Zero Trust Architecture enforces strict identity verification for every device and user attempting to access resources, minimizing internal and external cybersecurity threats. Security Information and Event Management (SIEM) systems aggregate and analyze security data in real-time to detect anomalies and respond to incidents swiftly. Explore the distinctions and benefits of these approaches to enhance your cybersecurity strategy.
Why it is important
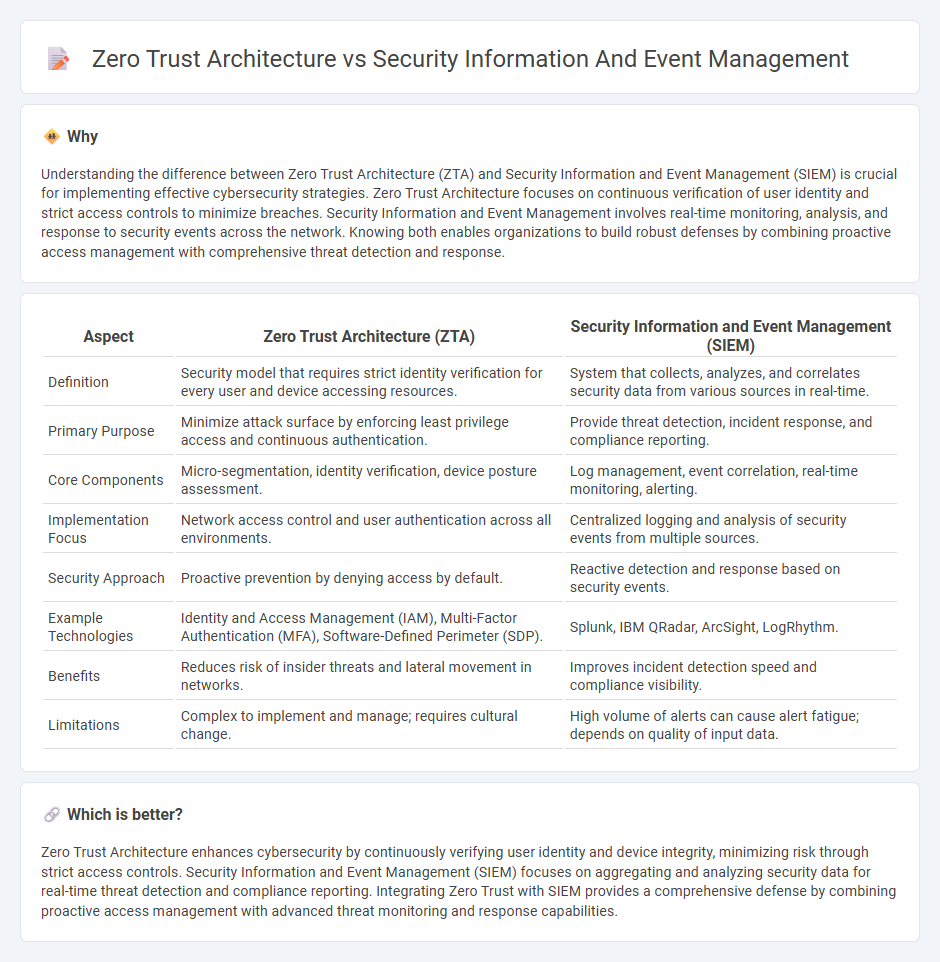
Understanding the difference between Zero Trust Architecture (ZTA) and Security Information and Event Management (SIEM) is crucial for implementing effective cybersecurity strategies. Zero Trust Architecture focuses on continuous verification of user identity and strict access controls to minimize breaches. Security Information and Event Management involves real-time monitoring, analysis, and response to security events across the network. Knowing both enables organizations to build robust defenses by combining proactive access management with comprehensive threat detection and response.
Comparison Table
| Aspect | Zero Trust Architecture (ZTA) | Security Information and Event Management (SIEM) |
|---|---|---|
| Definition | Security model that requires strict identity verification for every user and device accessing resources. | System that collects, analyzes, and correlates security data from various sources in real-time. |
| Primary Purpose | Minimize attack surface by enforcing least privilege access and continuous authentication. | Provide threat detection, incident response, and compliance reporting. |
| Core Components | Micro-segmentation, identity verification, device posture assessment. | Log management, event correlation, real-time monitoring, alerting. |
| Implementation Focus | Network access control and user authentication across all environments. | Centralized logging and analysis of security events from multiple sources. |
| Security Approach | Proactive prevention by denying access by default. | Reactive detection and response based on security events. |
| Example Technologies | Identity and Access Management (IAM), Multi-Factor Authentication (MFA), Software-Defined Perimeter (SDP). | Splunk, IBM QRadar, ArcSight, LogRhythm. |
| Benefits | Reduces risk of insider threats and lateral movement in networks. | Improves incident detection speed and compliance visibility. |
| Limitations | Complex to implement and manage; requires cultural change. | High volume of alerts can cause alert fatigue; depends on quality of input data. |
Which is better?
Zero Trust Architecture enhances cybersecurity by continuously verifying user identity and device integrity, minimizing risk through strict access controls. Security Information and Event Management (SIEM) focuses on aggregating and analyzing security data for real-time threat detection and compliance reporting. Integrating Zero Trust with SIEM provides a comprehensive defense by combining proactive access management with advanced threat monitoring and response capabilities.
Connection
Zero Trust Architecture enforces strict identity verification and least-privilege access across all network resources, generating extensive security data crucial for analysis. Security Information and Event Management (SIEM) systems collect, correlate, and analyze logs and events from Zero Trust components to detect anomalies and potential threats in real-time. The integration of Zero Trust with SIEM enhances proactive threat detection, incident response, and overall cybersecurity posture by leveraging comprehensive visibility and continuous monitoring.
Key Terms
**Security Information and Event Management (SIEM):**
Security Information and Event Management (SIEM) systems aggregate and analyze security data from across an organization's IT infrastructure to detect potential threats and compliance issues in real time. SIEM solutions provide centralized visibility, advanced threat detection, and automated incident response capabilities, enhancing an organization's ability to manage and mitigate security risks. Explore how integrating SIEM with Zero Trust Architecture strengthens overall security posture.
Log Aggregation
Security Information and Event Management (SIEM) systems centralize and analyze log data from diverse sources to detect threats and ensure compliance, while Zero Trust Architecture (ZTA) emphasizes strict access controls and continuous verification without inherently relying on log aggregation. SIEM enhances visibility by collecting, correlating, and normalizing logs for comprehensive security monitoring, whereas Zero Trust uses real-time authentication and micro-segmentation to minimize trust zones. Explore further to understand how integrating SIEM's log aggregation capabilities with Zero Trust's principles strengthens cybersecurity frameworks.
Real-time Monitoring
Security Information and Event Management (SIEM) provides real-time monitoring by aggregating and analyzing log data from various sources to detect potential threats and anomalies across an enterprise network. Zero Trust Architecture (ZTA) enhances this approach by enforcing strict access controls and continuous authentication, ensuring that every user and device is verified before gaining network entry, thus reducing the attack surface. Explore how combining SIEM's real-time insights with Zero Trust's stringent security policies can elevate your organization's defense strategy.
Source and External Links
Security Information and Event Management - Wikipedia - This page provides comprehensive information about SIEM, including its history, functions, and applications in enhancing security operations.
Security Information and Event Management (SIEM) Systems - IRS - This resource details the use of SIEM systems in managing security threats and ensuring compliance with regulatory requirements.
What is SIEM? - IBM - This webpage explains how SIEM solutions help organizations recognize and address security threats by analyzing event data across various IT infrastructure sources.
 dowidth.com
dowidth.com