Post-quantum cryptography focuses on creating encryption methods resilient against the computational power of quantum computers, ensuring data security in a future with advanced quantum technology. Lattice-based cryptography is a leading candidate within this field, leveraging the complexity of multidimensional lattice problems to provide robust, quantum-resistant encryption schemes. Explore the intricacies and applications of these groundbreaking cryptographic approaches to secure digital communication in the quantum era.
Why it is important
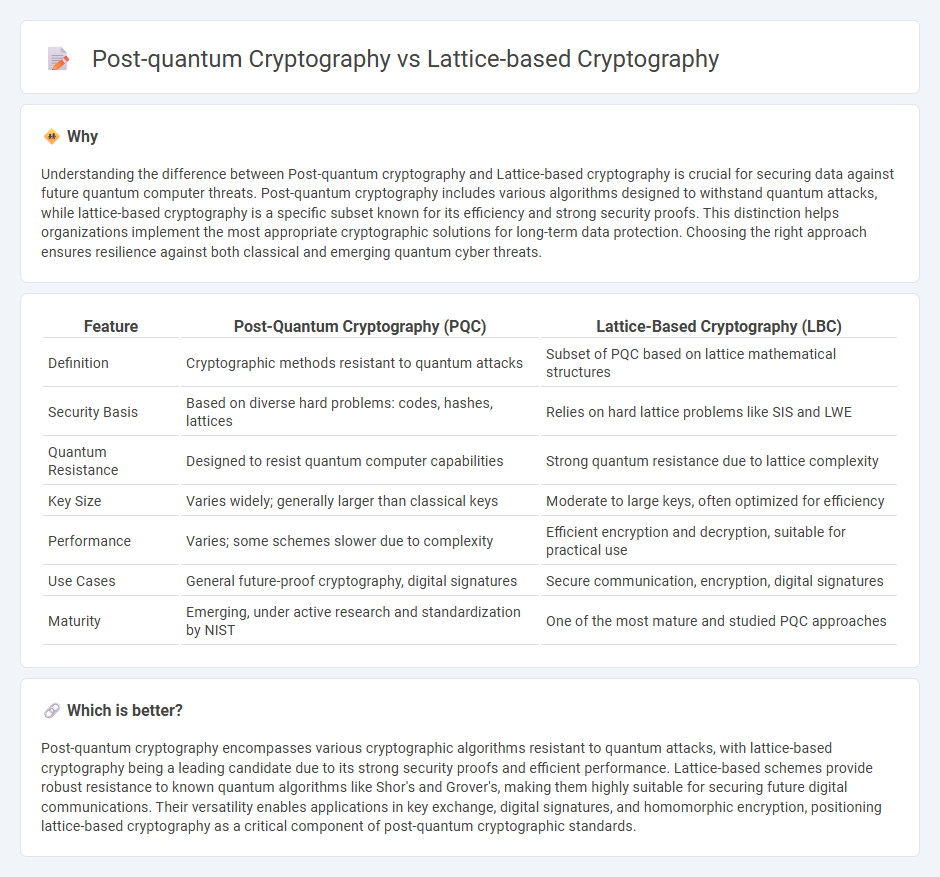
Understanding the difference between Post-quantum cryptography and Lattice-based cryptography is crucial for securing data against future quantum computer threats. Post-quantum cryptography includes various algorithms designed to withstand quantum attacks, while lattice-based cryptography is a specific subset known for its efficiency and strong security proofs. This distinction helps organizations implement the most appropriate cryptographic solutions for long-term data protection. Choosing the right approach ensures resilience against both classical and emerging quantum cyber threats.
Comparison Table
| Feature | Post-Quantum Cryptography (PQC) | Lattice-Based Cryptography (LBC) |
|---|---|---|
| Definition | Cryptographic methods resistant to quantum attacks | Subset of PQC based on lattice mathematical structures |
| Security Basis | Based on diverse hard problems: codes, hashes, lattices | Relies on hard lattice problems like SIS and LWE |
| Quantum Resistance | Designed to resist quantum computer capabilities | Strong quantum resistance due to lattice complexity |
| Key Size | Varies widely; generally larger than classical keys | Moderate to large keys, often optimized for efficiency |
| Performance | Varies; some schemes slower due to complexity | Efficient encryption and decryption, suitable for practical use |
| Use Cases | General future-proof cryptography, digital signatures | Secure communication, encryption, digital signatures |
| Maturity | Emerging, under active research and standardization by NIST | One of the most mature and studied PQC approaches |
Which is better?
Post-quantum cryptography encompasses various cryptographic algorithms resistant to quantum attacks, with lattice-based cryptography being a leading candidate due to its strong security proofs and efficient performance. Lattice-based schemes provide robust resistance to known quantum algorithms like Shor's and Grover's, making them highly suitable for securing future digital communications. Their versatility enables applications in key exchange, digital signatures, and homomorphic encryption, positioning lattice-based cryptography as a critical component of post-quantum cryptographic standards.
Connection
Post-quantum cryptography focuses on developing cryptographic algorithms resistant to the computational power of quantum computers, with lattice-based cryptography being a leading candidate due to its strong security foundations rooted in hard lattice problems. Lattice-based cryptography leverages mathematical structures such as the Shortest Vector Problem (SVP) and Learning With Errors (LWE) to provide encryption and digital signatures immune to quantum attacks. This connection positions lattice-based methods as a critical component in designing secure cryptographic systems for the post-quantum era.
Key Terms
Lattice Problems
Lattice-based cryptography relies on the hardness of lattice problems such as the Shortest Vector Problem (SVP) and Learning With Errors (LWE) to ensure security against quantum attacks. These problems remain intractable for both classical and quantum computers, making lattice-based schemes a leading candidate in post-quantum cryptography frameworks. Explore the complexities of lattice problems and their role in building quantum-resistant algorithms to enhance your understanding of future-proof cryptographic solutions.
Quantum Resistance
Lattice-based cryptography is a leading candidate within post-quantum cryptography due to its strong resistance against quantum computer attacks, leveraging complex mathematical problems like the Shortest Vector Problem (SVP) for security. Post-quantum cryptography encompasses various cryptographic systems designed to remain secure even as quantum computing capabilities advance, ensuring long-term protection of sensitive data. Explore more to understand how lattice-based methods outperform other quantum-resistant algorithms in both security and efficiency.
Hardness Assumptions
Lattice-based cryptography relies on the hardness of mathematical problems like the Shortest Vector Problem (SVP) and Learning With Errors (LWE), which remain difficult for both classical and quantum computers, making it a cornerstone of post-quantum cryptographic schemes. Post-quantum cryptography broadly encompasses various algorithms designed to resist attacks from quantum computers, including lattice-based, code-based, multivariate polynomial, and hash-based cryptographic methods. Explore the strengths and challenges of these hardness assumptions to understand the future of quantum-resistant security.
Source and External Links
Post-quantum cryptography: Lattice-based cryptography - Red Hat - Lattice-based cryptography is a class of cryptographic systems based on hard mathematical problems involving vectors that form lattices, which are used to build quantum-resistant encryption schemes.
Lattice-based cryptography - Wikipedia - This cryptographic approach includes schemes for encryption, key exchange, hashing, and homomorphic encryption, with notable examples like CRYSTALS-Kyber and NTRUEncrypt, many of which are candidates for or have been standardized for post-quantum security.
Lattice based cryptography - Lattice-based cryptography has a long history and forms the foundation for advanced constructs like fully homomorphic encryption and offers security assumptions resilient to quantum computing threats, attracting strong interest in both theoretical and applied cryptography.
 dowidth.com
dowidth.com