Post-quantum cryptography focuses on developing encryption algorithms resistant to attacks by quantum computers, whereas symmetric cryptography relies on shared secret keys for secure communication. Quantum-resistant algorithms like lattice-based and hash-based cryptography ensure data protection in a future with quantum advancements. Explore how these cryptographic methods shape the security landscape in the era of quantum computing.
Why it is important
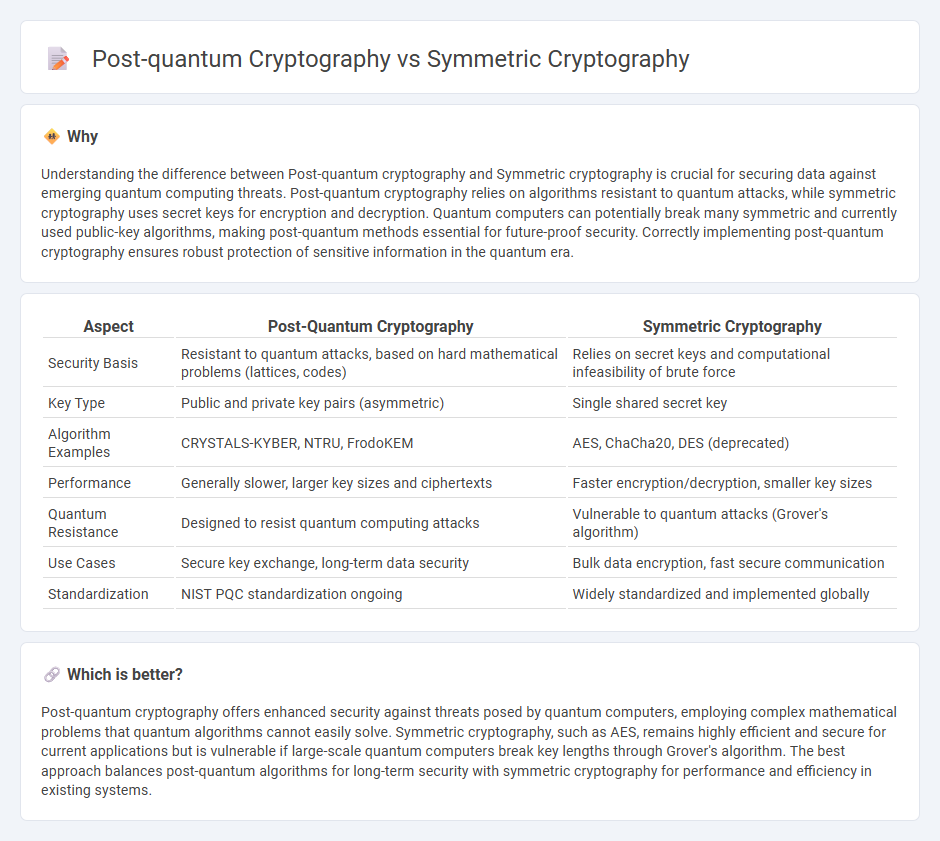
Understanding the difference between Post-quantum cryptography and Symmetric cryptography is crucial for securing data against emerging quantum computing threats. Post-quantum cryptography relies on algorithms resistant to quantum attacks, while symmetric cryptography uses secret keys for encryption and decryption. Quantum computers can potentially break many symmetric and currently used public-key algorithms, making post-quantum methods essential for future-proof security. Correctly implementing post-quantum cryptography ensures robust protection of sensitive information in the quantum era.
Comparison Table
| Aspect | Post-Quantum Cryptography | Symmetric Cryptography |
|---|---|---|
| Security Basis | Resistant to quantum attacks, based on hard mathematical problems (lattices, codes) | Relies on secret keys and computational infeasibility of brute force |
| Key Type | Public and private key pairs (asymmetric) | Single shared secret key |
| Algorithm Examples | CRYSTALS-KYBER, NTRU, FrodoKEM | AES, ChaCha20, DES (deprecated) |
| Performance | Generally slower, larger key sizes and ciphertexts | Faster encryption/decryption, smaller key sizes |
| Quantum Resistance | Designed to resist quantum computing attacks | Vulnerable to quantum attacks (Grover's algorithm) |
| Use Cases | Secure key exchange, long-term data security | Bulk data encryption, fast secure communication |
| Standardization | NIST PQC standardization ongoing | Widely standardized and implemented globally |
Which is better?
Post-quantum cryptography offers enhanced security against threats posed by quantum computers, employing complex mathematical problems that quantum algorithms cannot easily solve. Symmetric cryptography, such as AES, remains highly efficient and secure for current applications but is vulnerable if large-scale quantum computers break key lengths through Grover's algorithm. The best approach balances post-quantum algorithms for long-term security with symmetric cryptography for performance and efficiency in existing systems.
Connection
Post-quantum cryptography safeguards data against threats posed by quantum computing, which can break many traditional asymmetric cryptographic schemes. Symmetric cryptography remains largely secure against quantum attacks by relying on shorter key lengths and robust algorithms such as AES and SHA-3. The integration of post-quantum algorithms with symmetric cryptography enhances overall encryption strength, ensuring data confidentiality and integrity in a quantum-resistant security framework.
Key Terms
Shared Secret Key
Symmetric cryptography relies on a shared secret key for both encryption and decryption, offering speed and efficiency but facing vulnerabilities against quantum algorithms like Grover's, which can halve its security strength. Post-quantum cryptography aims to develop new algorithms resistant to quantum attacks, often using different key exchange methods that don't depend solely on shared secret keys, thereby enhancing long-term security. Explore the latest advances in secure key exchange protocols to better understand the evolution from symmetric to post-quantum cryptographic systems.
Quantum Resistance
Symmetric cryptography relies on shared secret keys and remains relatively secure against quantum attacks when key sizes are sufficiently large, but its efficiency declines as key length increases. Post-quantum cryptography encompasses algorithms specifically designed to withstand quantum computing threats, utilizing lattice-based, code-based, and multivariate polynomial techniques to ensure quantum resistance. Explore the latest advancements and practical implementations of quantum-resistant cryptographic methods to enhance cybersecurity.
Lattice-Based Algorithms
Symmetric cryptography relies on shared secret keys for encryption and decryption, offering efficiency but facing challenges against future quantum attacks. Post-quantum cryptography, particularly lattice-based algorithms, provides quantum-resistant security by leveraging the hardness of lattice problems such as Learning With Errors (LWE) and Shortest Vector Problem (SVP). Explore how lattice-based methods are shaping the next generation of secure encryption to prepare for the quantum era.
Source and External Links
Symmetric-key algorithm - Wikipedia - Symmetric-key algorithms use the same cryptographic keys for both encrypting plaintext and decrypting ciphertext, making them efficient for bulk encryption but requiring secure key exchange between parties.
What is Symmetric Encryption? - Entrust - Symmetric encryption, also called secret-key encryption, uses a single shared key for both encrypting and decrypting data, relying on algorithms that transform plaintext into unreadable ciphertext for secure transmission or storage.
What Is Symmetric Encryption? - IBM - Symmetric encryption is faster and simpler than asymmetric encryption, using one key for both encryption and decryption, though secure key management is crucial to prevent unauthorized access to encrypted data.
 dowidth.com
dowidth.com