Zero Trust Architecture enforces strict identity verification for every user and device attempting to access resources, minimizing risks of unauthorized access in dynamic IT environments. Privileged Access Management focuses on controlling and monitoring elevated account activities to prevent misuse of high-level credentials. Explore how integrating both models enhances enterprise cybersecurity strategies.
Why it is important
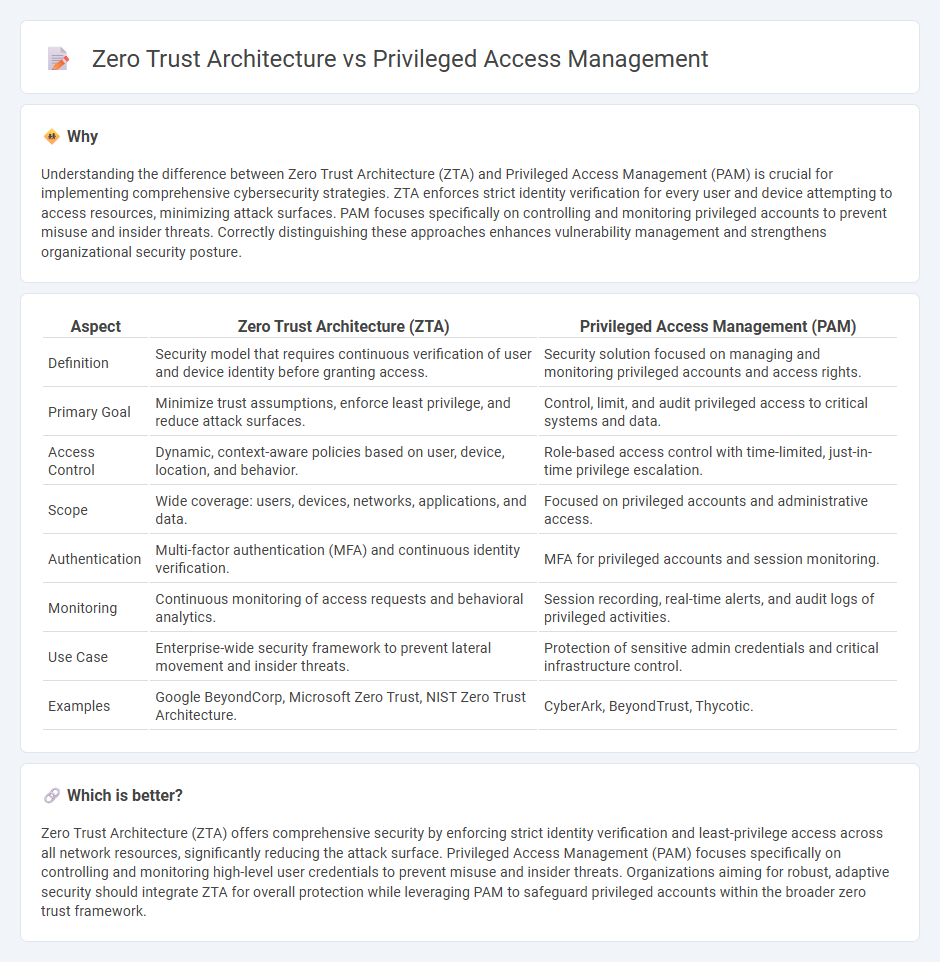
Understanding the difference between Zero Trust Architecture (ZTA) and Privileged Access Management (PAM) is crucial for implementing comprehensive cybersecurity strategies. ZTA enforces strict identity verification for every user and device attempting to access resources, minimizing attack surfaces. PAM focuses specifically on controlling and monitoring privileged accounts to prevent misuse and insider threats. Correctly distinguishing these approaches enhances vulnerability management and strengthens organizational security posture.
Comparison Table
| Aspect | Zero Trust Architecture (ZTA) | Privileged Access Management (PAM) |
|---|---|---|
| Definition | Security model that requires continuous verification of user and device identity before granting access. | Security solution focused on managing and monitoring privileged accounts and access rights. |
| Primary Goal | Minimize trust assumptions, enforce least privilege, and reduce attack surfaces. | Control, limit, and audit privileged access to critical systems and data. |
| Access Control | Dynamic, context-aware policies based on user, device, location, and behavior. | Role-based access control with time-limited, just-in-time privilege escalation. |
| Scope | Wide coverage: users, devices, networks, applications, and data. | Focused on privileged accounts and administrative access. |
| Authentication | Multi-factor authentication (MFA) and continuous identity verification. | MFA for privileged accounts and session monitoring. |
| Monitoring | Continuous monitoring of access requests and behavioral analytics. | Session recording, real-time alerts, and audit logs of privileged activities. |
| Use Case | Enterprise-wide security framework to prevent lateral movement and insider threats. | Protection of sensitive admin credentials and critical infrastructure control. |
| Examples | Google BeyondCorp, Microsoft Zero Trust, NIST Zero Trust Architecture. | CyberArk, BeyondTrust, Thycotic. |
Which is better?
Zero Trust Architecture (ZTA) offers comprehensive security by enforcing strict identity verification and least-privilege access across all network resources, significantly reducing the attack surface. Privileged Access Management (PAM) focuses specifically on controlling and monitoring high-level user credentials to prevent misuse and insider threats. Organizations aiming for robust, adaptive security should integrate ZTA for overall protection while leveraging PAM to safeguard privileged accounts within the broader zero trust framework.
Connection
Zero Trust Architecture minimizes security risks by strictly verifying every user and device before granting access, while Privileged Access Management controls and monitors elevated permissions to critical systems. Both frameworks complement each other by enforcing stringent access controls and continuous authentication, reducing the attack surface from insider threats and credential compromises. Integrating these strategies strengthens organizational cybersecurity posture through granular access enforcement and real-time privilege oversight.
Key Terms
Least Privilege
Privileged Access Management (PAM) enforces least privilege by restricting administrative access to only the necessary accounts and tasks, minimizing risk from insider threats and compromised credentials. Zero Trust Architecture (ZTA) extends least privilege principles by continuously validating every access request, regardless of network location, ensuring that users and devices have minimal access needed for their roles. Explore the differences and integration strategies of PAM and ZTA to strengthen your cybersecurity framework.
Multi-Factor Authentication
Privileged Access Management (PAM) relies on Multi-Factor Authentication (MFA) to secure elevated user privileges by enforcing strict access controls and verifying identities through multiple authentication factors. Zero Trust Architecture (ZTA) adopts MFA as a core principle, continuously validating every access request regardless of user location, device, or network environment to minimize security risks. Explore in-depth comparisons of PAM and ZTA implementations to optimize your cybersecurity strategy with effective MFA integration.
Continuous Verification
Privileged Access Management (PAM) focuses on controlling and monitoring access to critical systems by verifying and limiting privileged accounts, while Zero Trust Architecture (ZTA) enforces continuous verification of all users and devices regardless of location or network status. Continuous verification in ZTA relies on dynamic risk assessment and multifactor authentication to ensure persistent trustworthiness, minimizing insider threats and unauthorized access. Explore deeper insights into how Continuous Verification integrates PAM within a Zero Trust framework for enhanced cybersecurity resilience.
Source and External Links
Best Privileged Access Management Reviews 2025 - Privileged access management (PAM) tools centralize and enforce the control of elevated technical access by managing and protecting privileged accounts, credentials, and commands, with features like credential vaulting, session monitoring, just-in-time access, and privileged account discovery.
What is Privileged Access Management (PAM) - PAM is an identity security solution that safeguards organizations from cyberthreats by requiring multifactor authentication, automating security controls, removing unnecessary admin users, and granting only temporary, least-privilege access based on activity and need.
What is a Privileged Access Management Tool? - PAM tools are software solutions that discover, govern, and secure privileged accounts across systems and applications, offering credential vaulting, session management, privilege elevation controls, and secrets management to enforce least-privilege access and reduce credential exposure.
 dowidth.com
dowidth.com