Zero Trust Architecture eliminates implicit trust by continuously verifying every user and device, contrasting sharply with the Castle-and-Moat model that relies on perimeter defenses to protect internal resources. This modern security approach minimizes insider threats and lateral movement by enforcing strict access controls and real-time monitoring across networks. Explore how adopting Zero Trust can revolutionize your organization's cybersecurity strategy.
Why it is important
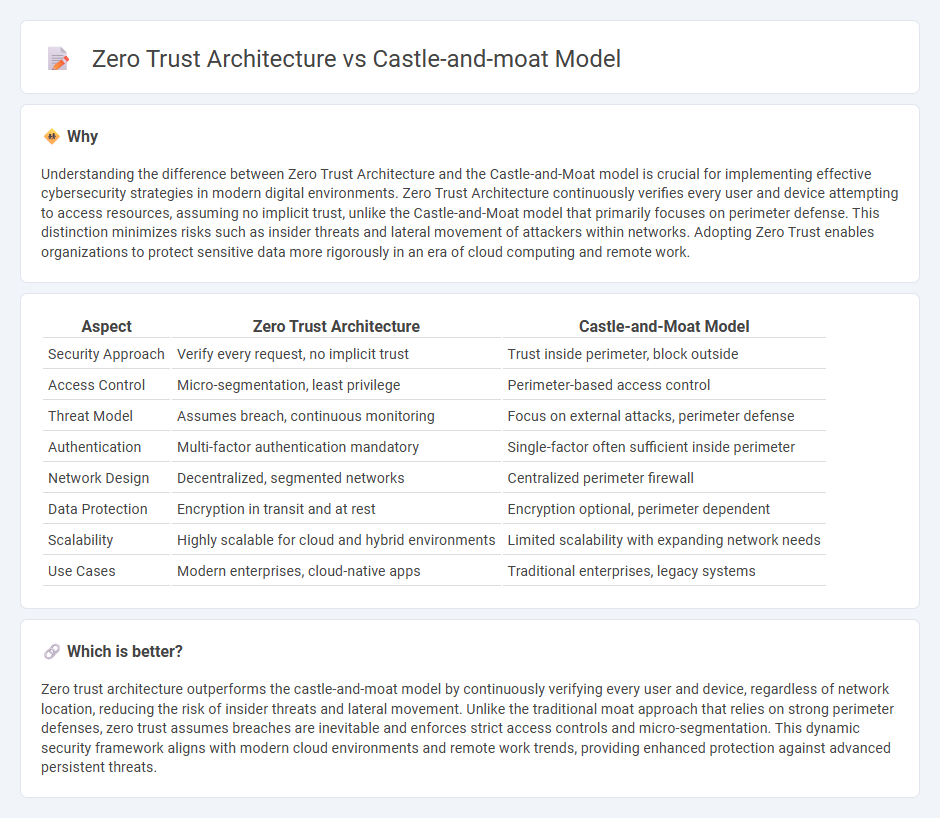
Understanding the difference between Zero Trust Architecture and the Castle-and-Moat model is crucial for implementing effective cybersecurity strategies in modern digital environments. Zero Trust Architecture continuously verifies every user and device attempting to access resources, assuming no implicit trust, unlike the Castle-and-Moat model that primarily focuses on perimeter defense. This distinction minimizes risks such as insider threats and lateral movement of attackers within networks. Adopting Zero Trust enables organizations to protect sensitive data more rigorously in an era of cloud computing and remote work.
Comparison Table
| Aspect | Zero Trust Architecture | Castle-and-Moat Model |
|---|---|---|
| Security Approach | Verify every request, no implicit trust | Trust inside perimeter, block outside |
| Access Control | Micro-segmentation, least privilege | Perimeter-based access control |
| Threat Model | Assumes breach, continuous monitoring | Focus on external attacks, perimeter defense |
| Authentication | Multi-factor authentication mandatory | Single-factor often sufficient inside perimeter |
| Network Design | Decentralized, segmented networks | Centralized perimeter firewall |
| Data Protection | Encryption in transit and at rest | Encryption optional, perimeter dependent |
| Scalability | Highly scalable for cloud and hybrid environments | Limited scalability with expanding network needs |
| Use Cases | Modern enterprises, cloud-native apps | Traditional enterprises, legacy systems |
Which is better?
Zero trust architecture outperforms the castle-and-moat model by continuously verifying every user and device, regardless of network location, reducing the risk of insider threats and lateral movement. Unlike the traditional moat approach that relies on strong perimeter defenses, zero trust assumes breaches are inevitable and enforces strict access controls and micro-segmentation. This dynamic security framework aligns with modern cloud environments and remote work trends, providing enhanced protection against advanced persistent threats.
Connection
Zero trust architecture and the castle-and-moat model both focus on securing network perimeters, but zero trust eliminates implicit trust by continuously verifying every user and device regardless of location. While the castle-and-moat model relies heavily on a strong boundary defense and internal trust, zero trust enforces strict access controls and micro-segmentation to reduce lateral movement within the network. Combining these approaches enhances cybersecurity by addressing evolving threats beyond traditional perimeter defenses.
Key Terms
Perimeter Security (Castle-and-Moat)
The Castle-and-Moat model emphasizes perimeter security by establishing a strong boundary around an organization's network to prevent unauthorized access, similar to a fortress protecting its inner assets. This approach relies heavily on firewalls, intrusion detection systems, and VPNs to secure the network perimeter but assumes that threats within the boundary are trusted. Explore comprehensive comparisons and advantages of Zero Trust Architecture to understand why modern cybersecurity shifts towards continuous verification and minimal trust.
Least Privilege (Zero Trust)
The castle-and-moat model relies heavily on perimeter defense, assuming entities inside the network are trusted, while Zero Trust architecture enforces Least Privilege by continuously verifying and limiting access based on user roles and context. Least Privilege in Zero Trust minimizes risk by granting users and applications only the permissions necessary to perform their tasks, reducing the attack surface. Explore how adopting Least Privilege within Zero Trust can strengthen your security posture and prevent insider threats.
Continuous Verification (Zero Trust)
The castle-and-moat model relies on strong perimeter defenses to keep threats out, but once inside, network elements often have broad access, posing significant risks. Zero Trust Architecture (ZTA) enforces continuous verification of every user and device, regardless of location, minimizing the attack surface and preventing lateral movement within networks. Explore how continuous verification transforms security frameworks by ensuring persistent authentication and dynamic access control.
Source and External Links
Castle-And-Moat Network Security Model - CyberHoot - The castle-and-moat model is a traditional network security approach where external access to internal data is blocked, but once inside, users can freely access all resources, focusing perimeter defenses like medieval castles and moats.
The Crumbling Castle - Cyber Defense Magazine - This model relies on building a strong perimeter (the "moat") around corporate networks, assuming threats come only from outside, but struggles with insider threats, remote work, and cloud services, making it obsolete in modern IT environments.
The So-Called Castle and Moat Security Model is Dead - The castle-and-moat model is now considered ineffective because organizations' digital infrastructures are too large and dispersed, and the traditional perimeter can no longer be meaningfully defended against today's threats.
 dowidth.com
dowidth.com