Algorithmic bias consulting focuses on identifying and mitigating biases in AI models to ensure fairness, transparency, and ethical decision-making across industries such as finance, healthcare, and recruitment. Cybersecurity consulting centers on protecting digital assets through risk assessment, threat detection, and implementing security protocols to defend against cyberattacks and data breaches. Explore how these specialized consulting fields address unique challenges in technology-driven environments.
Why it is important
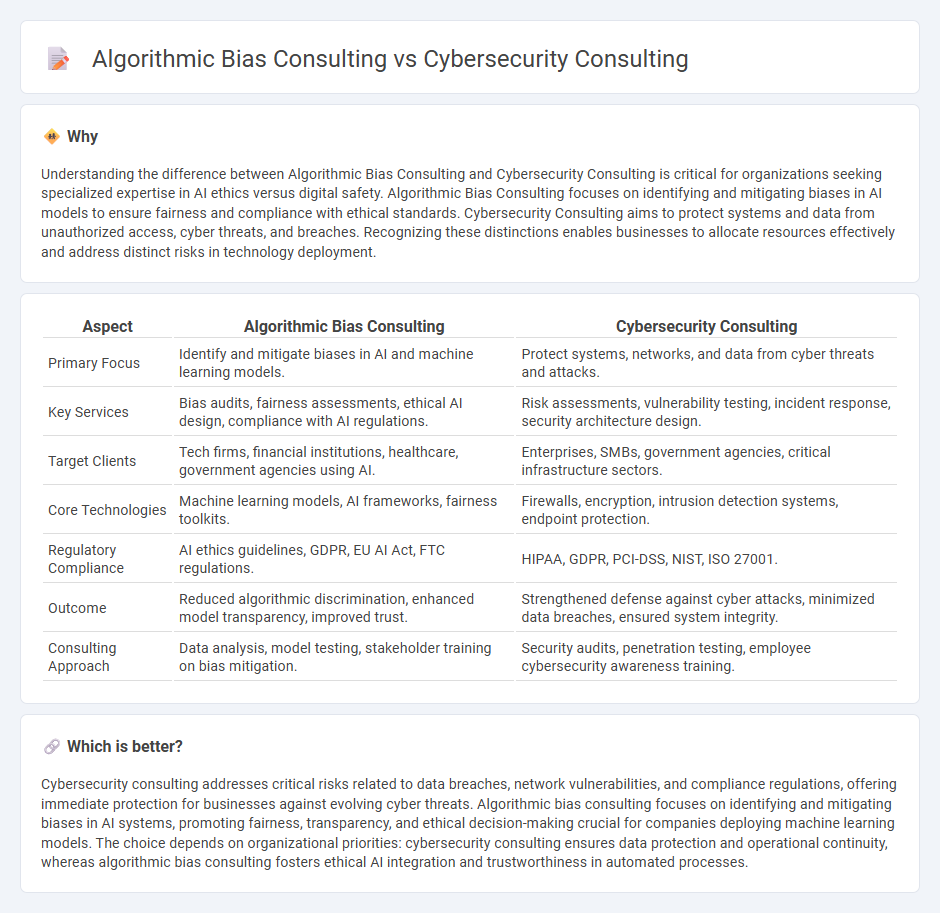
Understanding the difference between Algorithmic Bias Consulting and Cybersecurity Consulting is critical for organizations seeking specialized expertise in AI ethics versus digital safety. Algorithmic Bias Consulting focuses on identifying and mitigating biases in AI models to ensure fairness and compliance with ethical standards. Cybersecurity Consulting aims to protect systems and data from unauthorized access, cyber threats, and breaches. Recognizing these distinctions enables businesses to allocate resources effectively and address distinct risks in technology deployment.
Comparison Table
| Aspect | Algorithmic Bias Consulting | Cybersecurity Consulting |
|---|---|---|
| Primary Focus | Identify and mitigate biases in AI and machine learning models. | Protect systems, networks, and data from cyber threats and attacks. |
| Key Services | Bias audits, fairness assessments, ethical AI design, compliance with AI regulations. | Risk assessments, vulnerability testing, incident response, security architecture design. |
| Target Clients | Tech firms, financial institutions, healthcare, government agencies using AI. | Enterprises, SMBs, government agencies, critical infrastructure sectors. |
| Core Technologies | Machine learning models, AI frameworks, fairness toolkits. | Firewalls, encryption, intrusion detection systems, endpoint protection. |
| Regulatory Compliance | AI ethics guidelines, GDPR, EU AI Act, FTC regulations. | HIPAA, GDPR, PCI-DSS, NIST, ISO 27001. |
| Outcome | Reduced algorithmic discrimination, enhanced model transparency, improved trust. | Strengthened defense against cyber attacks, minimized data breaches, ensured system integrity. |
| Consulting Approach | Data analysis, model testing, stakeholder training on bias mitigation. | Security audits, penetration testing, employee cybersecurity awareness training. |
Which is better?
Cybersecurity consulting addresses critical risks related to data breaches, network vulnerabilities, and compliance regulations, offering immediate protection for businesses against evolving cyber threats. Algorithmic bias consulting focuses on identifying and mitigating biases in AI systems, promoting fairness, transparency, and ethical decision-making crucial for companies deploying machine learning models. The choice depends on organizational priorities: cybersecurity consulting ensures data protection and operational continuity, whereas algorithmic bias consulting fosters ethical AI integration and trustworthiness in automated processes.
Connection
Algorithmic bias consulting and cybersecurity consulting intersect in addressing the risks of biased algorithms that can create security vulnerabilities or exploit sensitive data. Both fields focus on ensuring robust, fair, and secure AI systems by identifying and mitigating biases that could lead to unauthorized access or data breaches. Integrating algorithmic bias assessments with cybersecurity protocols enhances overall system integrity and compliance with ethical and legal standards.
Key Terms
**Cybersecurity consulting:**
Cybersecurity consulting specializes in protecting organizations from cyber threats by assessing vulnerabilities, implementing robust security measures, and ensuring compliance with industry standards such as NIST and ISO 27001. Experts analyze network infrastructures, develop incident response strategies, and deploy advanced technologies like encryption and multi-factor authentication to safeguard sensitive data. To explore how cybersecurity consulting can fortify your business against evolving cyber risks, discover more detailed insights and tailored solutions.
Risk Assessment
Cybersecurity consulting emphasizes comprehensive risk assessment by identifying vulnerabilities, threat vectors, and potential breaches to safeguard digital infrastructure and sensitive data. Algorithmic bias consulting focuses on evaluating AI models and datasets for discriminatory patterns, ensuring fairness and compliance with ethical standards in automated decision-making systems. Explore in-depth insights on risk assessment approaches in both fields to strengthen organizational resilience and ethical AI implementation.
Penetration Testing
Penetration testing in cybersecurity consulting involves simulating cyberattacks to identify vulnerabilities in networks and systems, ensuring robust protection against data breaches and unauthorized access. In algorithmic bias consulting, penetration testing shifts focus to evaluating AI models and data pipelines for biases that could lead to unfair or discriminatory outcomes. Explore deeper into how penetration testing techniques differ across these consulting areas to enhance security and fairness in technology.
Source and External Links
Cyber Security Consulting - IT Security Consulting | Risk Management - CyberSecOp offers comprehensive cybersecurity consulting services including risk assessment, incident response, strategy development, and compliance support across multiple industries with services like Virtual CISO programs and cybersecurity strategy governance tailored to organizational needs.
What Is a Cybersecurity Consultant? (And How to Become One) - Cybersecurity consultants identify vulnerabilities, assess risks, and implement solutions to defend against cyber threats; they require technical skills in ethical hacking, programming, and communication, and can work in-house, freelance, or for consulting firms.
Best Security Consulting Services, Worldwide Reviews 2025 - Gartner - Security consulting firms provide advisory services for IT and information security management, offering expertise in program development, threat detection, digital forensics, and incident response to help organizations maintain security readiness and resilience.
 dowidth.com
dowidth.com