Passkey authentication offers enhanced security by utilizing cryptographic keys instead of traditional pattern locks, which can be vulnerable to smudge traces and shoulder surfing. Pattern locks rely on user-generated sequences that are often predictable, whereas passkeys enable seamless, phishing-resistant access across multiple devices. Explore the advantages of passkeys versus pattern locks to secure your digital life more effectively.
Why it is important
Understanding the difference between passkeys and pattern locks is crucial for enhancing smartphone security and preventing unauthorized access. Passkeys use encryption-based authentication, offering stronger protection against phishing compared to pattern locks that rely on simple gestures. This knowledge helps users choose more secure methods tailored to their privacy needs and device capabilities. Effective use of passkeys reduces cybersecurity risks and safeguards sensitive personal information.
Comparison Table
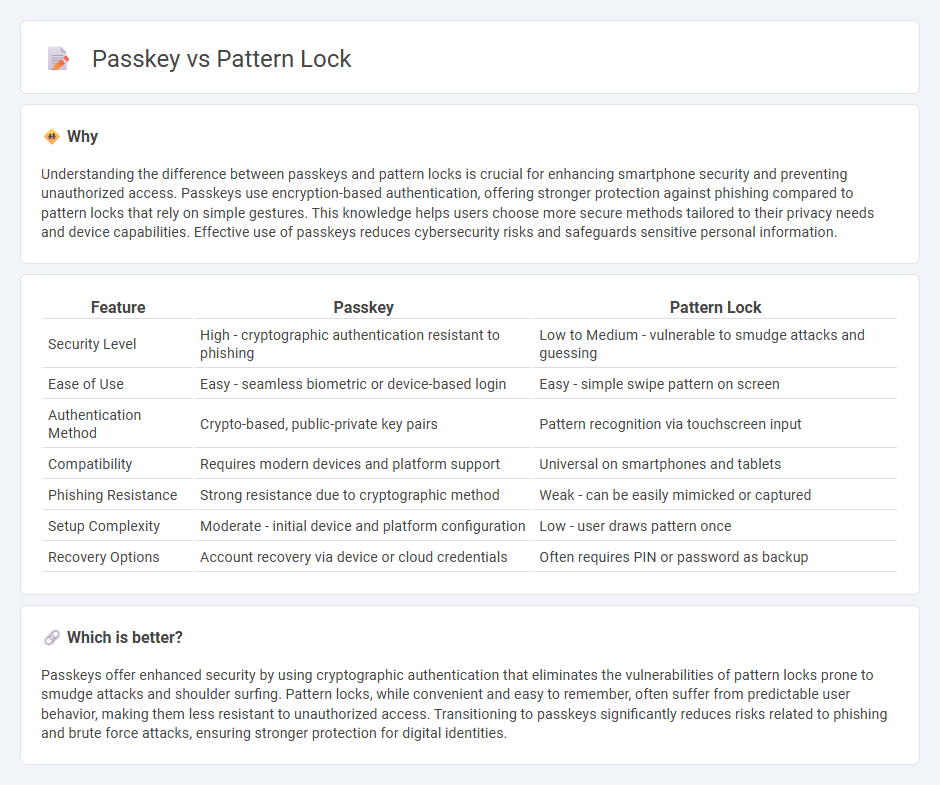
| Feature | Passkey | Pattern Lock |
|---|---|---|
| Security Level | High - cryptographic authentication resistant to phishing | Low to Medium - vulnerable to smudge attacks and guessing |
| Ease of Use | Easy - seamless biometric or device-based login | Easy - simple swipe pattern on screen |
| Authentication Method | Crypto-based, public-private key pairs | Pattern recognition via touchscreen input |
| Compatibility | Requires modern devices and platform support | Universal on smartphones and tablets |
| Phishing Resistance | Strong resistance due to cryptographic method | Weak - can be easily mimicked or captured |
| Setup Complexity | Moderate - initial device and platform configuration | Low - user draws pattern once |
| Recovery Options | Account recovery via device or cloud credentials | Often requires PIN or password as backup |
Which is better?
Passkeys offer enhanced security by using cryptographic authentication that eliminates the vulnerabilities of pattern locks prone to smudge attacks and shoulder surfing. Pattern locks, while convenient and easy to remember, often suffer from predictable user behavior, making them less resistant to unauthorized access. Transitioning to passkeys significantly reduces risks related to phishing and brute force attacks, ensuring stronger protection for digital identities.
Connection
Passkeys and pattern locks both enhance device security by providing user-friendly authentication methods that replace or complement traditional passwords. Passkeys leverage cryptographic protocols for seamless, phishing-resistant access, while pattern locks rely on visual patterns drawn on touchscreens, offering quick biometric alternatives. Integrating passkeys with pattern locks strengthens multi-factor authentication, combining cryptographic security with intuitive user verification.
Key Terms
Authentication
Pattern lock relies on a user-drawn sequence on a grid to authenticate access, offering convenience but lower security due to susceptibility to smudge attacks and shoulder surfing. Passkeys use cryptographic key pairs stored securely on devices, providing stronger, phishing-resistant authentication across platforms without requiring memorization. Explore the advancements in authentication methods to enhance your digital security.
Usability
Pattern lock offers fast, intuitive access using simple swipe gestures, ideal for users seeking convenience and memorability. Passkeys enhance security by replacing traditional passwords with cryptographic keys, reducing the risk of phishing and credential theft while requiring minimal user effort for authentication. Explore deeper insights into how usability and security balance in choosing between pattern locks and passkeys.
Security
Pattern lock security relies on graphical gestures, which can be vulnerable to smudge attacks and shoulder surfing, making it less secure than alphanumeric passkeys. Passkeys offer enhanced protection by utilizing complex, randomized character combinations that are more resistant to brute force and phishing attempts. Explore the differences in depth to choose the best security method for your device.
Source and External Links
pattern-lock-js Demo - A JavaScript library for implementing customizable pattern locks on web pages, complete with interactive demos and GitHub source code.
Set screen lock on an Android device - Google Help - Official Google instructions for setting, changing, or removing pattern locks (and other screen locks) on Android devices.
What Is The Most Complicated Lock Pattern? - YouTube - A video exploring the rules, mathematics, and complexity of Android lock patterns, including explanations of how many unique and maximum-complexity patterns exist under Android's constraints.
 dowidth.com
dowidth.com