Quantum-safe cryptography focuses on developing encryption methods resistant to quantum computer attacks, ensuring data security against future quantum threats. Quantum cryptography leverages quantum mechanics to create secure communication channels, primarily using quantum key distribution to detect eavesdropping. Explore the latest advancements and differences between quantum-safe and quantum cryptography to strengthen your cybersecurity knowledge.
Why it is important
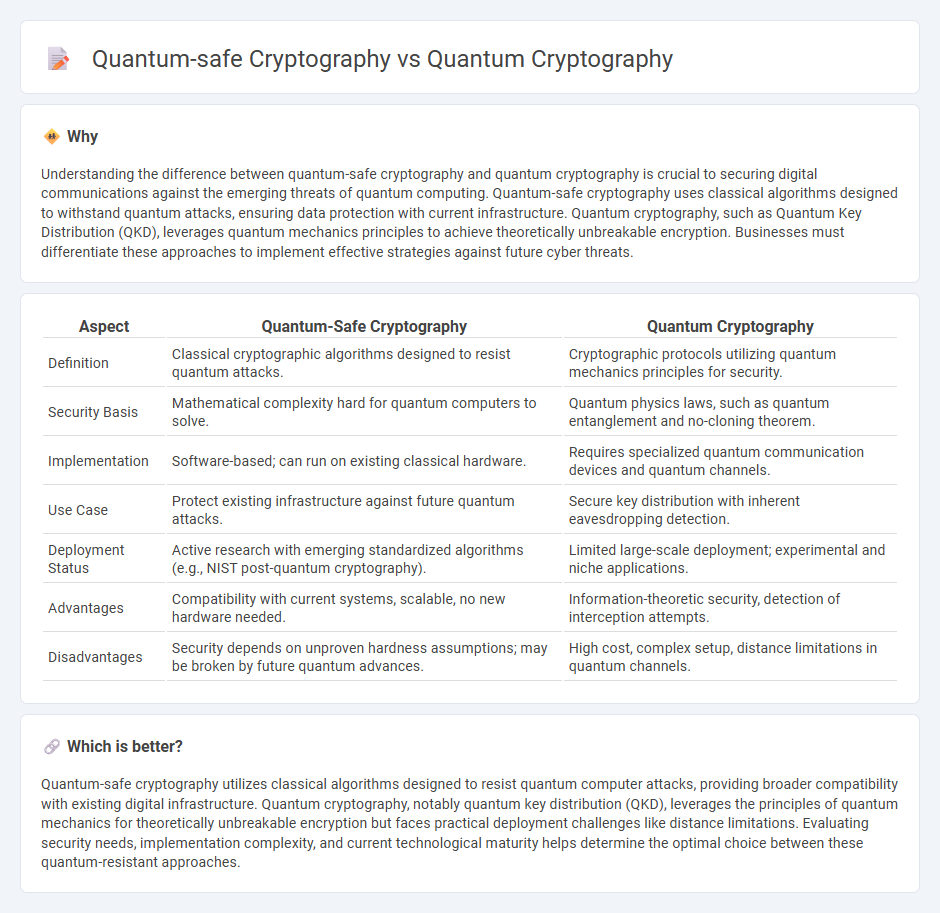
Understanding the difference between quantum-safe cryptography and quantum cryptography is crucial to securing digital communications against the emerging threats of quantum computing. Quantum-safe cryptography uses classical algorithms designed to withstand quantum attacks, ensuring data protection with current infrastructure. Quantum cryptography, such as Quantum Key Distribution (QKD), leverages quantum mechanics principles to achieve theoretically unbreakable encryption. Businesses must differentiate these approaches to implement effective strategies against future cyber threats.
Comparison Table
| Aspect | Quantum-Safe Cryptography | Quantum Cryptography |
|---|---|---|
| Definition | Classical cryptographic algorithms designed to resist quantum attacks. | Cryptographic protocols utilizing quantum mechanics principles for security. |
| Security Basis | Mathematical complexity hard for quantum computers to solve. | Quantum physics laws, such as quantum entanglement and no-cloning theorem. |
| Implementation | Software-based; can run on existing classical hardware. | Requires specialized quantum communication devices and quantum channels. |
| Use Case | Protect existing infrastructure against future quantum attacks. | Secure key distribution with inherent eavesdropping detection. |
| Deployment Status | Active research with emerging standardized algorithms (e.g., NIST post-quantum cryptography). | Limited large-scale deployment; experimental and niche applications. |
| Advantages | Compatibility with current systems, scalable, no new hardware needed. | Information-theoretic security, detection of interception attempts. |
| Disadvantages | Security depends on unproven hardness assumptions; may be broken by future quantum advances. | High cost, complex setup, distance limitations in quantum channels. |
Which is better?
Quantum-safe cryptography utilizes classical algorithms designed to resist quantum computer attacks, providing broader compatibility with existing digital infrastructure. Quantum cryptography, notably quantum key distribution (QKD), leverages the principles of quantum mechanics for theoretically unbreakable encryption but faces practical deployment challenges like distance limitations. Evaluating security needs, implementation complexity, and current technological maturity helps determine the optimal choice between these quantum-resistant approaches.
Connection
Quantum cryptography leverages principles of quantum mechanics to create secure communication channels resistant to eavesdropping, while quantum-safe cryptography focuses on developing classical cryptographic algorithms immune to attacks by quantum computers. Both fields aim to protect data confidentiality against emerging quantum threats, with quantum-safe cryptography preparing for future quantum attacks, and quantum cryptography providing immediate security using quantum key distribution (QKD). The connection lies in their shared goal of ensuring robust encryption in a world where quantum computing capabilities continue to advance rapidly.
Key Terms
Quantum key distribution (QKD)
Quantum cryptography primarily utilizes Quantum Key Distribution (QKD) to generate secure cryptographic keys by leveraging principles of quantum mechanics, such as quantum entanglement and superposition, ensuring eavesdropping attempts are detectable. Quantum-safe cryptography, also known as post-quantum cryptography, develops algorithms resistant to attacks from quantum computers but operates on classical systems without needing quantum hardware like QKD. Explore the distinctions and implementations of QKD and quantum-safe methods to understand their roles in future-proofing data security.
Post-quantum algorithms
Post-quantum algorithms in quantum-safe cryptography are designed to withstand attacks from quantum computers, unlike quantum cryptography which relies on quantum key distribution techniques for security. Lattice-based, hash-based, and code-based cryptographic algorithms are some leading candidates for post-quantum standards due to their resilience against Shor's and Grover's algorithms. Explore the advancements and implementation challenges of post-quantum cryptographic algorithms for securing future digital communications.
Shor's algorithm
Quantum cryptography uses quantum mechanics principles to secure communication, primarily through quantum key distribution (QKD), which is theoretically immune to interception. Quantum-safe cryptography, or post-quantum cryptography, develops algorithms resistant to quantum attacks like Shor's algorithm, which efficiently factors large integers and undermines classical RSA and ECC encryption. Explore the advancements in quantum-safe algorithms designed to counteract Shor's algorithm for a future-proof security framework.
Source and External Links
Classical vs. Quantum vs. Post-Quantum Cryptography - Quantum cryptography uses qubits and the unpredictable nature of quantum mechanics to enable secure key exchange and detect eavesdropping, providing security beyond traditional classical methods.
What Is Quantum Cryptography? - Quantum cryptography, exemplified by quantum key distribution (QKD), is a method that uses single photons to create and share secure cryptographic keys, detecting any interception attempt due to the impossibility of observing quantum states without altering them.
What Is Quantum Cryptography? - Quantum cryptography leverages quantum principles like superposition and entanglement to protect and authenticate data, and is being developed to safeguard information even in remote computing environments, such as blind quantum computing.
 dowidth.com
dowidth.com