Post-quantum cryptography employs innovative algorithms designed to withstand attacks from quantum computers, unlike classical cryptography which relies on mathematical problems vulnerable to quantum decryption methods. Quantum-resistant algorithms, such as lattice-based and hash-based cryptography, offer enhanced security for future digital communications. Explore the advancements in cryptographic technology securing tomorrow's data.
Why it is important
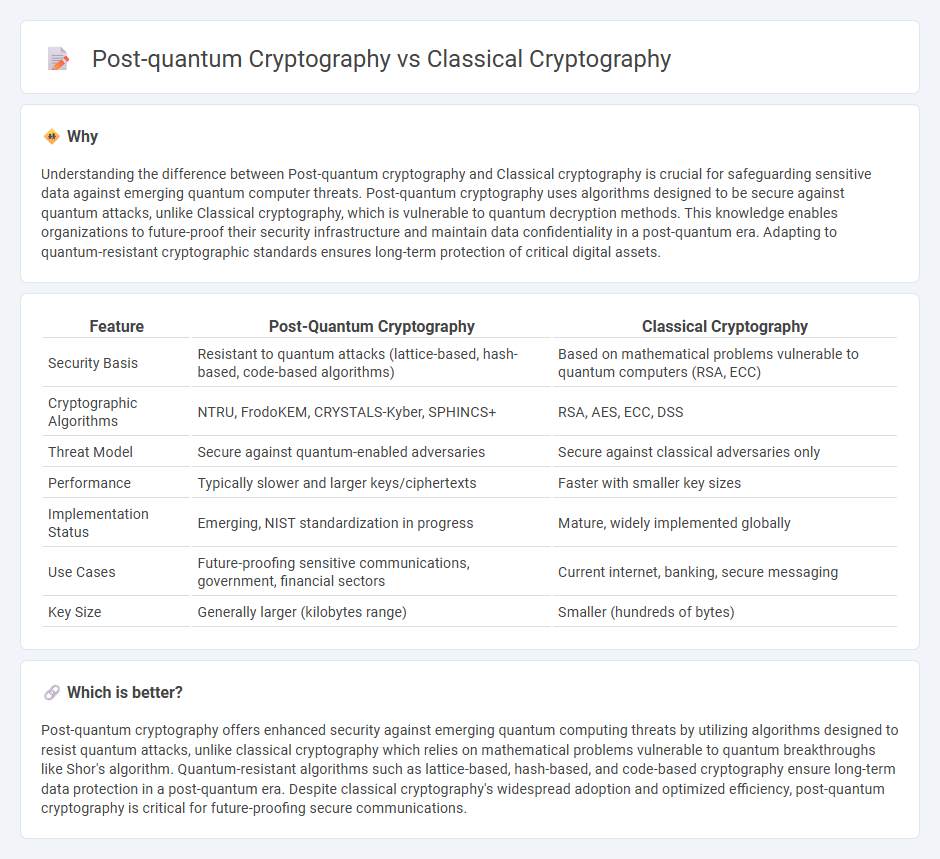
Understanding the difference between Post-quantum cryptography and Classical cryptography is crucial for safeguarding sensitive data against emerging quantum computer threats. Post-quantum cryptography uses algorithms designed to be secure against quantum attacks, unlike Classical cryptography, which is vulnerable to quantum decryption methods. This knowledge enables organizations to future-proof their security infrastructure and maintain data confidentiality in a post-quantum era. Adapting to quantum-resistant cryptographic standards ensures long-term protection of critical digital assets.
Comparison Table
| Feature | Post-Quantum Cryptography | Classical Cryptography |
|---|---|---|
| Security Basis | Resistant to quantum attacks (lattice-based, hash-based, code-based algorithms) | Based on mathematical problems vulnerable to quantum computers (RSA, ECC) |
| Cryptographic Algorithms | NTRU, FrodoKEM, CRYSTALS-Kyber, SPHINCS+ | RSA, AES, ECC, DSS |
| Threat Model | Secure against quantum-enabled adversaries | Secure against classical adversaries only |
| Performance | Typically slower and larger keys/ciphertexts | Faster with smaller key sizes |
| Implementation Status | Emerging, NIST standardization in progress | Mature, widely implemented globally |
| Use Cases | Future-proofing sensitive communications, government, financial sectors | Current internet, banking, secure messaging |
| Key Size | Generally larger (kilobytes range) | Smaller (hundreds of bytes) |
Which is better?
Post-quantum cryptography offers enhanced security against emerging quantum computing threats by utilizing algorithms designed to resist quantum attacks, unlike classical cryptography which relies on mathematical problems vulnerable to quantum breakthroughs like Shor's algorithm. Quantum-resistant algorithms such as lattice-based, hash-based, and code-based cryptography ensure long-term data protection in a post-quantum era. Despite classical cryptography's widespread adoption and optimized efficiency, post-quantum cryptography is critical for future-proofing secure communications.
Connection
Post-quantum cryptography builds upon classical cryptography by enhancing security protocols to resist quantum computer attacks, ensuring data confidentiality and integrity in the quantum era. It adapts traditional cryptographic algorithms, such as RSA and ECC, by introducing quantum-resistant algorithms like lattice-based, hash-based, and code-based cryptography. This connection preserves the foundational principles of classical cryptography while future-proofing encryption against the computational power of quantum machines.
Key Terms
Symmetric-key algorithms
Symmetric-key algorithms in classical cryptography, such as AES and DES, rely on computational hardness assumptions vulnerable to quantum attacks, especially Grover's algorithm, which effectively halves their key strength. Post-quantum cryptography focuses on designing symmetric-key schemes with longer keys and quantum-resistant constructions to ensure data confidentiality against quantum adversaries. Explore more about advancements in symmetric-key post-quantum cryptography and their practical implications for securing information.
Public-key quantum resistance
Classical cryptography, such as RSA and ECC, relies on mathematical problems like integer factorization and discrete logarithms that can be efficiently solved by quantum algorithms like Shor's algorithm, rendering them vulnerable to quantum attacks. Post-quantum cryptography (PQC) focuses on developing public-key algorithms based on hard problems like lattice-based, code-based, and multivariate polynomial equations, which remain secure against quantum adversaries. Explore more about how post-quantum cryptography ensures future-proof security in a quantum computing era.
Lattice-based cryptography
Lattice-based cryptography offers robust security against quantum attacks, leveraging the hardness of lattice problems like Learning With Errors (LWE) and Shortest Vector Problem (SVP), unlike classical cryptography that relies on factoring or discrete logarithm assumptions vulnerable to quantum algorithms. This makes lattice-based schemes promising candidates for post-quantum cryptographic standards, enabling secure encryption, digital signatures, and key exchange protocols resistant to quantum computing threats. Explore detailed comparisons and implementation challenges in lattice-based cryptography to strengthen future-proof cybersecurity.
Source and External Links
How Do Classical Cryptography and Modern Cryptography Differ? - This article discusses how classical cryptography, reliant on manual methods like substitution ciphers, differs from modern cryptography in terms of scalability and security.
History of cryptography - This page provides a comprehensive history of cryptography, including the development of classical cryptographic methods and their significance in medieval times.
Classical Cryptography and Quantum Cryptography - This article describes classical cryptography, focusing on its mathematical basis and use of keys for encryption, as well as its limitations and differences from quantum cryptography.
 dowidth.com
dowidth.com