eBPF (extended Berkeley Packet Filter) enhances Linux kernel capabilities with dynamic, programmable event handling, while AppArmor provides security by enforcing mandatory access control through predefined policies. Both technologies improve system security and performance but operate at different layers and use cases within the Linux environment. Explore their unique features and benefits to determine which solution aligns best with your infrastructure needs.
Why it is important
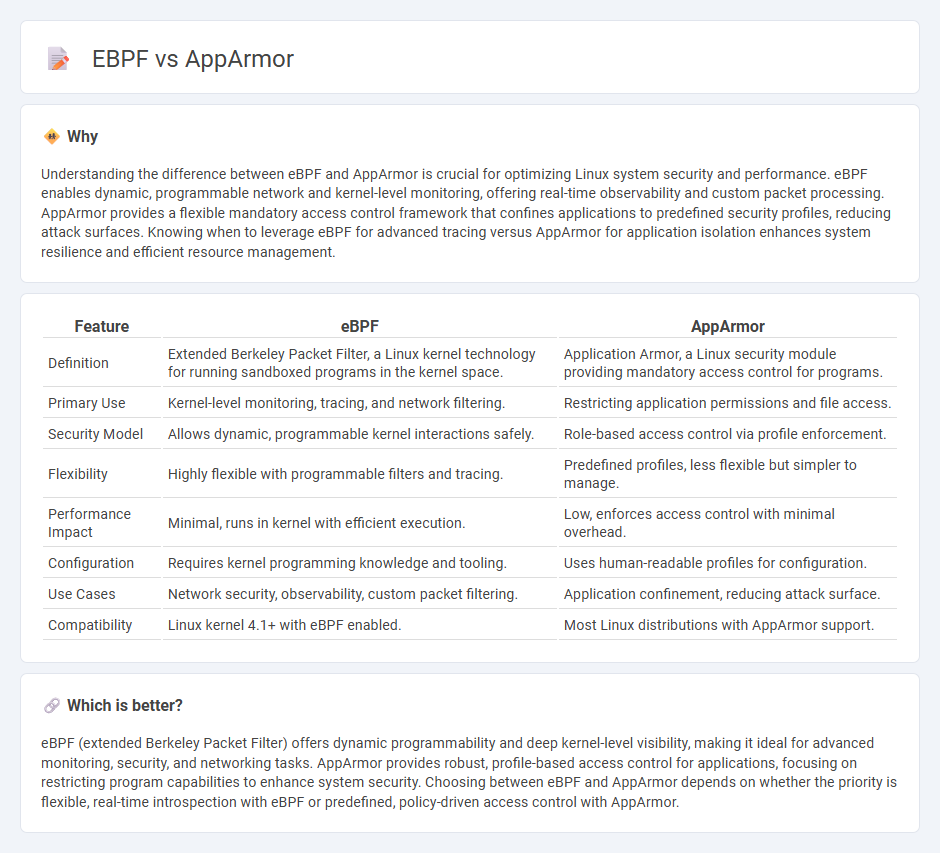
Understanding the difference between eBPF and AppArmor is crucial for optimizing Linux system security and performance. eBPF enables dynamic, programmable network and kernel-level monitoring, offering real-time observability and custom packet processing. AppArmor provides a flexible mandatory access control framework that confines applications to predefined security profiles, reducing attack surfaces. Knowing when to leverage eBPF for advanced tracing versus AppArmor for application isolation enhances system resilience and efficient resource management.
Comparison Table
| Feature | eBPF | AppArmor |
|---|---|---|
| Definition | Extended Berkeley Packet Filter, a Linux kernel technology for running sandboxed programs in the kernel space. | Application Armor, a Linux security module providing mandatory access control for programs. |
| Primary Use | Kernel-level monitoring, tracing, and network filtering. | Restricting application permissions and file access. |
| Security Model | Allows dynamic, programmable kernel interactions safely. | Role-based access control via profile enforcement. |
| Flexibility | Highly flexible with programmable filters and tracing. | Predefined profiles, less flexible but simpler to manage. |
| Performance Impact | Minimal, runs in kernel with efficient execution. | Low, enforces access control with minimal overhead. |
| Configuration | Requires kernel programming knowledge and tooling. | Uses human-readable profiles for configuration. |
| Use Cases | Network security, observability, custom packet filtering. | Application confinement, reducing attack surface. |
| Compatibility | Linux kernel 4.1+ with eBPF enabled. | Most Linux distributions with AppArmor support. |
Which is better?
eBPF (extended Berkeley Packet Filter) offers dynamic programmability and deep kernel-level visibility, making it ideal for advanced monitoring, security, and networking tasks. AppArmor provides robust, profile-based access control for applications, focusing on restricting program capabilities to enhance system security. Choosing between eBPF and AppArmor depends on whether the priority is flexible, real-time introspection with eBPF or predefined, policy-driven access control with AppArmor.
Connection
eBPF (extended Berkeley Packet Filter) enhances Linux kernel security by enabling dynamic tracing and filtering of system calls at runtime. AppArmor complements eBPF by providing mandatory access control policies that restrict application behaviors based on predefined profiles. Together, they create a robust security framework by leveraging eBPF's event-driven monitoring and AppArmor's fine-grained permission enforcement.
Key Terms
Mandatory Access Control (MAC)
AppArmor enforces Mandatory Access Control (MAC) by confining program capabilities with predefined security profiles, limiting file access and system calls based on application context. eBPF extends MAC by dynamically monitoring and filtering system events at the kernel level, providing fine-grained, programmable control over processes, network packets, and tracepoints. Discover more about how combining AppArmor's static policies with eBPF's dynamic capabilities enhances your system's security posture.
Kernel Security Modules (KSM)
AppArmor and eBPF both enhance kernel security but operate differently; AppArmor uses mandatory access control policies to restrict program capabilities, while eBPF enables dynamic and programmable tracing and filtering within the Linux kernel. Kernel Security Modules (KSM) like AppArmor enforce predefined security policies, whereas eBPF offers more flexible, fine-grained monitoring and real-time network security enforcement. Explore the nuances of these technologies to understand their impact on Linux kernel security frameworks.
In-kernel Programmability
AppArmor enhances Linux security by enforcing mandatory access control policies that restrict application capabilities at the kernel level, ensuring process isolation and reducing attack surfaces. eBPF (extended Berkeley Packet Filter) enables dynamic, programmable kernel instrumentation allowing custom monitoring, tracing, and security enforcement without the need for kernel module development or restarts. Discover how combining AppArmor's structured policy framework with eBPF's flexible in-kernel programmability can elevate system security and performance.
Source and External Links
AppArmor - Wikipedia - AppArmor is a Linux kernel security module providing mandatory access control (MAC) by restricting program capabilities with per-program profiles, based on file paths rather than labels, aiming to be easier to manage than SELinux.
AppArmor - Ubuntu Wiki - AppArmor confines programs to limited resources via profiles in enforcement or complain mode, binding access control to programs not users, and is included in the Linux kernel since version 2.6.36 as a MAC system.
AppArmor - ArchWiki - AppArmor supplements standard Linux discretionary access control by enforcing detailed per-application security policies based on file paths and providing logs and real-time violation alerts to proactively protect the system against threats.
 dowidth.com
dowidth.com