Digital forensics consulting specializes in uncovering and analyzing digital evidence from cyber incidents to support legal cases and internal investigations. Cybersecurity consulting focuses on protecting IT infrastructure by identifying vulnerabilities, developing security policies, and implementing threat mitigation strategies. Explore our comprehensive consulting services to strengthen your organization's cyber defense and forensic capabilities.
Why it is important
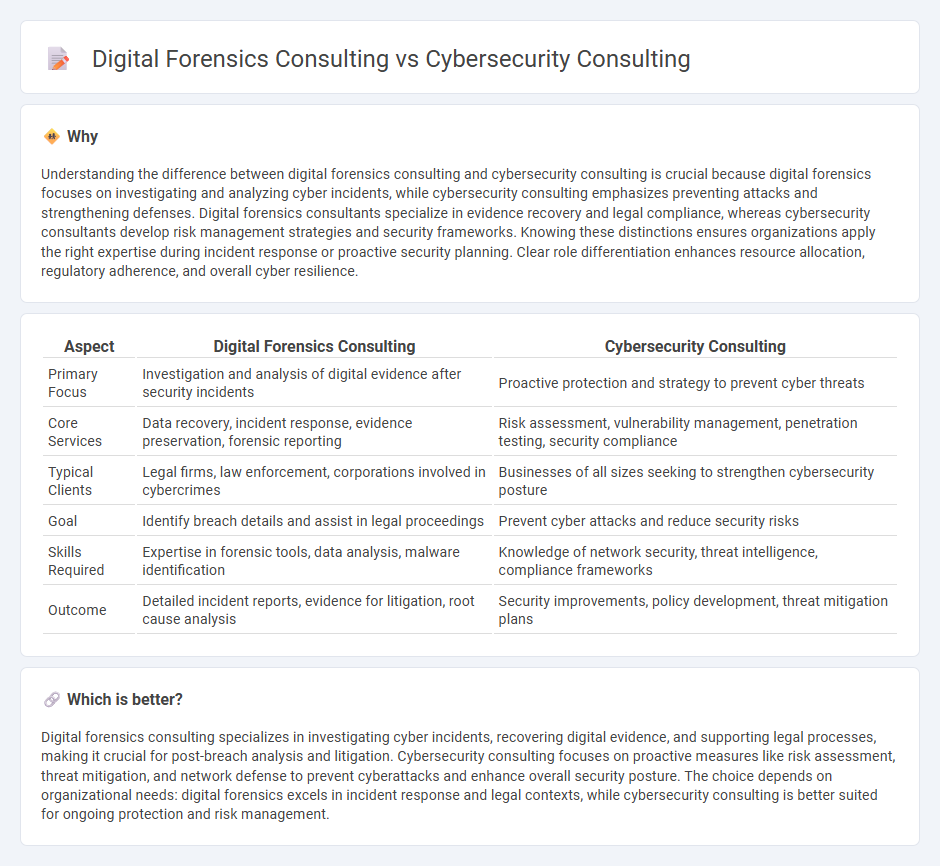
Understanding the difference between digital forensics consulting and cybersecurity consulting is crucial because digital forensics focuses on investigating and analyzing cyber incidents, while cybersecurity consulting emphasizes preventing attacks and strengthening defenses. Digital forensics consultants specialize in evidence recovery and legal compliance, whereas cybersecurity consultants develop risk management strategies and security frameworks. Knowing these distinctions ensures organizations apply the right expertise during incident response or proactive security planning. Clear role differentiation enhances resource allocation, regulatory adherence, and overall cyber resilience.
Comparison Table
| Aspect | Digital Forensics Consulting | Cybersecurity Consulting |
|---|---|---|
| Primary Focus | Investigation and analysis of digital evidence after security incidents | Proactive protection and strategy to prevent cyber threats |
| Core Services | Data recovery, incident response, evidence preservation, forensic reporting | Risk assessment, vulnerability management, penetration testing, security compliance |
| Typical Clients | Legal firms, law enforcement, corporations involved in cybercrimes | Businesses of all sizes seeking to strengthen cybersecurity posture |
| Goal | Identify breach details and assist in legal proceedings | Prevent cyber attacks and reduce security risks |
| Skills Required | Expertise in forensic tools, data analysis, malware identification | Knowledge of network security, threat intelligence, compliance frameworks |
| Outcome | Detailed incident reports, evidence for litigation, root cause analysis | Security improvements, policy development, threat mitigation plans |
Which is better?
Digital forensics consulting specializes in investigating cyber incidents, recovering digital evidence, and supporting legal processes, making it crucial for post-breach analysis and litigation. Cybersecurity consulting focuses on proactive measures like risk assessment, threat mitigation, and network defense to prevent cyberattacks and enhance overall security posture. The choice depends on organizational needs: digital forensics excels in incident response and legal contexts, while cybersecurity consulting is better suited for ongoing protection and risk management.
Connection
Digital forensics consulting and cybersecurity consulting are interconnected through their shared focus on protecting organizations from cyber threats and investigating security breaches. Digital forensics consulting involves the identification, preservation, and analysis of digital evidence to trace cyberattacks, while cybersecurity consulting emphasizes the implementation of proactive measures to prevent data breaches and enhance overall system security. Together, they provide a comprehensive approach to risk management by combining incident response with preventative cybersecurity strategies.
Key Terms
Risk Assessment (Cybersecurity consulting)
Cybersecurity consulting emphasizes comprehensive risk assessment to identify, evaluate, and mitigate potential vulnerabilities within an organization's IT infrastructure, ensuring robust protection against cyber threats. This process involves detailed analysis of network security, compliance with industry standards, and implementation of strategic safeguards to reduce the likelihood of data breaches or cyberattacks. Explore more about how specialized risk assessment in cybersecurity consulting can fortify your organization's defense mechanisms.
Incident Response (Digital forensics consulting)
Cybersecurity consulting focuses on proactive strategies to prevent, detect, and mitigate cyber threats, while digital forensics consulting specializes in incident response by investigating and analyzing security breaches to identify the attack's origin and impact. Digital forensics experts collect and preserve digital evidence, enabling legal proceedings and aiding in recovery efforts after a cyber incident. Discover how digital forensics consulting enhances incident response and organizational resilience.
Compliance Management (Cybersecurity consulting)
Cybersecurity consulting emphasizes Compliance Management by ensuring organizations adhere to industry standards such as ISO 27001, NIST, and GDPR, minimizing legal and financial risks. Consultants perform risk assessments, implement security policies, and guide companies through regulatory audits to maintain continuous compliance. Explore how expert cybersecurity consulting can strengthen your compliance framework and protect your business.
Source and External Links
Cyber Security Consulting - IT Security Consulting | Risk Management - CyberSecOp offers comprehensive cybersecurity consulting services, including virtual CISO support, risk management, incident response, compliance reporting, and tailored security roadmaps for multiple industries worldwide.
Cybersecurity Consulting Services & Jobs - ALKU - ALKU provides specialized cybersecurity consulting that helps businesses proactively identify vulnerabilities, conduct risk assessments, manage incident response, and ensure ongoing security tailored to organizational needs.
Atlanta Cyber Security Services | Suwanee Cybersecurity Consulting - Integricom delivers expert cybersecurity consulting focusing on protection of hardware, software, and data through services like security awareness training, vulnerability management, compliance, and risk management to safeguard businesses against cyber threats.
 dowidth.com
dowidth.com