Quantum-safe cryptography ensures data security against quantum computing threats by using algorithms resistant to quantum attacks, while multivariate polynomial cryptography relies on the hardness of solving systems of multivariate equations to create secure keys. Both approaches aim to safeguard sensitive information in a future with powerful quantum computers capable of breaking traditional encryption methods. Explore the detailed comparisons and applications of these cryptographic techniques to understand their roles in advancing cybersecurity.
Why it is important
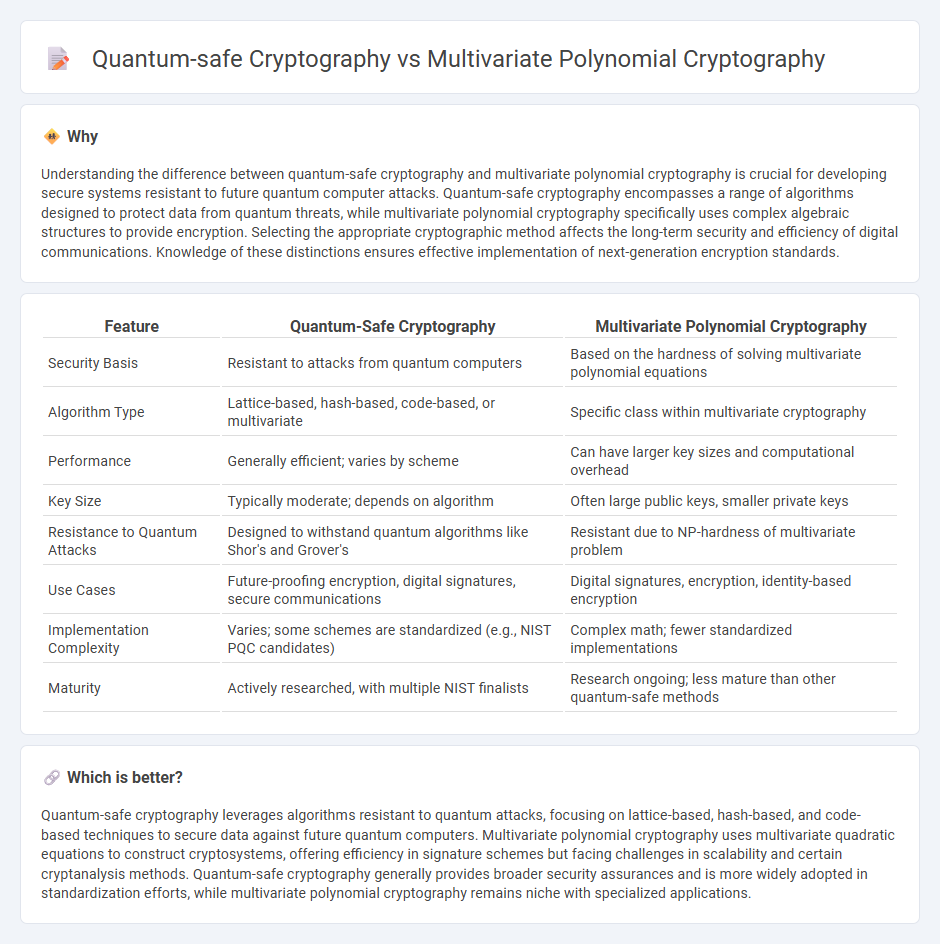
Understanding the difference between quantum-safe cryptography and multivariate polynomial cryptography is crucial for developing secure systems resistant to future quantum computer attacks. Quantum-safe cryptography encompasses a range of algorithms designed to protect data from quantum threats, while multivariate polynomial cryptography specifically uses complex algebraic structures to provide encryption. Selecting the appropriate cryptographic method affects the long-term security and efficiency of digital communications. Knowledge of these distinctions ensures effective implementation of next-generation encryption standards.
Comparison Table
| Feature | Quantum-Safe Cryptography | Multivariate Polynomial Cryptography |
|---|---|---|
| Security Basis | Resistant to attacks from quantum computers | Based on the hardness of solving multivariate polynomial equations |
| Algorithm Type | Lattice-based, hash-based, code-based, or multivariate | Specific class within multivariate cryptography |
| Performance | Generally efficient; varies by scheme | Can have larger key sizes and computational overhead |
| Key Size | Typically moderate; depends on algorithm | Often large public keys, smaller private keys |
| Resistance to Quantum Attacks | Designed to withstand quantum algorithms like Shor's and Grover's | Resistant due to NP-hardness of multivariate problem |
| Use Cases | Future-proofing encryption, digital signatures, secure communications | Digital signatures, encryption, identity-based encryption |
| Implementation Complexity | Varies; some schemes are standardized (e.g., NIST PQC candidates) | Complex math; fewer standardized implementations |
| Maturity | Actively researched, with multiple NIST finalists | Research ongoing; less mature than other quantum-safe methods |
Which is better?
Quantum-safe cryptography leverages algorithms resistant to quantum attacks, focusing on lattice-based, hash-based, and code-based techniques to secure data against future quantum computers. Multivariate polynomial cryptography uses multivariate quadratic equations to construct cryptosystems, offering efficiency in signature schemes but facing challenges in scalability and certain cryptanalysis methods. Quantum-safe cryptography generally provides broader security assurances and is more widely adopted in standardization efforts, while multivariate polynomial cryptography remains niche with specialized applications.
Connection
Quantum-safe cryptography and Multivariate polynomial cryptography are connected through their role in securing data against quantum computing threats. Multivariate polynomial cryptography, based on the hardness of solving systems of nonlinear equations, is a promising candidate for quantum-safe cryptographic schemes resistant to quantum attacks. This approach ensures robust encryption methods that maintain confidentiality even as quantum computers evolve and threaten traditional cryptographic algorithms.
Key Terms
Public Key Algorithms
Multivariate polynomial cryptography relies on the hardness of solving systems of nonlinear equations over finite fields, making it a promising candidate for post-quantum public key algorithms resistant to quantum attacks. Quantum-safe cryptography encompasses a broader range of cryptographic methods, including lattice-based, hash-based, code-based, and multivariate polynomial schemes, all designed to withstand the capabilities of quantum computers. Explore the latest advancements and practical applications of these quantum-resistant public key algorithms to understand their potential in securing future communications.
NP-hard Problems
Multivariate polynomial cryptography relies on solving systems of nonlinear polynomial equations, leveraging the NP-hardness of these problems for security in post-quantum scenarios. Quantum-safe cryptography encompasses a broader set of algorithms, including lattice-based, hash-based, and code-based schemes, all designed to withstand attacks from quantum computers by exploiting different NP-hard or NP-complete problems. Explore the latest advancements in both fields to understand how they secure information against future quantum threats.
Quantum Resistance
Multivariate polynomial cryptography employs complex systems of polynomial equations over finite fields, offering fast encryption and digital signatures resistant to classical attacks. Quantum-safe cryptography encompasses a broader range of algorithms, including lattice-based, code-based, and hash-based methods, designed specifically to withstand quantum computing threats. Explore the comparative quantum resistance and practical applications of these cutting-edge cryptographic approaches to ensure future-proof data security.
Source and External Links
MQ Challenge: Hardness Evaluation of Solving MQ problems - Multivariate polynomial (MP) cryptosystems, such as MPKC and the QUAD stream cipher, derive security from the difficulty of solving systems of multivariate polynomial equations, particularly when restricted to quadratics (MQ problem).
Exploring Multivariate Cryptography - Blue Goat Cyber - Multivariate cryptography relies on systems of polynomial equations with many variables, offering an alternative to number-theoretic schemes by using algebraic structures and high non-linearity to resist attacks.
Multivariate cryptography - Wikipedia - These asymmetric primitives use multivariate polynomials over finite fields, featuring public and private keys based on the composition of invertible transformations and quadratic maps, with trapdoors for efficient signing and verification.
 dowidth.com
dowidth.com