Post-quantum cryptography focuses on developing encryption algorithms resistant to attacks from quantum computers, ensuring long-term data security in a quantum-enabled future. Homomorphic encryption allows computations to be performed directly on encrypted data without decryption, preserving privacy while enabling secure data processing. Explore the latest advancements in these groundbreaking technologies to understand their impact on cybersecurity and data privacy.
Why it is important
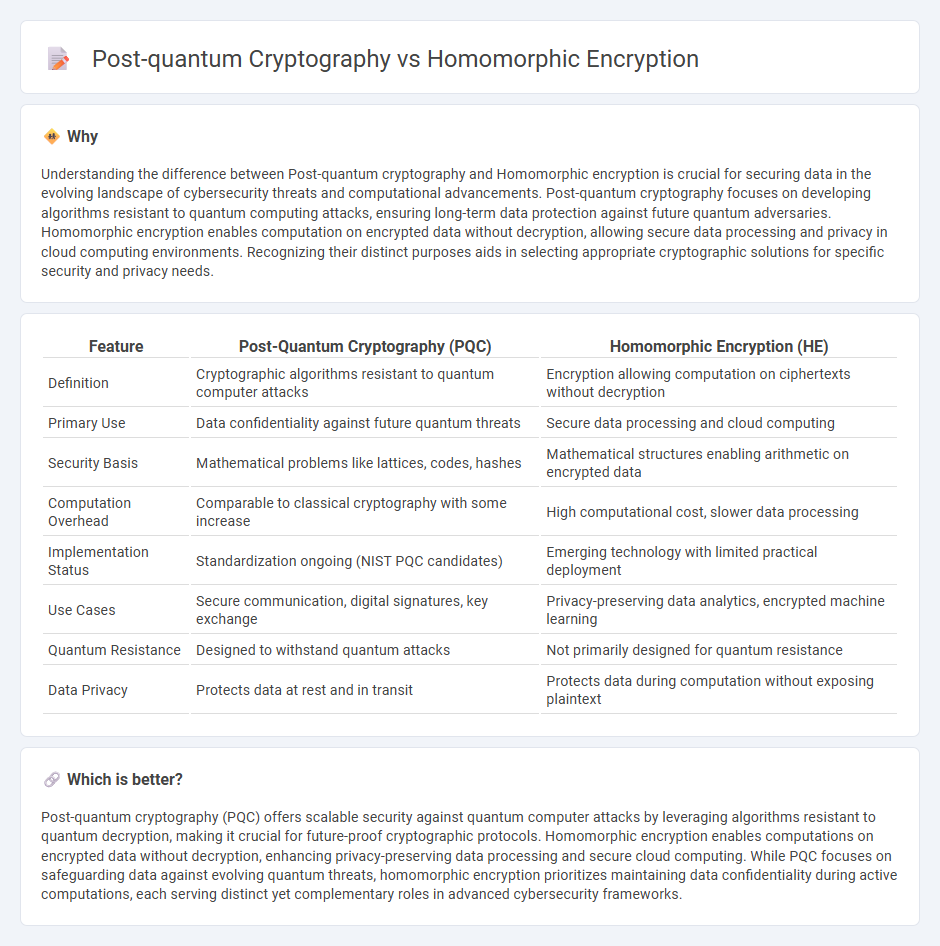
Understanding the difference between Post-quantum cryptography and Homomorphic encryption is crucial for securing data in the evolving landscape of cybersecurity threats and computational advancements. Post-quantum cryptography focuses on developing algorithms resistant to quantum computing attacks, ensuring long-term data protection against future quantum adversaries. Homomorphic encryption enables computation on encrypted data without decryption, allowing secure data processing and privacy in cloud computing environments. Recognizing their distinct purposes aids in selecting appropriate cryptographic solutions for specific security and privacy needs.
Comparison Table
| Feature | Post-Quantum Cryptography (PQC) | Homomorphic Encryption (HE) |
|---|---|---|
| Definition | Cryptographic algorithms resistant to quantum computer attacks | Encryption allowing computation on ciphertexts without decryption |
| Primary Use | Data confidentiality against future quantum threats | Secure data processing and cloud computing |
| Security Basis | Mathematical problems like lattices, codes, hashes | Mathematical structures enabling arithmetic on encrypted data |
| Computation Overhead | Comparable to classical cryptography with some increase | High computational cost, slower data processing |
| Implementation Status | Standardization ongoing (NIST PQC candidates) | Emerging technology with limited practical deployment |
| Use Cases | Secure communication, digital signatures, key exchange | Privacy-preserving data analytics, encrypted machine learning |
| Quantum Resistance | Designed to withstand quantum attacks | Not primarily designed for quantum resistance |
| Data Privacy | Protects data at rest and in transit | Protects data during computation without exposing plaintext |
Which is better?
Post-quantum cryptography (PQC) offers scalable security against quantum computer attacks by leveraging algorithms resistant to quantum decryption, making it crucial for future-proof cryptographic protocols. Homomorphic encryption enables computations on encrypted data without decryption, enhancing privacy-preserving data processing and secure cloud computing. While PQC focuses on safeguarding data against evolving quantum threats, homomorphic encryption prioritizes maintaining data confidentiality during active computations, each serving distinct yet complementary roles in advanced cybersecurity frameworks.
Connection
Post-quantum cryptography and homomorphic encryption both address the need for secure data protection in emerging technological landscapes, with post-quantum cryptography focusing on safeguarding information against quantum computing attacks. Homomorphic encryption enables computations on encrypted data without decryption, maintaining privacy during data processing, a feature vital in quantum-resistant protocols. The integration of these techniques advances secure communication frameworks capable of resisting quantum threats while preserving encrypted data utility.
Key Terms
Computation on Encrypted Data
Homomorphic encryption enables direct computation on encrypted data without decryption, preserving data privacy during processing and supporting secure outsourced computations in cloud environments. Post-quantum cryptography focuses on developing algorithms resistant to quantum attacks, ensuring long-term data security but typically does not inherently support computation on encrypted data. Explore further to understand how these technologies complement each other in safeguarding sensitive information while enabling secure data processing.
Quantum Resistance
Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy but often facing efficiency challenges in quantum resistance. Post-quantum cryptography specifically targets algorithms resistant to quantum attacks, ensuring secure communication against future quantum computers through lattice-based, hash-based, and code-based methods. Explore our comprehensive analysis to understand the quantum-proof strengths and applications of these cryptographic approaches.
Lattice-based Cryptography
Lattice-based cryptography serves as a foundational technique in both homomorphic encryption and post-quantum cryptography, leveraging complex mathematical structures to ensure security against quantum attacks. Homomorphic encryption enables secure computation on encrypted data, preserving privacy during processing, while lattice-based post-quantum cryptographic schemes focus on developing algorithms resistant to quantum computers. Discover more about how lattice-based methods are revolutionizing cryptographic security in the quantum era.
Source and External Links
Homomorphic encryption (Wikipedia) - Homomorphic encryption is a form of cryptography that allows computations to be performed on encrypted data without needing to decrypt it first.
What is homomorphic encryption, and why isn't it (Keyfactor) - Homomorphic encryption algorithms let you perform mathematical operations on encrypted data, preserving privacy even during computation.
What Is Homomorphic Encryption? (Chainlink) - Homomorphic encryption comes in several types--from schemes that only support addition or multiplication (partially homomorphic) to those that can perform any computation on encrypted data (fully homomorphic, though less practical due to computational cost).
 dowidth.com
dowidth.com