Passkeys offer a passwordless authentication method that enhances security by using cryptographic keys stored on devices, reducing the risk of phishing and credential theft. Multi-factor authentication (MFA) combines two or more verification factors, such as passwords, biometrics, or one-time codes, to provide layered protection against unauthorized access. Explore the advantages and applications of passkeys and MFA to strengthen your cybersecurity posture.
Why it is important
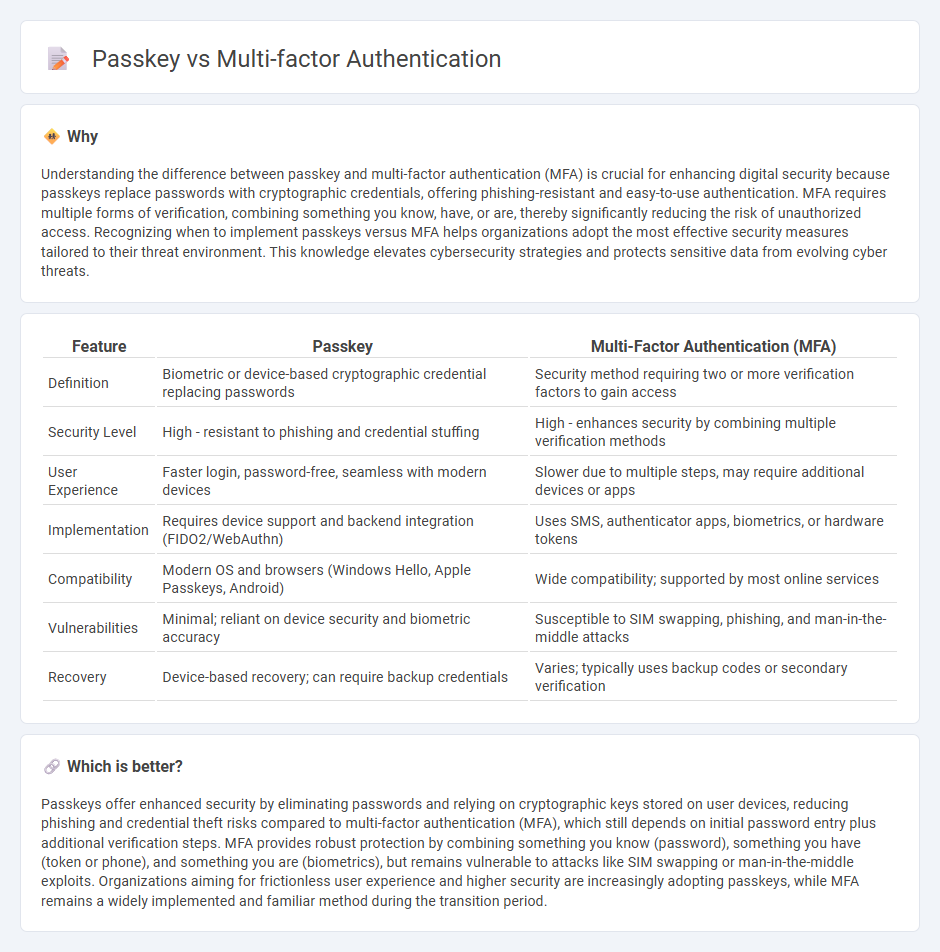
Understanding the difference between passkey and multi-factor authentication (MFA) is crucial for enhancing digital security because passkeys replace passwords with cryptographic credentials, offering phishing-resistant and easy-to-use authentication. MFA requires multiple forms of verification, combining something you know, have, or are, thereby significantly reducing the risk of unauthorized access. Recognizing when to implement passkeys versus MFA helps organizations adopt the most effective security measures tailored to their threat environment. This knowledge elevates cybersecurity strategies and protects sensitive data from evolving cyber threats.
Comparison Table
| Feature | Passkey | Multi-Factor Authentication (MFA) |
|---|---|---|
| Definition | Biometric or device-based cryptographic credential replacing passwords | Security method requiring two or more verification factors to gain access |
| Security Level | High - resistant to phishing and credential stuffing | High - enhances security by combining multiple verification methods |
| User Experience | Faster login, password-free, seamless with modern devices | Slower due to multiple steps, may require additional devices or apps |
| Implementation | Requires device support and backend integration (FIDO2/WebAuthn) | Uses SMS, authenticator apps, biometrics, or hardware tokens |
| Compatibility | Modern OS and browsers (Windows Hello, Apple Passkeys, Android) | Wide compatibility; supported by most online services |
| Vulnerabilities | Minimal; reliant on device security and biometric accuracy | Susceptible to SIM swapping, phishing, and man-in-the-middle attacks |
| Recovery | Device-based recovery; can require backup credentials | Varies; typically uses backup codes or secondary verification |
Which is better?
Passkeys offer enhanced security by eliminating passwords and relying on cryptographic keys stored on user devices, reducing phishing and credential theft risks compared to multi-factor authentication (MFA), which still depends on initial password entry plus additional verification steps. MFA provides robust protection by combining something you know (password), something you have (token or phone), and something you are (biometrics), but remains vulnerable to attacks like SIM swapping or man-in-the-middle exploits. Organizations aiming for frictionless user experience and higher security are increasingly adopting passkeys, while MFA remains a widely implemented and familiar method during the transition period.
Connection
Passkeys enhance multi-factor authentication (MFA) by providing a passwordless login method that relies on cryptographic keys stored on a device, increasing security against phishing and credential theft. MFA combines passkeys with other authentication factors, such as biometrics or one-time codes, to create multiple layers of verification. This integration reduces reliance on traditional passwords and strengthens overall access control in digital security systems.
Key Terms
Authentication factors
Multi-factor authentication (MFA) requires users to provide two or more verification factors, such as something they know (password), something they have (security token), or something they are (biometrics). Passkeys streamline authentication by replacing passwords with cryptographic key pairs stored securely on devices, combining something you have with biometric verification for enhanced security. Explore more about the differences and benefits of MFA and passkey authentication methods.
Biometric verification
Biometric verification in multi-factor authentication requires users to provide physical identifiers like fingerprints or facial recognition alongside passwords, increasing security by combining "something you know" with "something you are." Passkeys leverage biometric data directly to replace traditional passwords, offering a seamless, phishing-resistant authentication experience through private-public key cryptography integrated with the device's biometric sensors. Explore the evolving role of biometric verification in authentication to understand the future of secure access.
FIDO2
Multi-factor authentication (MFA) combines multiple verification methods such as passwords, biometrics, and hardware tokens to enhance security, while passkeys are FIDO2-compliant cryptographic credentials designed to replace passwords with seamless and phishing-resistant authentication. FIDO2 passkeys leverage public-key cryptography to enable passwordless login experiences, offering stronger protection against credential theft compared to traditional MFA methods. Explore the advantages and implementation details of FIDO2 passkeys to strengthen your security infrastructure.
Source and External Links
What is MFA (Multifactor Authentication)? - IBM - Multi-factor authentication (MFA) secures user identity by requiring at least two distinct proofs (e.g., password and fingerprint), adding extra layers of protection beyond passwords alone and preventing unauthorized access even if a password is compromised.
What is Multi-Factor Authentication (MFA)? - OneLogin - MFA requires two or more verification factors such as passwords plus OTPs or biometric data, enhancing security by reducing the likelihood of cyber attacks on accounts or applications.
What is Multi-Factor Authentication? - MFA Explained - AWS - MFA is a multi-step login process that improves digital security by requiring more than a password, helping prevent unauthorized account access and minimizing risks like lost passwords or stolen devices.
 dowidth.com
dowidth.com