Zero-knowledge proofs enable one party to prove knowledge of information without revealing the information itself, enhancing privacy in cryptographic protocols. Secure multiparty computation allows multiple parties to jointly compute a function over their inputs while keeping those inputs private, ensuring data confidentiality during collaborative processing. Explore further to understand the practical applications and differences between these cutting-edge cryptographic techniques.
Why it is important
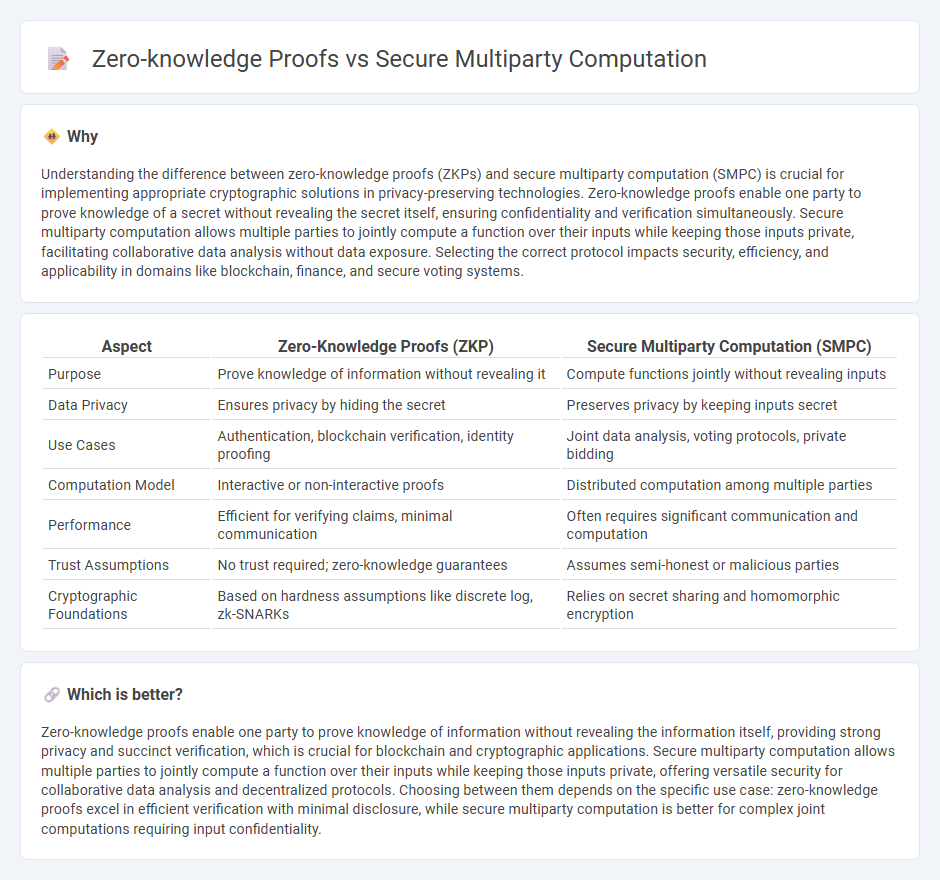
Understanding the difference between zero-knowledge proofs (ZKPs) and secure multiparty computation (SMPC) is crucial for implementing appropriate cryptographic solutions in privacy-preserving technologies. Zero-knowledge proofs enable one party to prove knowledge of a secret without revealing the secret itself, ensuring confidentiality and verification simultaneously. Secure multiparty computation allows multiple parties to jointly compute a function over their inputs while keeping those inputs private, facilitating collaborative data analysis without data exposure. Selecting the correct protocol impacts security, efficiency, and applicability in domains like blockchain, finance, and secure voting systems.
Comparison Table
| Aspect | Zero-Knowledge Proofs (ZKP) | Secure Multiparty Computation (SMPC) |
|---|---|---|
| Purpose | Prove knowledge of information without revealing it | Compute functions jointly without revealing inputs |
| Data Privacy | Ensures privacy by hiding the secret | Preserves privacy by keeping inputs secret |
| Use Cases | Authentication, blockchain verification, identity proofing | Joint data analysis, voting protocols, private bidding |
| Computation Model | Interactive or non-interactive proofs | Distributed computation among multiple parties |
| Performance | Efficient for verifying claims, minimal communication | Often requires significant communication and computation |
| Trust Assumptions | No trust required; zero-knowledge guarantees | Assumes semi-honest or malicious parties |
| Cryptographic Foundations | Based on hardness assumptions like discrete log, zk-SNARKs | Relies on secret sharing and homomorphic encryption |
Which is better?
Zero-knowledge proofs enable one party to prove knowledge of information without revealing the information itself, providing strong privacy and succinct verification, which is crucial for blockchain and cryptographic applications. Secure multiparty computation allows multiple parties to jointly compute a function over their inputs while keeping those inputs private, offering versatile security for collaborative data analysis and decentralized protocols. Choosing between them depends on the specific use case: zero-knowledge proofs excel in efficient verification with minimal disclosure, while secure multiparty computation is better for complex joint computations requiring input confidentiality.
Connection
Zero-knowledge proofs and secure multiparty computation both enhance privacy in cryptographic protocols by enabling verification without revealing underlying data. Zero-knowledge proofs allow one party to prove knowledge of a secret without disclosing it, while secure multiparty computation enables multiple parties to jointly compute a function over their inputs without sharing those inputs. Their synergy is crucial for privacy-preserving applications in blockchain, secure voting, and confidential data analysis.
Key Terms
Privacy
Secure multiparty computation allows multiple parties to jointly compute a function over their inputs without revealing those inputs to each other, ensuring data privacy during collaborative processes. Zero-knowledge proofs enable one party to prove knowledge of a secret without disclosing the secret itself, enhancing individual privacy in verification tasks. Explore the detailed differences and applications of these cryptographic techniques to better understand their roles in safeguarding privacy.
Computation Integrity
Secure multiparty computation (SMC) ensures computation integrity by enabling multiple parties to collaboratively compute a function over their inputs while keeping those inputs private and verifying the correctness of the output without trusting any single participant. Zero-knowledge proofs (ZKPs) provide computation integrity by allowing one party to prove to another that a computation was performed correctly without revealing any details about the input or the process. Explore deeper insights on how SMC and ZKPs maintain computation integrity in privacy-preserving cryptographic protocols.
Trust Assumptions
Secure multiparty computation (SMPC) enables multiple parties to jointly compute a function over their inputs while keeping those inputs private, relying on assumptions such as honest majority or threshold adversaries for security. Zero-knowledge proofs (ZKPs) allow one party to prove knowledge of a secret without revealing it, based on cryptographic hardness assumptions like discrete logarithms or elliptic curve problems. Explore how these trust assumptions impact real-world applications and security guarantees.
Source and External Links
What is Secure Multiparty Computation? - Secure Multiparty Computation (SMPC) is a cryptographic technique enabling secure computations on private data across multiple parties without revealing the original data itself.
What Is Multiparty Computation? - Multiparty computation allows multiple parties to jointly compute a function using their private data, ensuring each party's input remains confidential and only the final result is revealed.
Secure multi-party computation - Secure multi-party computation is a subfield of cryptography focused on developing protocols that let parties compute a joint function over their private inputs while keeping those inputs hidden from each other.
 dowidth.com
dowidth.com