Quantum key distribution leverages the principles of quantum mechanics to enable secure communication by detecting eavesdropping attempts on cryptographic keys. Lattice-based cryptography offers robust post-quantum security through complex mathematical structures resistant to attacks from quantum computers. Explore the latest advancements in quantum key distribution and lattice-based cryptographic methods to understand their impact on future cybersecurity.
Why it is important
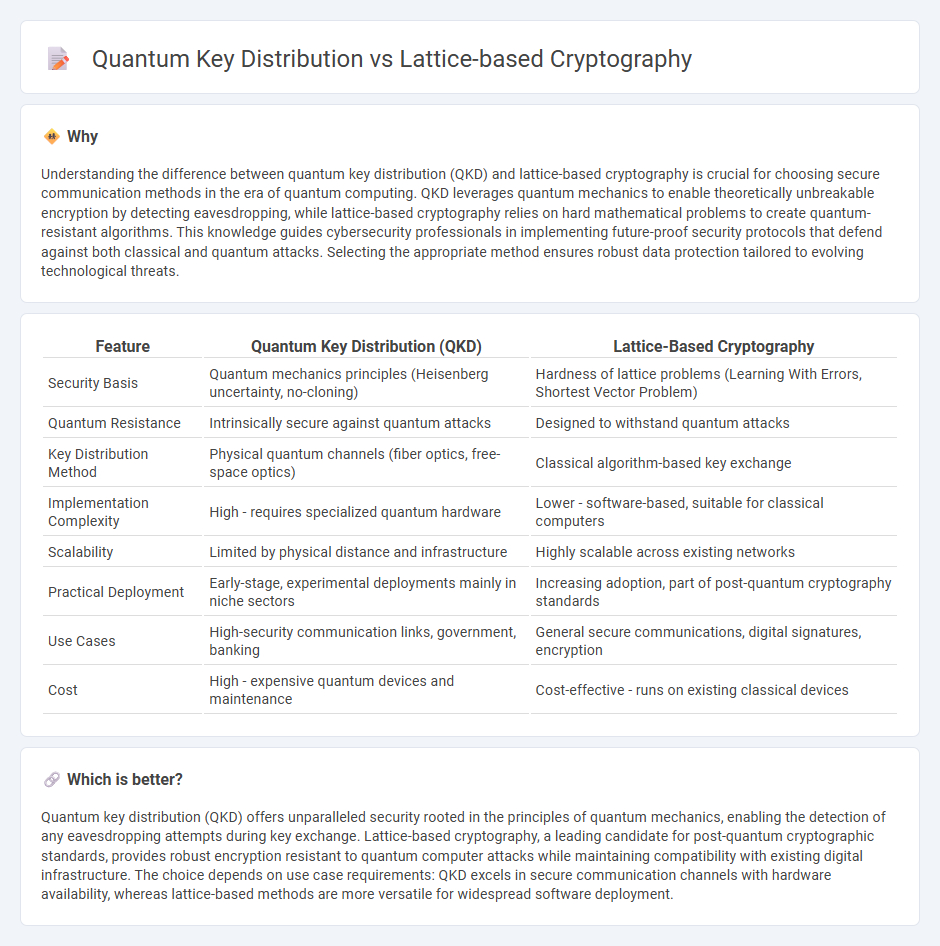
Understanding the difference between quantum key distribution (QKD) and lattice-based cryptography is crucial for choosing secure communication methods in the era of quantum computing. QKD leverages quantum mechanics to enable theoretically unbreakable encryption by detecting eavesdropping, while lattice-based cryptography relies on hard mathematical problems to create quantum-resistant algorithms. This knowledge guides cybersecurity professionals in implementing future-proof security protocols that defend against both classical and quantum attacks. Selecting the appropriate method ensures robust data protection tailored to evolving technological threats.
Comparison Table
| Feature | Quantum Key Distribution (QKD) | Lattice-Based Cryptography |
|---|---|---|
| Security Basis | Quantum mechanics principles (Heisenberg uncertainty, no-cloning) | Hardness of lattice problems (Learning With Errors, Shortest Vector Problem) |
| Quantum Resistance | Intrinsically secure against quantum attacks | Designed to withstand quantum attacks |
| Key Distribution Method | Physical quantum channels (fiber optics, free-space optics) | Classical algorithm-based key exchange |
| Implementation Complexity | High - requires specialized quantum hardware | Lower - software-based, suitable for classical computers |
| Scalability | Limited by physical distance and infrastructure | Highly scalable across existing networks |
| Practical Deployment | Early-stage, experimental deployments mainly in niche sectors | Increasing adoption, part of post-quantum cryptography standards |
| Use Cases | High-security communication links, government, banking | General secure communications, digital signatures, encryption |
| Cost | High - expensive quantum devices and maintenance | Cost-effective - runs on existing classical devices |
Which is better?
Quantum key distribution (QKD) offers unparalleled security rooted in the principles of quantum mechanics, enabling the detection of any eavesdropping attempts during key exchange. Lattice-based cryptography, a leading candidate for post-quantum cryptographic standards, provides robust encryption resistant to quantum computer attacks while maintaining compatibility with existing digital infrastructure. The choice depends on use case requirements: QKD excels in secure communication channels with hardware availability, whereas lattice-based methods are more versatile for widespread software deployment.
Connection
Quantum key distribution (QKD) leverages principles of quantum mechanics to enable secure communication by generating encryption keys that are theoretically immune to eavesdropping. Lattice-based cryptography provides a classical post-quantum cryptographic approach designed to withstand attacks from quantum computers by relying on the hardness of lattice problems. Both technologies are interconnected in the broader effort to achieve quantum-resistant security, with QKD offering secure key exchange and lattice-based methods securing data against future quantum threats.
Key Terms
Hardness Assumptions (Lattice Problems)
Lattice-based cryptography relies on the hardness of mathematical problems such as the Shortest Vector Problem (SVP) and Learning With Errors (LWE), which remain resistant to attacks even by quantum computers, offering scalable and efficient post-quantum security. Quantum key distribution (QKD), on the other hand, depends on the fundamental principles of quantum mechanics rather than computational hardness assumptions, providing theoretically unconditional security through quantum states transmission. Explore the distinctions and potential applications of these approaches to enhance your understanding of post-quantum cryptography.
Quantum Entanglement
Lattice-based cryptography offers post-quantum security by relying on hard mathematical problems resistant to quantum attacks, contrasting with quantum key distribution (QKD) that uses quantum entanglement to detect eavesdropping via the principles of quantum mechanics. Quantum entanglement in QKD ensures secure communication by generating correlated key pairs that are impossible to intercept without altering the quantum state, providing theoretical unconditional security. Explore more on how quantum entanglement shapes next-generation cryptographic protocols and their implications for secure communications.
Post-Quantum Security
Lattice-based cryptography offers a scalable and practical approach to post-quantum security by leveraging complex mathematical structures resistant to quantum attacks, unlike quantum key distribution which relies on the principles of quantum mechanics for secure key exchange. The National Institute of Standards and Technology (NIST) actively promotes lattice-based schemes as finalists in its Post-Quantum Cryptography standardization process due to their efficiency and compatibility with existing digital infrastructure. Explore deeper into the evolving landscape of quantum-resistant cryptographic solutions to safeguard future digital communications.
Source and External Links
What is Lattice based Cryptography? - Glossary - Training Camp - Lattice-based cryptography is a form of encryption relying on complex lattice math that remains secure even against quantum computing, using hard mathematical problems in high-dimensional lattice structures to enable quantum-resistant cryptographic schemes like NTRU and Falcon.
Post-quantum cryptography: Lattice-based cryptography - Red Hat - Lattice-based cryptography uses hard problems in spaces formed by vector combinations (lattices), providing a fundamental approach for secure cryptography that is resistant to known quantum computer attacks.
Lattice-based cryptography - Wikipedia - Lattice-based cryptography encompasses various cryptographic primitives built on lattice problems such as NTRUEncrypt for encryption and CRYSTALS-Kyber for key exchange, being central in the NIST post-quantum standardization effort.
 dowidth.com
dowidth.com