Quantum-safe cryptography uses algorithms designed to resist attacks from quantum computers, unlike Elliptic Curve Cryptography (ECC), which relies on the difficulty of solving elliptic curve discrete logarithms vulnerable to quantum algorithms like Shor's algorithm. With the rise of quantum computing, quantum-safe cryptography, such as lattice-based or hash-based schemes, is critical for securing future communications and data integrity. Explore the evolving landscape of cryptographic technologies to understand how they safeguard digital security in a post-quantum world.
Why it is important
Understanding the difference between quantum-safe cryptography and elliptic curve cryptography is crucial because quantum-safe cryptography resists attacks from quantum computers that can break elliptic curve cryptography rapidly using Shor's algorithm. Elliptic curve cryptography currently secures most online transactions but will become vulnerable as quantum computing advances, risking data breaches and financial losses. Transitioning to quantum-safe algorithms like lattice-based cryptography ensures long-term security for sensitive information. This knowledge enables organizations to future-proof their encryption strategies against emerging quantum threats.
Comparison Table
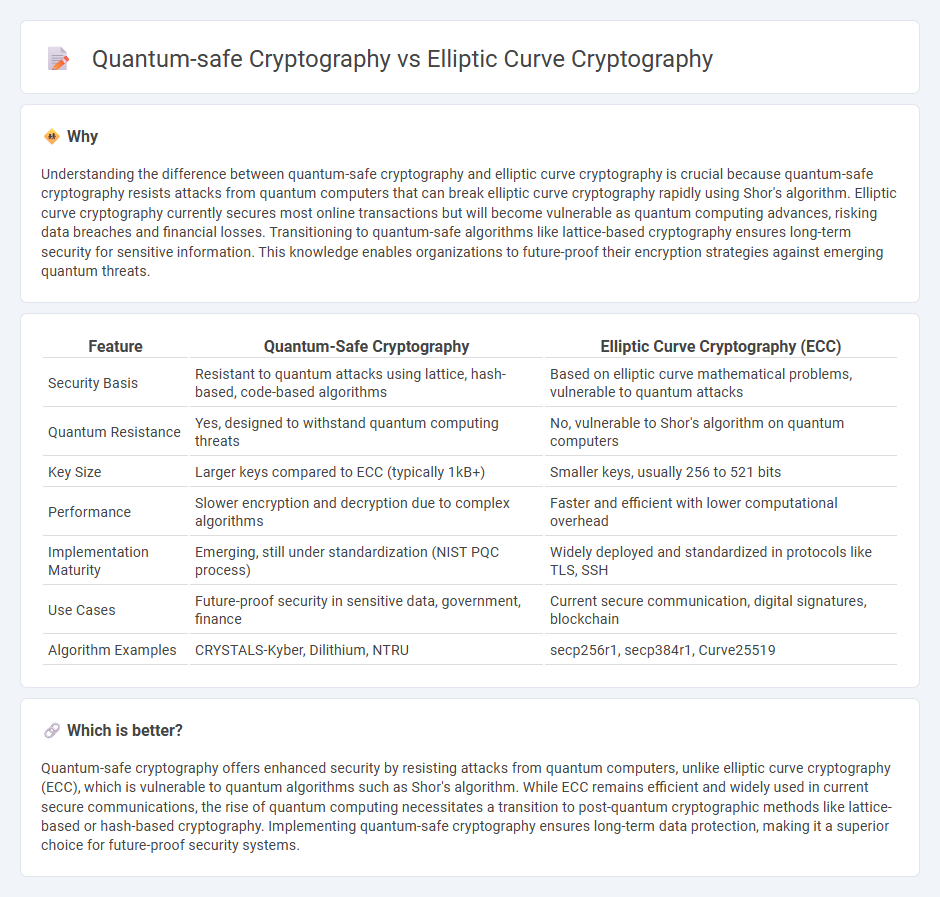
| Feature | Quantum-Safe Cryptography | Elliptic Curve Cryptography (ECC) |
|---|---|---|
| Security Basis | Resistant to quantum attacks using lattice, hash-based, code-based algorithms | Based on elliptic curve mathematical problems, vulnerable to quantum attacks |
| Quantum Resistance | Yes, designed to withstand quantum computing threats | No, vulnerable to Shor's algorithm on quantum computers |
| Key Size | Larger keys compared to ECC (typically 1kB+) | Smaller keys, usually 256 to 521 bits |
| Performance | Slower encryption and decryption due to complex algorithms | Faster and efficient with lower computational overhead |
| Implementation Maturity | Emerging, still under standardization (NIST PQC process) | Widely deployed and standardized in protocols like TLS, SSH |
| Use Cases | Future-proof security in sensitive data, government, finance | Current secure communication, digital signatures, blockchain |
| Algorithm Examples | CRYSTALS-Kyber, Dilithium, NTRU | secp256r1, secp384r1, Curve25519 |
Which is better?
Quantum-safe cryptography offers enhanced security by resisting attacks from quantum computers, unlike elliptic curve cryptography (ECC), which is vulnerable to quantum algorithms such as Shor's algorithm. While ECC remains efficient and widely used in current secure communications, the rise of quantum computing necessitates a transition to post-quantum cryptographic methods like lattice-based or hash-based cryptography. Implementing quantum-safe cryptography ensures long-term data protection, making it a superior choice for future-proof security systems.
Connection
Quantum-safe cryptography and Elliptic Curve Cryptography (ECC) both address data security but differ fundamentally in resistance to quantum attacks. ECC relies on the hardness of the Elliptic Curve Discrete Logarithm Problem, vulnerable to quantum algorithms like Shor's, while quantum-safe methods use post-quantum algorithms resistant to such threats. Integrating quantum-safe cryptography with ECC aims to future-proof encryption systems against emerging quantum computing capabilities.
Key Terms
Quantum Resistance
Elliptic curve cryptography (ECC) relies on the difficulty of the elliptic curve discrete logarithm problem, but its security faces challenges from emerging quantum algorithms like Shor's algorithm, which can efficiently solve these problems. Quantum-safe cryptography, also known as post-quantum cryptography, employs algorithms such as lattice-based, hash-based, and code-based cryptographic schemes designed to resist attacks from quantum computers. Explore the evolving landscape of quantum-resistant algorithms to understand how they safeguard data against future quantum threats.
Public Key Algorithms
Elliptic curve cryptography (ECC) offers efficient public key algorithms based on the algebraic structure of elliptic curves over finite fields, widely used for secure key exchange and digital signatures. Quantum-safe cryptography involves algorithms designed to resist attacks from quantum computers, such as lattice-based, hash-based, and multivariate polynomial public key systems, ensuring long-term data protection against quantum threats. Explore the evolving landscape of public key algorithms to understand the future of secure communication in the quantum era.
Shor's Algorithm
Elliptic curve cryptography (ECC) is vulnerable to Shor's Algorithm, a quantum algorithm capable of efficiently solving the discrete logarithm problem underlying ECC's security. Quantum-safe cryptography, including lattice-based and hash-based schemes, offers resistance against attacks from quantum computers exploiting Shor's Algorithm. Explore further to understand how these cryptographic approaches safeguard data in the quantum era.
Source and External Links
What is Elliptical Curve Cryptography (ECC)? - Elliptic curve cryptography (ECC) is a public key encryption technique based on elliptic curve theory that creates faster, smaller, and more efficient cryptographic keys compared to traditional methods like RSA.
Elliptic-curve cryptography - ECC is an approach to public-key cryptography that uses the algebraic structure of elliptic curves over finite fields, enabling smaller keys to provide security equivalent to larger RSA keys.
What is Elliptic Curve Cryptography (ECC)? - ECC leverages the mathematical properties of elliptic curves to generate key pairs, with security relying on the difficulty of solving the elliptic curve discrete logarithm problem.
 dowidth.com
dowidth.com