Digital twin strategy leverages real-time data and simulation models to optimize operational efficiency and predictive maintenance across industries. Cybersecurity strategy focuses on protecting digital assets and networks from cyber threats by implementing robust defense mechanisms and risk management protocols. Explore how integrating these strategies enhances innovation and security in your business.
Why it is important
Understanding the difference between digital twin strategy and cybersecurity strategy is crucial because digital twins focus on replicating physical assets for simulation and optimization, while cybersecurity strategies protect digital infrastructure from cyber threats. A well-defined digital twin strategy enables effective monitoring, predictive maintenance, and operational efficiency across industries like manufacturing and smart cities. Cybersecurity strategy is essential to safeguard sensitive data, ensure system integrity, and prevent financial losses or reputational damage. Confusing the two can lead to inadequate protection or missed opportunities for innovation and risk management.
Comparison Table
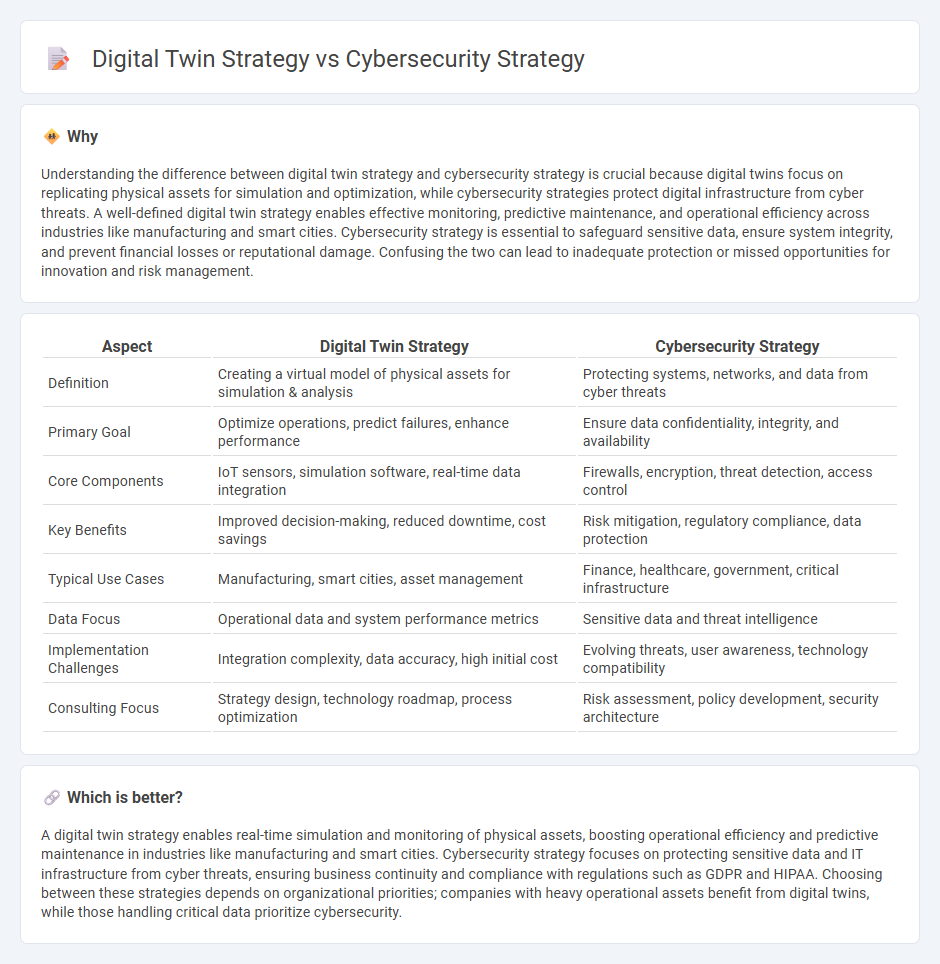
| Aspect | Digital Twin Strategy | Cybersecurity Strategy |
|---|---|---|
| Definition | Creating a virtual model of physical assets for simulation & analysis | Protecting systems, networks, and data from cyber threats |
| Primary Goal | Optimize operations, predict failures, enhance performance | Ensure data confidentiality, integrity, and availability |
| Core Components | IoT sensors, simulation software, real-time data integration | Firewalls, encryption, threat detection, access control |
| Key Benefits | Improved decision-making, reduced downtime, cost savings | Risk mitigation, regulatory compliance, data protection |
| Typical Use Cases | Manufacturing, smart cities, asset management | Finance, healthcare, government, critical infrastructure |
| Data Focus | Operational data and system performance metrics | Sensitive data and threat intelligence |
| Implementation Challenges | Integration complexity, data accuracy, high initial cost | Evolving threats, user awareness, technology compatibility |
| Consulting Focus | Strategy design, technology roadmap, process optimization | Risk assessment, policy development, security architecture |
Which is better?
A digital twin strategy enables real-time simulation and monitoring of physical assets, boosting operational efficiency and predictive maintenance in industries like manufacturing and smart cities. Cybersecurity strategy focuses on protecting sensitive data and IT infrastructure from cyber threats, ensuring business continuity and compliance with regulations such as GDPR and HIPAA. Choosing between these strategies depends on organizational priorities; companies with heavy operational assets benefit from digital twins, while those handling critical data prioritize cybersecurity.
Connection
Digital twin strategy and cybersecurity strategy are interconnected through their focus on protecting digital replicas of physical assets, systems, or processes from cyber threats. Implementing robust cybersecurity measures safeguards the integrity, availability, and confidentiality of real-time data within digital twins, ensuring accurate simulations and analytics. Effective cybersecurity strategies prevent unauthorized access and data breaches, which are critical for maintaining trust and operational efficiency in digital twin applications.
Key Terms
Risk Assessment
Cybersecurity strategy prioritizes identifying, evaluating, and mitigating digital threats to protect data integrity, confidentiality, and availability. Digital twin strategy emphasizes risk assessment by simulating real-world processes to predict vulnerabilities and optimize system resilience in complex environments. Explore comprehensive approaches to enhance your organization's security and operational efficiency.
Data Integration
A cybersecurity strategy prioritizes safeguarding data through encryption, threat detection, and access control, ensuring integrity and confidentiality across digital assets. In contrast, a digital twin strategy emphasizes seamless data integration from IoT devices, sensors, and real-time analytics to create accurate virtual models of physical systems. Explore how aligning these strategies enhances both security and operational efficiency in interconnected environments.
Threat Modeling
Threat modeling in cybersecurity strategy emphasizes identifying, evaluating, and mitigating potential risks to digital assets, networks, and systems by simulating attack vectors and adversary behaviors. In contrast, digital twin strategy integrates threat modeling within virtual replicas of physical systems to predict vulnerabilities and optimize real-time defense mechanisms through continuous data analysis. Explore how combining threat modeling with digital twin technologies enhances proactive cybersecurity measures.
Source and External Links
CISA Cybersecurity Strategic Plan - The FY2024-2026 plan by CISA focuses on collaboration, innovation, and accountability with three goals: addressing immediate threats, hardening the terrain, and driving security at scale through secure-by-design technology and measurable outcomes in cyber risk reduction.
How To Plan & Develop An Effective Cybersecurity Strategy - A robust cybersecurity strategy involves 8 steps including risk assessment, setting goals, evaluating technology, selecting frameworks, policy review, risk management planning, implementation, and continuous evaluation to protect against internal and external threats.
National Cybersecurity Strategy | ONCD | The White House - The 2023 National Cybersecurity Strategy emphasizes rebalancing responsibility towards capable organizations and realigning incentives to promote long-term investments, ensuring a secure digital ecosystem with public-private collaboration at its core.
 dowidth.com
dowidth.com