Zero Trust Architecture enforces strict identity verification for every user and device attempting to access resources, eliminating implicit trust based on network location. Network segmentation divides a network into isolated segments to contain breaches and limit lateral movement of attackers. Explore the key differences and benefits of Zero Trust and network segmentation to enhance your cybersecurity strategy.
Why it is important
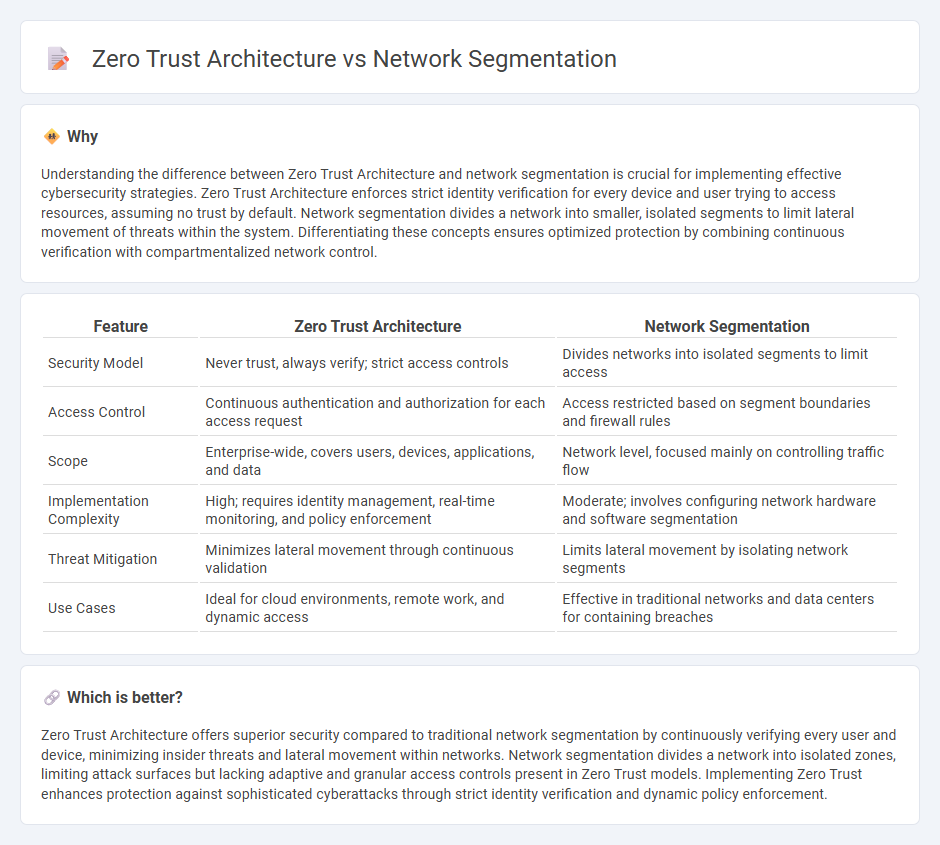
Understanding the difference between Zero Trust Architecture and network segmentation is crucial for implementing effective cybersecurity strategies. Zero Trust Architecture enforces strict identity verification for every device and user trying to access resources, assuming no trust by default. Network segmentation divides a network into smaller, isolated segments to limit lateral movement of threats within the system. Differentiating these concepts ensures optimized protection by combining continuous verification with compartmentalized network control.
Comparison Table
| Feature | Zero Trust Architecture | Network Segmentation |
|---|---|---|
| Security Model | Never trust, always verify; strict access controls | Divides networks into isolated segments to limit access |
| Access Control | Continuous authentication and authorization for each access request | Access restricted based on segment boundaries and firewall rules |
| Scope | Enterprise-wide, covers users, devices, applications, and data | Network level, focused mainly on controlling traffic flow |
| Implementation Complexity | High; requires identity management, real-time monitoring, and policy enforcement | Moderate; involves configuring network hardware and software segmentation |
| Threat Mitigation | Minimizes lateral movement through continuous validation | Limits lateral movement by isolating network segments |
| Use Cases | Ideal for cloud environments, remote work, and dynamic access | Effective in traditional networks and data centers for containing breaches |
Which is better?
Zero Trust Architecture offers superior security compared to traditional network segmentation by continuously verifying every user and device, minimizing insider threats and lateral movement within networks. Network segmentation divides a network into isolated zones, limiting attack surfaces but lacking adaptive and granular access controls present in Zero Trust models. Implementing Zero Trust enhances protection against sophisticated cyberattacks through strict identity verification and dynamic policy enforcement.
Connection
Zero trust architecture relies on network segmentation to enforce strict access controls by dividing the network into isolated segments, minimizing the attack surface. Network segmentation enables continuous verification of user identities and device health within each segment, aligning with the zero trust principle of "never trust, always verify." Together, they enhance cybersecurity by containing potential breaches and preventing lateral movement across network resources.
Key Terms
Trust Boundaries
Network segmentation divides a network into multiple zones to limit access and contain threats within defined trust boundaries, reducing the attack surface by isolating sensitive data and systems. Zero Trust Architecture eliminates implicit trust by continuously verifying user identity and device security posture, enforcing strict access controls regardless of network location. Explore how combining dynamic zero trust principles with strategic network segmentation fortifies trust boundaries to enhance cybersecurity resilience.
Microsegmentation
Network segmentation divides a network into isolated segments to limit the spread of threats, while zero trust architecture enforces strict identity verification across all users and devices, regardless of location. Microsegmentation, a key component of zero trust, creates secure zones within data centers and cloud environments to provide granular control over east-west traffic, minimizing lateral movement of attackers. Explore how microsegmentation enhances security in zero trust frameworks for advanced threat protection.
Least Privilege
Network segmentation divides a network into separate zones to limit access and reduce attack surfaces, aligning with the principle of Least Privilege by restricting user permissions to specific segments. Zero Trust Architecture enforces continuous verification of user identities and device health, ensuring access permissions are granted strictly on a need-to-know basis regardless of network location. Discover how integrating these strategies enhances cybersecurity frameworks by minimizing unauthorized access risks.
Source and External Links
Network Segmentation: What It Is & How It Works - Network segmentation divides a larger network into smaller subnetworks or segments, either physically using hardware like routers and switches or logically using VLANs and IP subnetting, to isolate and control traffic flows and users within distinct zones.
10 Network Segmentation Best Practices - Network segmentation improves security by isolating network parts based on criteria like user roles or data sensitivity, using techniques such as VLANs, firewalls, and SDN to control access and contain breaches within defined zones or segments.
What Is Network Segmentation? - Network segmentation is an architectural approach splitting a network into subnets using physical or logical methods to reduce attack surface, enhance security, improve performance by reducing congestion, and simplify compliance scope.
 dowidth.com
dowidth.com