, enable scalable encryption, digital signatures, and key encapsulation suitable for securing future communication networks against quantum adversaries. Explore the advancements and practical implementations of lattice-based cryptography to understand its role in the evolving landscape of quantum-safe security solutions.
No-cloning Theorem
Quantum key distribution (QKD) leverages the No-cloning Theorem to ensure that quantum states representing encryption keys cannot be copied without detection, enabling provably secure communication channels. Post-quantum cryptography (PQC) relies on mathematical hardness assumptions rather than quantum principles, making it resistant to quantum attacks but not inherently protected by the no-cloning property. Explore further how the No-cloning Theorem fundamentally differentiates quantum cryptographic methods from classical approaches enhanced for quantum security.
Source and External Links
What is Quantum Key Distribution? QKD Explained - TechTarget - Quantum key distribution (QKD) is a secure communication method for exchanging encryption keys using quantum physics principles, ensuring that any interception attempt changes the system, thus revealing eavesdropping and providing security beyond classical computing capabilities.
Quantum key distribution - Wikipedia - QKD is a cryptographic protocol based on quantum mechanics that allows two parties to share a secret key with provable security by detecting eavesdropping through unavoidable disturbances caused by quantum measurements.
True single-photon source boosts secure key rates in quantum key distribution - Phys.org - Advances in QKD include using true single-photon sources to increase secure key generation rates and overcome previous limitations of laser pulse-based systems, significantly enhancing secure communication performance.
 dowidth.com
dowidth.com