Federated learning enables decentralized model training by allowing devices to collaboratively learn from data without sharing raw information, enhancing privacy and reducing communication costs. Homomorphic encryption secures computations by performing operations on encrypted data, maintaining confidentiality even during processing in untrusted environments. Explore the detailed comparison to understand how these technologies revolutionize secure data handling in modern AI applications.
Why it is important
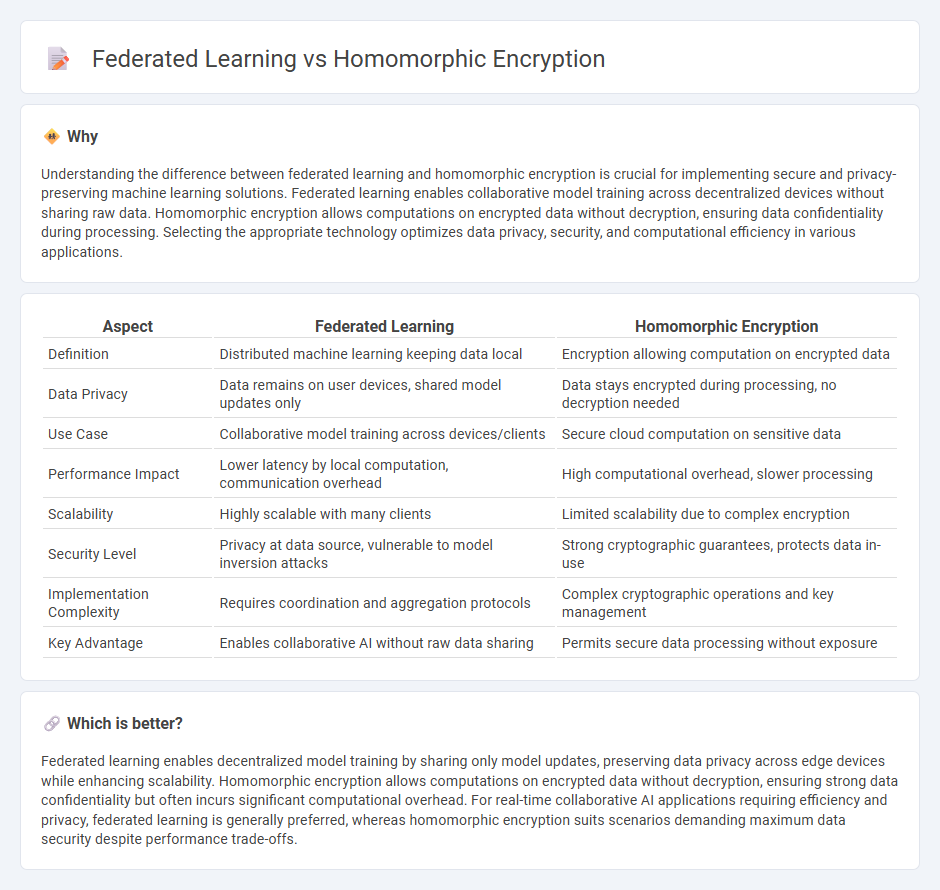
Understanding the difference between federated learning and homomorphic encryption is crucial for implementing secure and privacy-preserving machine learning solutions. Federated learning enables collaborative model training across decentralized devices without sharing raw data. Homomorphic encryption allows computations on encrypted data without decryption, ensuring data confidentiality during processing. Selecting the appropriate technology optimizes data privacy, security, and computational efficiency in various applications.
Comparison Table
| Aspect | Federated Learning | Homomorphic Encryption |
|---|---|---|
| Definition | Distributed machine learning keeping data local | Encryption allowing computation on encrypted data |
| Data Privacy | Data remains on user devices, shared model updates only | Data stays encrypted during processing, no decryption needed |
| Use Case | Collaborative model training across devices/clients | Secure cloud computation on sensitive data |
| Performance Impact | Lower latency by local computation, communication overhead | High computational overhead, slower processing |
| Scalability | Highly scalable with many clients | Limited scalability due to complex encryption |
| Security Level | Privacy at data source, vulnerable to model inversion attacks | Strong cryptographic guarantees, protects data in-use |
| Implementation Complexity | Requires coordination and aggregation protocols | Complex cryptographic operations and key management |
| Key Advantage | Enables collaborative AI without raw data sharing | Permits secure data processing without exposure |
Which is better?
Federated learning enables decentralized model training by sharing only model updates, preserving data privacy across edge devices while enhancing scalability. Homomorphic encryption allows computations on encrypted data without decryption, ensuring strong data confidentiality but often incurs significant computational overhead. For real-time collaborative AI applications requiring efficiency and privacy, federated learning is generally preferred, whereas homomorphic encryption suits scenarios demanding maximum data security despite performance trade-offs.
Connection
Federated learning enables collaborative model training across decentralized devices while keeping data localized, enhancing privacy. Homomorphic encryption complements this by allowing computations on encrypted data without decryption, ensuring sensitive information remains secure during the learning process. The integration of these technologies facilitates privacy-preserving machine learning in distributed environments, optimizing data security and analytical capabilities.
Key Terms
Data Privacy
Homomorphic encryption enables secure computations on encrypted data without revealing the raw information, ensuring privacy by allowing data processing in ciphertext form. Federated learning trains machine learning models locally on decentralized devices, sharing only model updates rather than raw data, thus minimizing exposure of sensitive information. Explore the latest advancements to understand which privacy-preserving technique best suits your data security needs.
Decentralized Computation
Homomorphic encryption enables secure decentralized computation by allowing data to be processed in its encrypted form, preserving privacy without decryption. Federated learning distributes model training across multiple devices, keeping data localized while aggregating learning updates to improve a global model. Explore these cutting-edge technologies to understand how they revolutionize decentralized computation and privacy-preserving machine learning.
Secure Computation
Homomorphic encryption enables secure computation by allowing data to be processed in its encrypted form, preserving privacy throughout the computation process. Federated learning distributes model training across decentralized devices, ensuring raw data remains local while only encrypted model updates are shared, reducing exposure to centralized data breaches. Explore the nuances of secure computation methods and their impact on privacy-preserving AI by learning more about homomorphic encryption and federated learning.
Source and External Links
Homomorphic encryption - Homomorphic encryption is a cryptographic method that enables computations on encrypted data without decrypting it, with types including partially, somewhat, leveled fully, and fully homomorphic encryption allowing increasing levels of computation complexity and circuit depth over encrypted data.
What is homomorphic encryption, and why isn't it ... - Homomorphic encryption algorithms allow mathematical operations such as addition or multiplication to be performed on encrypted data, with partially homomorphic encryption supporting only one type of operation indefinitely, like RSA's multiplicative homomorphism.
What Is Homomorphic Encryption? - Homomorphic encryption includes various schemes like partially homomorphic (supports either addition or multiplication), somewhat homomorphic (both but limited), leveled fully homomorphic (bounded depth arbitrary computations), and fully homomorphic encryption enabling unrestricted computations on encrypted data, though with current computational cost challenges.
 dowidth.com
dowidth.com