Zero trust security eliminates assumptions by verifying every access request regardless of location or network, strictly limiting permissions based on identity and context. Implicit trust, in contrast, grants access once initial credentials are verified, often leaving systems vulnerable to breaches if internal defenses are compromised. Discover how adopting a zero trust model can transform your organization's cybersecurity posture.
Why it is important
Understanding the difference between zero trust and implicit trust is crucial for strengthening cybersecurity frameworks. Zero trust assumes no user or device is trustworthy until verified, reducing risks of data breaches and insider threats. Implicit trust grants access based on network location or credentials, which can lead to vulnerabilities if compromised. Knowledge of these models helps organizations implement more effective access controls and protect sensitive information.
Comparison Table
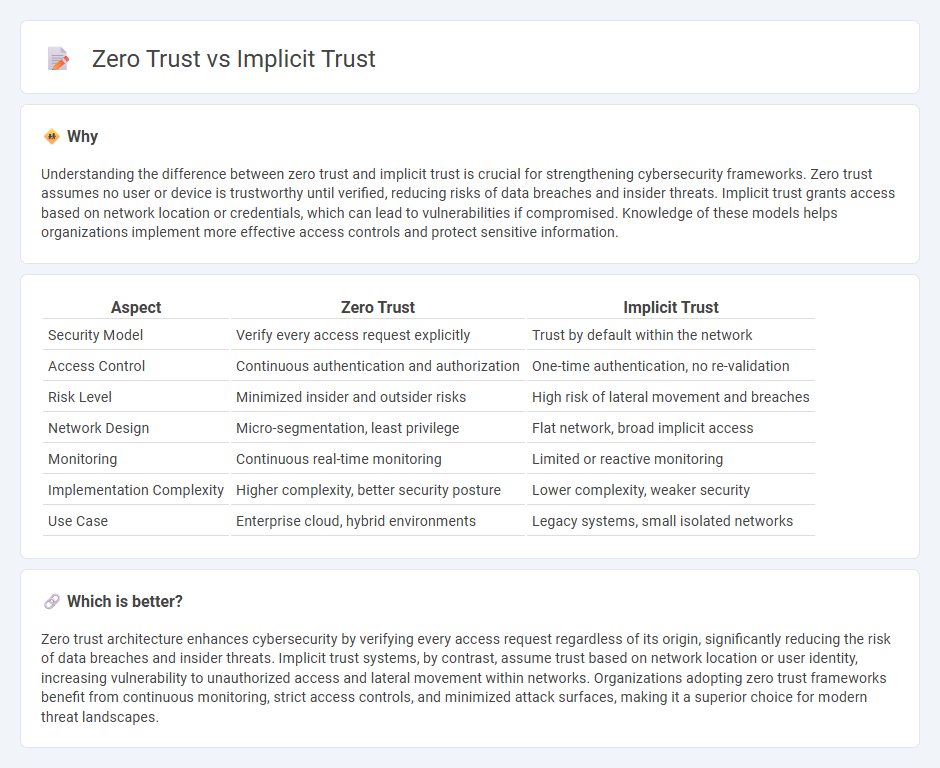
| Aspect | Zero Trust | Implicit Trust |
|---|---|---|
| Security Model | Verify every access request explicitly | Trust by default within the network |
| Access Control | Continuous authentication and authorization | One-time authentication, no re-validation |
| Risk Level | Minimized insider and outsider risks | High risk of lateral movement and breaches |
| Network Design | Micro-segmentation, least privilege | Flat network, broad implicit access |
| Monitoring | Continuous real-time monitoring | Limited or reactive monitoring |
| Implementation Complexity | Higher complexity, better security posture | Lower complexity, weaker security |
| Use Case | Enterprise cloud, hybrid environments | Legacy systems, small isolated networks |
Which is better?
Zero trust architecture enhances cybersecurity by verifying every access request regardless of its origin, significantly reducing the risk of data breaches and insider threats. Implicit trust systems, by contrast, assume trust based on network location or user identity, increasing vulnerability to unauthorized access and lateral movement within networks. Organizations adopting zero trust frameworks benefit from continuous monitoring, strict access controls, and minimized attack surfaces, making it a superior choice for modern threat landscapes.
Connection
Zero trust and implicit trust represent contrasting cybersecurity models; zero trust operates on the principle of "never trust, always verify," requiring continuous authentication and authorization for every access request. Implicit trust assumes users and devices within a network are trustworthy by default, relying heavily on perimeter defenses. The shift from implicit trust to zero trust architectures addresses modern threats by minimizing attack surfaces and enforcing strict access controls regardless of the user's location.
Key Terms
Authentication
Implicit trust relies on recognizing users by their credentials or device location without continuous verification, assuming a secure environment inside the network perimeter. Zero trust enforces strict identity verification through multi-factor authentication (MFA) and continuous monitoring regardless of network location, eliminating reliance on assumed trust. Explore how zero trust authentication strategies enhance security postures over implicit trust models for robust protection.
Access Control
Implicit trust models grant access based on assumed user legitimacy, often relying on network location or device credentials, which can expose systems to insider threats and lateral movement risks. Zero trust access control continuously verifies user identity, device health, and contextual factors before granting permission, implementing strict least-privilege principles to minimize attack surfaces. Explore in-depth comparisons of access control strategies to optimize cybersecurity frameworks.
Network Segmentation
Implicit trust networks rely on broad access privileges, often allowing lateral movement within the network, increasing security risks in the absence of effective network segmentation. Zero trust architecture enforces strict access controls by segmenting the network into micro-perimeters, ensuring that each user or device is continuously verified before granting access to critical resources. Explore further to understand how network segmentation transforms security postures from implicit trust vulnerabilities to robust zero trust defenses.
Source and External Links
Automatic Trust in Government and System Support | The Journal of... - Implicit trust is an unconscious, gut-level trust people have in government, largely unrelated to their explicit, self-reported distrust, and it influences public support for government actions in crises.
Implicit Trust vs Explicit Trust in Access Management - Keeper Security - Implicit trust in access management grants broad access by default within a system, assuming trust unless disproven, and is typically used for low-risk resources, unlike explicit trust which requires real-time approvals.
Implicit Trust vs. Explicit Trust in Access Management - StrongDM - Implicit trust functions like an open-door policy granting access based on system membership without continuous verification, contrasting with explicit trust which demands ongoing, explicit approvals for access.
 dowidth.com
dowidth.com